- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Cisco AMP for Endpoints - Scan removable drives upon insertion
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco AMP for Endpoints - Scan removable drives upon insertion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 12:32 PM
Just wanting to know if someone can answer whether or not there is a way to automatically kick off a scan of any storage device when initially plugged in? We are being required by audit to automatically perform a threat/virus scan whenever a removable device (majority will be USB flash drives) are plugged into a computer. Thanks for any response.
- Labels:
-
AMP for Endpoints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2019 11:28 AM - edited 07-29-2019 11:32 AM
Hello @Joshua Heath,
we do not do an automated USB drive OnDemand Scan. This can also be very time and resource intensive, e.g. if you are using a Removeable Storage Device connected using USB 2.0. I know, audit guideline are important, but you may think about the following topics.
There are some interesting things about Signature based detection mechanism we should think about.
- An endpoint can hold millions of unknown files which have not been seen by any AV Vendor. We tested this. You can test this for your own. Just hash your files on a standard system and use the API from virustotal to compare. You will be surprised, how many completely unknown files exist on a system.
- Talos discovers approx. 5 billion unique hashes per week, so you cannot hold any available information in the AV signatures.
- Endpoint products do not a cloud lookup for any file (filetype), this is still not possible. Think about all the non PE files and so on.
- How about Memory Mapped Devices, which are directly mapped into the systems memory?
- New Code or maybe files used for a targeted attack are most time not covered by any AV Signatures.
What we are doing, or, what we are doing more than traditional AV (some info, I´m not aware how familiar you are with AMP).
- We are monitoring file activity and process activity
- We are monitoring network communication.
- We are monitoring command line activity for a process which is directly executed from Removeable Storage.
- All this information is automatically processed in the AMP backend and also calculates IOCs is there is just malicious behaviour. Keep in mind, this also happens if the file just exists on the USB drive for just a few seconds.
- This is also done, if the file on the Removeable Storage is a known clean file.
- If we figure out something bad, the AMP backend generates a retrospective alert.
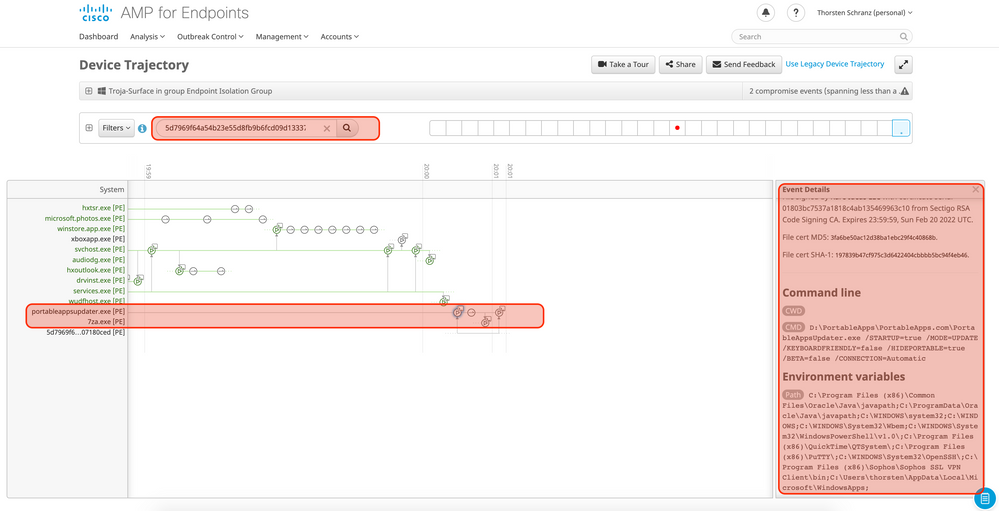
For Threat Hunting we need the behaviour information for known good files.
Below you can see the monitored activity (process, file, network and command line) from a good file.
Hope this helps,
Greetings, Thorsten
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: