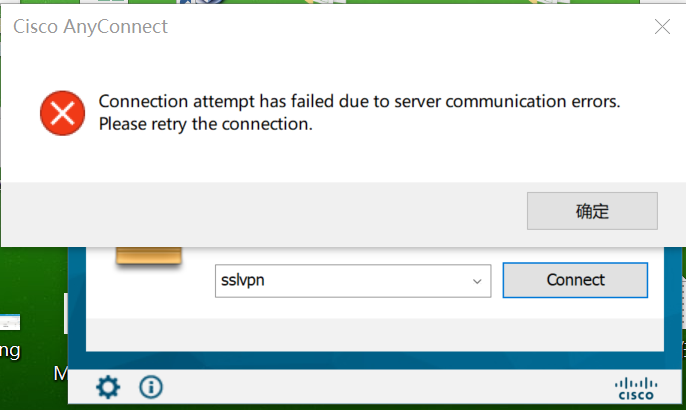
Anyconnect 更新到4.9、 4.10 登录失败,原4.7正常。
则是啥原因,4.9 4.10 都连接失败 换回4.7 则没有问题,有意思的是WEB可以连接SSLVPN 但自动连接两次才正常,IPSEC IKE2的WEB连接也不行。
Anyconnect 认证模式AAA+证书方式
- 标签:
-
VPN 和 AnyConnect
根本原因应该还是加密算法不再受支持的问题(图2)
4.9之后的版本不再支持一些不安全的加密算法。具体可以参考下面的链接:
解决办法:对于sslvpn,最好保证使用TLSv1.2,保证ssl cipher不包含不支持的加密套件,检查dh group配置 可以通过show run ssl来验证(至少放弃使用SSLv3);对于ipsec,检查是否存在DES、3DES MD5等相关的配置,如果存在建议升级至加密基本更高的设置。替换不支持的DH group 设置。
show ver
Cisco Adaptive Security Appliance Software Version 9.1(7)23
Device Manager Version 7.12(1)
Compiled on Thu 01-Feb-18 23:08 by builders
System image file is "disk0:/asa917-23-k8.bin"
SSLVPN在网页可以登录认证通过,客户端则提示证书问题。
webvpn 相关配置
crypto ipsec ikev2 ipsec-proposal secure
protocol esp encryption aes-256 aes-192 aes 3des des
protocol esp integrity sha-1
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map DYN 1 set ikev2 ipsec-proposal secure
crypto map STATIC 65535 ipsec-isakmp dynamic DYN
crypto map STATIC interface outside
crypto ca trustpoint Win2019-CA
enrollment terminal
crl configure
crypto ca trustpoint WIN2019-IC
enrollment terminal
fqdn asa.abcdczfh.com
subject-name CN=China
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
fqdn asa.abcdczfh.com
subject-name CN=asa
crl configure
crypto ca trustpool policy
crypto ca certificate chain Win2019-CA
certificate ca 1bbf7ef4f09aaf8642e4c90d02150dc0
略
quit
crypto ca certificate chain WIN2019-IC
certificate 720000001ddb4732ec625fbc1b00000000001d
quit
crypto ca certificate chain ASDM_TrustPoint0
certificate ca 718653f04941f99241f982b1c1116c95
略
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate 690000000a9635c0364045d06500000000000a
略
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint ASDM_TrustPoint1
!
telnet timeout 1400
ssh stricthostkeycheck
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 5
management-access inside
threat-detection basic-threat
threat-detection statistics
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
ntp server 10.144.46.33
ssl encryption 3des-sha1 aes128-sha1 aes256-sha1 dhe-aes128-sha1 dhe-aes256-sha1 des-sha1 rc4-sha1 rc4-md5
ssl trust-point ASDM_TrustPoint1 dianxin
ssl trust-point ASDM_TrustPoint1 inside
ssl trust-point ASDM_TrustPoint1 outside
ssl trust-point ASDM_TrustPoint1 WaiWang
webvpn
port 12340
enable outside
anyconnect image disk0:/anyconnect-win-4.8.03052-webdeploy-k9.pkg 1
anyconnect profiles ABCD-VPN disk0:/ABCD-vpn.xml
anyconnect enable
tunnel-group-list enable
cache
disable
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 ikev2 l2tp-ipsec
group-policy ABCDpolicy internal
group-policy ABCDpolicy attributes
wins-server none
dns-server none
vpn-tunnel-protocol ikev2 ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Vpnclient_splitTunnelAcl
default-domain none
address-pools value SSLClientPool
webvpn
anyconnect modules value dart
anyconnect profiles value ABCD-VPN type user
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group Both-Pass type remote-access
tunnel-group Both-Pass general-attributes
address-pool SSLClientPool
authentication-server-group acs
default-group-policy ABCDpolicy
tunnel-group Both-Pass webvpn-attributes
authentication aaa certificate
group-alias Abcd enable
!
在demo环境上搞了俩钟头,基本是能复现这个问题了。先说解决办法:
1. 4.9版本之后需要使用更高安全性的dh算法及加密算法,需要依赖AnyConnect Premium license。没有这个licenses,基本算是无解了,配置ikev2的时候会直接报错:
Username:Unknown An IKEv2 remote access connection failed. Attempting to use an NSA Suite B crypto algorithm (ECDH group) without an AnyConnect Premium license.
2. 有了premium license之后 webvpn需要配置"no anyconnect-essentials"
3. 更改ikev2 policy 的DH group
crypto ikev2 policy 1 encryption aes-256 integrity sha group 19 21 <---------如果anyconnect版本高于4.8请避免使用group 2 5 14 24 prf sha lifetime seconds 86400 !
4.(可选配置): 更改"crypto ipsec ikev2 ipsec-proposal"中的设置
将加密算法中des/3des更改为 aes或者更高级别的
将 完整性检查更改为sha-1或者更高级别的算法 //如果想将完成新检查的算法更改为高于sha-1时,仍旧需要满足Premium license的要求,不然anyconnect仍旧连接不成功 (Username:xxxx An IPsec remote access connection failed. Attempting to use an NSA Suite B crypto algorithm (SHA-2 integrity) without an AnyConnect Premium license.)
基本上确保license 正常,更改dh group即可解决问题:
附部分配置:
ASA(config)# sh run webvpn webvpn enable outside no anyconnect-essentials <== anyconnect image disk0:/anyconnect-win-4.3.02039-k9.pkg 1 anyconnect profiles sslvpn_client_profile disk0:/sslvpn_client_profile.xml anyconnect enable tunnel-group-list enable cache disable ASA(config)# sh run crypto ikev2 crypto ikev2 policy 1 <== encryption aes-256 integrity sha group 19 <== prf sha lifetime seconds 86400 crypto ikev2 policy 10 encryption aes-192 integrity sha group 19 21 <== prf sha lifetime seconds 86400 crypto ikev2 policy 20 encryption aes integrity sha group 19 21 prf sha lifetime seconds 86400 crypto ikev2 policy 30 encryption 3des integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 policy 40 encryption des integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 enable outside client-services port 443 crypto ikev2 remote-access trustpoint dc1_trust ASA(config)# sh run crypto ipsec crypto ipsec ikev2 ipsec-proposal DES protocol esp encryption des protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal 3DES protocol esp encryption 3des protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal AES protocol esp encryption aes protocol esp integrity sha-1 crypto ipsec ikev2 ipsec-proposal AES192 protocol esp encryption aes-192 protocol esp integrity sha-256 sha-1 crypto ipsec ikev2 ipsec-proposal AES256 protocol esp encryption aes-256 protocol esp integrity sha-256 sha-1 <== crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
------------------------------------------------------------------------------
更新1:
与asa os版本关系不大,asa9.1.x asa9.12.x 仅更改ikev2 policy DH group即可解决问题。
anyconnect4.9.04053 anyconnect 4.10.01075 两个版本测试均正常
我咨询的问题是 SSLVPN 与证书,不是IKE2啊。如不用证书,4.9 4.10 客户端原来配置都可以正常登录。
ASA5510(config-webvpn)# no anyconnect-essentials
ERROR: Command requires AnyConnect Essentials license 没有这个许可?
ASA5510(config-webvpn)#
ASA5510(config)# crypto ipsec ikev2 ipsec-proposal AES256
ASA5510(config-ipsec-proposal)# protocol esp encryption aes-256
ASA5510(config-ipsec-proposal)# protocol esp integrity sha-256 sha-1
^
ERROR: % Invalid input detected at '^' marker.
WaiWang-ASA5510(config-ipsec-proposal)# protocol esp integrity ?
ipsec-proposal mode commands/options:
md5 set hash md5
null set hash null
sha-1 set hash sha-1
WaiWang-ASA5510(config-ipsec-proposal)# protocol esp integrity 没有 sha-256 相关参数
Hardware: ASA5510, 1024 MB RAM, CPU Pentium 4 Celeron 1600 MHz,
Internal ATA Compact Flash, 256MB
BIOS Flash M50FW016 @ 0xfff00000, 2048KB
Encryption hardware device : Cisco ASA-55xx on-board accelerator (revision 0x0)
Boot microcode : CN1000-MC-BOOT-2.00
SSL/IKE microcode : CNlite-MC-SSLm-PLUS-2.08
IPSec microcode : CNlite-MC-IPSECm-MAIN-2.09
Number of accelerators: 1
0: Ext: Ethernet0/0 : address is 5057.a898.5554, irq 9
1: Ext: Ethernet0/1 : address is 5057.a898.5555, irq 9
2: Ext: Ethernet0/2 : address is 5057.a898.5556, irq 9
3: Ext: Ethernet0/3 : address is 5057.a898.5557, irq 9
4: Ext: Management0/0 : address is 5057.a898.5558, irq 11
5: Int: Not used : irq 11
6: Int: Not used : irq 5
Licensed features for this platform:
Maximum Physical Interfaces : Unlimited perpetual
Maximum VLANs : 100 perpetual
Inside Hosts : Unlimited perpetual
Failover : Active/Active perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Enabled perpetual
Security Contexts : 2 perpetual
GTP/GPRS : Disabled perpetual
AnyConnect Premium Peers : 10 perpetual
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 250 perpetual
Total VPN Peers : 250 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
UC Phone Proxy Sessions : 2 perpetual
Total UC Proxy Sessions : 2 perpetual
Botnet Traffic Filter : Disabled perpetual
Intercompany Media Engine : Disabled perpetual
Cluster : Disabled perpetual
This platform has an ASA 5510 Security Plus license.
敲不出来的命令可以暂时放一下,应该没有什么影响。
IKEv2和SSLVPN是一码事情啊?只不过ssl用的是DTLS,ipsec用的ikev2罢了。你group-policy里面配置了“vpn-tunnel-protocol ikev2 ssl-client ssl-clientless”的啊。你最初的问题不也是这样的么?
anyconnect全版本 + SSL/DTLS + 用户名密码(下面用aaa代替)==> ok
anyconnect全版本 + IPSec/IKEv2+ aaa ==> ok
anyconnect4.8以下版本 + SSL/DTLS + aaa + 证书 ==> ok
anyconnect4.8以下版本 + IPSec/IKEv2+ aaa + 证书 ==> ok
anyconnect4.9及以上版本 + SSL/DTLS + aaa + 证书 ==> 不成功
anyconnect4.9及以上版本 + IPSec/IKEv2+ aaa + 证书 ==> 不成功
现在不就是最后两项有问题么?
解决 “anyconnect4.9及以上版本 + SSL/DTLS + aaa + 证书 ” 需要将ssl encryption中的低安全级别的去掉,直接配置"ssl encryption aes128-sha1 aes256-sha1 dhe-aes128-sha1 dhe-aes256-sha1"也行
解决“anyconnect4.9及以上版本 + IPSec/IKEv2+ aaa + 证书 ”的问题,需要将ikev2 policy 中的 DH group修改一下,不要选择 group 5 2,设置成"group 19 21"就可以了
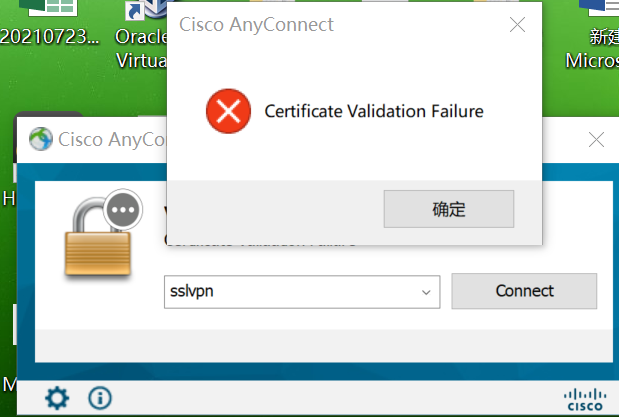
中间换证书提示 "Certificate Validation Failure" 这个自己检查一下trustpoint设置还有证书。
连接成功之后通过 setting->statistics 检查一下protocol是否正确。
更改完还是不行的话,带上相应log信息看看