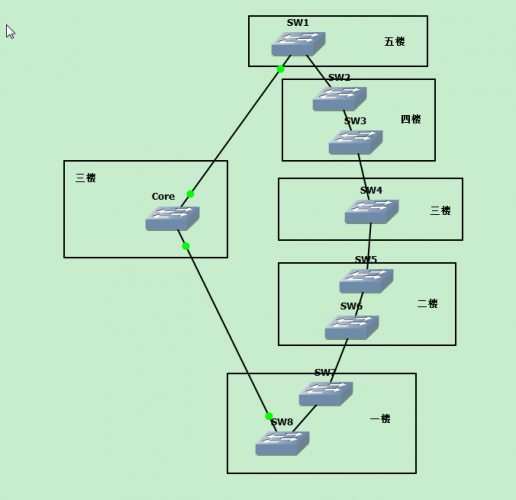
1、测试拓扑:
2、测试配置:
----------------------------------------------------------------
R1#sho run | s crypto
crypto ikev2 proposal azure-proposal
encryption aes-cbc-256 aes-cbc-128 3des
integrity sha1
group 2
crypto ikev2 policy azure-policy
proposal azure-proposal
crypto ikev2 keyring azure-keyring
peer 23.1.1.3
address 23.1.1.3
pre-shared-key <removed>
!
crypto ikev2 profile azure-profile
match address local interface Ethernet0/0
match identity remote address 23.1.1.3 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local azure-keyring
crypto ipsec transform-set azure-ipsec-proposal-set esp-aes 256 esp-sha-hmac
mode tunnel
crypto ipsec profile azure-vti
set transform-set azure-ipsec-proposal-set
set ikev2-profile azure-profile
----------------------------------------------------------------
crypto ikev2 proposal azure-proposal
encryption aes-cbc-256 aes-cbc-128 3des
integrity sha1
group 2
crypto ikev2 policy azure-policy
proposal azure-proposal
crypto ikev2 keyring azure-keyring
peer 12.1.1.1
address 12.1.1.1
pre-shared-key <removed>
!
crypto ikev2 profile azure-profile
match address local interface Ethernet0/0
match identity remote address 12.1.1.1 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local azure-keyring
crypto ipsec transform-set azure-ipsec-proposal-set esp-aes 256 esp-sha-hmac
mode tunnel
crypto ipsec profile azure-vti
set transform-set azure-ipsec-proposal-set
set ikev2-profile azure-profile
3、VPN debug过程
R1(config)#in tun 1
R1(config-if)#no shu
R1(config-if)#
*Aug 16 10:20:44.834: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
*Aug 16 10:20:44.834: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
*Aug 16 10:20:44.834: insert of map into mapdb AVL failed, map + ace pair already exists on the mapdb
*Aug 16 10:20:44.834: IPSEC: Expand action denied, discard or forward packet.
*Aug 16 10:20:44.834: IPSEC: Expand action denied, discard or forward packet.
*Aug 16 10:20:44.834: IPSEC: Expand action denied, discard or forward packet.
*Aug 16 10:20:44.834: IPSEC: Expand action denied, discard or forward packet.
*Aug 16 10:20:44.834: IPSEC:(SESSION ID = 3) (recalculate_mtu) reset sadb_root C3F1036C mtu to 1500
*Aug 16 10:20:44.834: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 12.1.1.1:500, remote= 23.1.1.3:500,
local_proxy= 0.0.0.0/0.0.0.0/256/0,
remote_proxy= 0.0.0.0/0.0.0.0/256/0,
protocol= ESP, transform= esp-aes 256 esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
*Aug 16 10:20:44.834: KMI: (Session ID: 3) IPSEC key engine sending message KEY_ENG_REQUEST_SAS to Crypto IKEv2.
*Aug 16 10:20:44.834: KMI: (Session ID: 3) Crypto IKEv2 received message KEY_ENG_REQUEST_SAS from IPSEC key engine.
*Aug 16 10:20:44.856: KMI: (Session ID: 3) Crypto IKEv2 sending message KEY_MGR_SESSION_CLOSED to IPSEC key engine.
*Aug 16 10:20:44.856: IPSEC(key_engine): got a queue event with 1 KMI message(s)
R1(config-if)#
*Aug 16 10:20:44.856: KMI: (Session ID: 3) IPSEC key engine received message KEY_MGR_SESSION_CLOSED from Crypto IKEv2.
R1(config-if)#
*Aug 16 10:20:46.837: %LINK-3-UPDOWN: Interface Tunnel1, changed state to up
R1(config-if)#
*Aug 16 10:20:49.055: ISAKMP:(0):: peer matches azure-profile profile
*Aug 16 10:20:49.055: KMI: (Session ID: 6) Crypto IKEv2 sending message KEY_MGR_VALIDATE_IPSEC_PROPOSALS to IPSEC key engine.
*Aug 16 10:20:49.055: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Aug 16 10:20:49.055: KMI: (Session ID: 6) IPSEC key engine received message KEY_MGR_VALIDATE_IPSEC_PROPOSALS from Crypto IKEv2.
*Aug 16 10:20:49.055: IPSEC(validate_proposal_request): proposal part #1
*Aug 16 10:20:49.055: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 12.1.1.1:0, remote= 23.1.1.3:0,
local_proxy= 0.0.0.0/0.0.0.0/256/0,
remote_proxy= 0.0.0.0/0.0.0.0/256/0,
protocol= ESP, transform= NONE (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
*Aug 16 10:20:49.055: Crypto mapdb : proxy_match
src addr : 0.0.0.0
dst addr : 0.0.0.0
protocol : 0
src port : 0
dst port : 0
*Aug 16 10:20:49.055: (ipsec_process_proposal)Map Accepted: Tunnel1-head-0, 65537
*Aug 16 10:20:49.060: KMI: (Session ID: 6) Crypto IKEv2 sending message KEY_MGR_CREATE_IPSEC_SAS to IPSEC key engine.
*Aug 16 10:20:49.060: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Aug 16 10:20:49.060: KMI: (Session ID: 6) IPSEC key engine received message KEY_MGR_CREATE_IPSEC_SAS from Crypto IKEv2.
*Aug 16 10:20:49.060: Crypto mapdb : proxy_match
src addr : 0.0.0.0
dst addr : 0.0.0.0
protocol : 256
src port : 0
dst port : 0
*Aug 16 10:20:49.060: IPSEC:(SESSION ID = 6) (crypto_ipsec_create_ipsec_sas) Map found Tunnel1-head-0, 65537
*Aug 16 10:20:49.060: IPSEC:(SESSION ID = 6) (crypto_ipsec_sa_find_ident_head) reconnecting with the same proxies and peer 23.1.1.3
*Aug 16 10:20:49.061: IPSEC:(SESSION ID = 6) (create_sa) sa created,
(sa) sa_dest= 12.1.1.1, sa_proto= 50,
sa_spi= 0x1BA3A992(463710610),
sa_trans= esp-aes 256 esp-sha-hmac , sa_conn_id= 5
sa_lifetime(k/sec)= (4608000/3600),
(identity) local= 12.1.1.1:0, remote= 23.1.1.3:0,
local_proxy= 0.0.0.0/0.0.0.0/256/0,
remote_proxy= 0.0.0.0/0.0.0.0/256/0
*Aug 16 10:20:49.061: IPSEC:(SESSION ID = 6) (create_sa) sa created,
(sa) sa_dest= 23.1.1.3, sa_proto= 50,
sa_spi= 0x3EFE2712(1056843538),
sa_trans= esp-aes 256 esp-sha-hmac , sa_conn_id= 6
sa_lifetime(k/sec)= (4608000/3600),
(identity) local= 12.1.1.1:0, remote= 23.1.1.3:0,
local_proxy= 0.0.0.0/0.0.0.0/256/0,
remote_proxy= 0.0.0.0/0.0.0.0/256/0
*Aug 16 10:20:49.061: IPSEC: Expand action denied, notify RP
*Aug 16 10:20:49.061: KMI: (Session ID: 6) IPSEC key engine sending message KEY_ENG_NOTIFY_INCR_COUNT to Crypto IKEv2.
*Aug 16 10:20:49.061: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel1, changed state to up
*Aug 16 10:20:49.062: KMI: (Session ID: 6) Crypto IKEv2 received message KEY_ENG_NOTIFY_INCR_COUNT from IPSEC key engine
4、验证:
R1#sho crypto isakmp sa >>>>将没有isakmp SA的协商
IPv4 Crypto ISAKMP SA
dst src state conn-id status
IPv6 Crypto ISAKMP SA
R1#sho crypto ipsec sa >>>>>可以查看IPSec的SA
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 12.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 23.1.1.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.1.1.1, remote crypto endpt.: 23.1.1.3
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x3EFE2712(1056843538)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x1BA3A992(463710610)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 5, flow_id: SW:5, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4280852/3589)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3EFE2712(1056843538)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 6, flow_id: SW:6, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4280852/3589)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1#sho crypto engine connections active >>>>>目前还没有测试流量
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
5 IPsec AES256+SHA 0 0 0 12.1.1.1
6 IPsec AES256+SHA 0 0 0 12.1.1.1
1007 IKEv2 SHA+AES256 0 0 0 12.1.1.1
R1#show crypto session detail >>>>>IPSec Flow应该是任意,只要进入tunnel的流量就加密
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect
Interface: Tunnel1
Profile: azure-profile
Uptime: 00:00:18
Session status: UP-ACTIVE
Peer: 23.1.1.3 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 23.1.1.3
Desc: (none)
Session ID: 6
IKEv2 SA: local 12.1.1.1/500 remote 23.1.1.3/500 Active
Capabilities:(none) connid:1 lifetime:23:59:42
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 0 drop 0 life (KB/Sec) 4280852/3581
Outbound: #pkts enc'ed 0 drop 0 life (KB/Sec) 4280852/3581
R1#ping 100.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.1.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/6 ms
Interface: Tunnel1
Profile: azure-profile
Uptime: 00:00:31
Session status: UP-ACTIVE
Peer: 23.1.1.3 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 23.1.1.3
Desc: (none)
Session ID: 6
IKEv2 SA: local 12.1.1.1/500 remote 23.1.1.3/500 Active
Capabilities:(none) connid:1 lifetime:23:59:29
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 5 drop 0 life (KB/Sec) 4280851/3568
Outbound: #pkts enc'ed 5 drop 0 life (KB/Sec) 4280851/3568
R1#ping 20.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 20.1.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/6 ms
R1#sho crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect
Interface: Tunnel1
Profile: azure-profile
Uptime: 00:00:40
Session status: UP-ACTIVE
Peer: 23.1.1.3 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 23.1.1.3
Desc: (none)
Session ID: 6
IKEv2 SA: local 12.1.1.1/500 remote 23.1.1.3/500 Active
Capabilities:(none) connid:1 lifetime:23:59:20
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 10 drop 0 life (KB/Sec) 4280850/3559
Outbound: #pkts enc'ed 10 drop 0 life (KB/Sec) 4280850/3559
R1#sho crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
5 IPsec AES256+SHA 0 10 10 12.1.1.1
6 IPsec AES256+SHA 10 0 0 12.1.1.1
1007 IKEv2 SHA+AES256 0 0 0 12.1.1.1
只有注册用户才能在此添加评论。 如果您已经注册,请登录。 如果您还没有注册,请注册并登录。