- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Re: Will AMP for Endpoint remove Malware or just quarantine?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Will AMP for Endpoint remove Malware or just quarantine?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2018 04:44 PM - edited 02-20-2020 09:06 PM
400 endpoint deployment. It is finding and quarantining like it should. The malicious activity is staying in quarantine. Does A4E remove the Malware or does it rely on an additional component to actually remove it?
- Labels:
-
AMP for Endpoints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2018 07:30 AM
Do you mean, will it clean an infected system? I do not believe that capability is part of AMP. It will quarantine a malicious file (Supposedly) and prevent a malicious file from executing (Supposedly), but once a system is infected you will need to use a valid tool to clean and remove.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2018 08:16 AM
It will not remove malware if it installed. What AMP does is hopefully get the file before it is executed and it will quarantine. So if the user downloads a malicious executable and puts in their Documents folder, AMP will detect it and quarantine it to its own folder. If it still is marked malicious after analysis it will stay in that folder. After 30 days it is supposed to be deleted, but I have never been able to confirm that 100% as far as time frame. Personally, I would rather have a shorter time frame. If it is determined to not be malicious within that 30 days, it will be restored to its original location.
If the user clicks on the executable and installs the malware, then no, AMP does not remove that. It will hopefully prevent it from running in the first place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 10:17 AM
Good day, Steve,
AMP would quarantine malicious files and remove completely after 30 days. Within 30 days, users can restore. After 30 days, restore operation is not possible. Please refer to the original user guide.
https://docs.amp.cisco.com/en/A4E/AMP%20for%20Endpoints%20User%20Guide.pdf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2019 11:34 AM - edited 08-16-2019 11:35 AM
Is there a way to restore the Quarantined Files on the local machine instead of from the Cloud? Some of our users are complaining of the length of time it takes for the files to be restored from the Cloud.
The link to the user guide previously posted by Cisco's Employee is broken.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2019 03:40 PM
Hello J. Hefner,
I'm Luis from Cisco TAC Advance Threat Solutions team, answering your question about a way to restore quarantined files from the local machine instead from the cloud.
I can understand that in cases of false positives, the time that it takes for the false positive to be identified or the time it takes to get the file restored on the end user machine could be somewhat long, but if a user is able to restore a file by its own, If the file has not been properly excluded or deemed benign by the cloud, and the user could restore the file, AMP will just quarantine it again.
Also, by having the need to do it from the console, we ensure that an administrator has reviewed the file and determined if the file is trusted or not, keeping the endpoints secure.
Note:
To download "AMP for endpoints user guide" and other supporting documents follow these steps:
1)
2)
User guide: https://docs.amp.cisco.com/en/A4E/AMP%20for%20Endpoints%20User%20Guide.pdf
Cheers,
Luis Velazquez
Technical Consulting Engineer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 02:34 AM
Hello @J Hefner,
yes, the file is fully automated restored based on the following two conditions.
- The file will be classified clean again
- you are adding the hash of the file to the Application Whitelist.
After the next successful policy update, the file is automatically restored from quarantine.
Greetings,
Thorsten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 02:45 AM - edited 08-19-2019 02:46 AM
Hello @Steve Bellan,
AMP does much more than only removing the a threat. Yes, we do it in real time, but also retrospective. We also restore a file fully automated from the quarantine. See some technical details below.
I wrote an answer to another topic, but explains the limitations of signature based engines. So we addressed this, and added much more capabilities to the endpoint and also to the backend: https://community.cisco.com/t5/advanced-threats/cisco-amp-for-endpoints-scan-removable-drives-upon-insertion/m-p/3899476/highlight/true#M1598
What we are doing, or, what we are doing more than traditional AV (some info, I´m not aware how familiar you are with AMP).
- We are monitoring file activity and process activity.
- We are monitoring network communication.
- We are monitoring command line activity for a process.
- All this information is automatically processed in the AMP backend and also calculates IOCs if there is just malicious behaviour/activity. Keep in mind, this also happens if the file just exists on the system for just a few seconds.
- This is also done, if the file is a known clean file.
- If we figure out something bad, the AMP backend generates a retrospective alert.
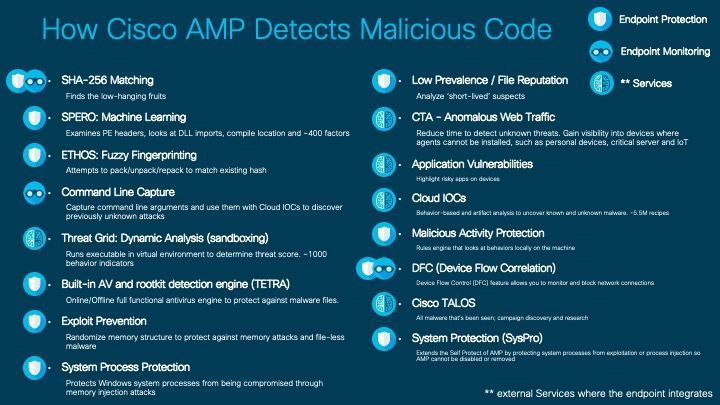
Enclosed an overview about the Engines, Features and Integrations the Endpoint has.
There are new Engines and Features coming up this year, so stay tuned.... :-)
You can also extend the endpoint capabilities with all the integrations we are providing.
Hope this helps,
Greetings, Thorsten
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: