- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- Re: Unable to validate provider. Nexus Dashboard
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 06:49 AM
Unable to validate provider. Please check you configuration.
Nexus Dashboard , when I configured the provider DNS for the first time , it said that it cannot validate it but why?
I followed the steps, it arrives to the dns server but still it can't validate , even when I try to configure a LDAP domain login and try to add the provider it just throws the same error: "Unable to validate provider. Please check you configuration."
what should I check? what can be wrong?
I'm really lost.
Solved! Go to Solution.
- Labels:
-
ACI App Center
-
ACI Multi-Site
-
APIC
-
Cisco ACI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 07:34 AM - edited 05-30-2023 08:04 AM
Im using ND 2.1.2 .
But The LDAP still doesn't work, We suspect it might be the time different causing the kerberos to fail, but I doubt it.
But I cant change it due to the fact that the command timedatectl prompts "timedatectl: Failed to create bus connection: No such file or directory" so I'm abit stuck here
Still it seems that the DNS keeps on searching weird DNS records and I would like it to stop, it is useless data traffic, It searches for "staging-connectdna.cisco.com." and "nodectrlr-svc.cisco.com" now it won't ever reach it cause it is a closed network so I really don't need it.
I suppose upgrading to Nexus Dashboard to 2.3 is a possibility but I don't that it is a solution. From the IDM side I see it recieving the DNS requests and the answers but it still fails.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 08:28 AM
Do you have a valid NTP server configured?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 08:54 AM
I suppose. It doesnt prompt any error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 08:33 AM
If you use port 636 you will need to enable SSL
If you enable SSL, you must also provide the SSL Certificate and the SSL Certificate Validation type:
▪ Permissive: Accept a certificate signed by any certificate authority (CA) and use it for encryption.
▪ Strict: Verify the entire certificate chain before using it
Working with Certs is explained in the User Guide: https://www.cisco.com/c/en/us/td/docs/dcn/nd/2x/user-guide/cisco-nexus-dashboard-user-guide-211.pdf.
If you're not using SSL, then you don't need this. As long as the AVPair/GroupMap is setup, should be enough.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 09:01 AM
Well the user guide doesn't specify what ssl certificate to use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 09:21 AM
What I don't understand is how to set manually the time zone with the command timedatectl which doesnt work on the CLI of the Nexus Dashboard.
Nevertheless where can I look at logs in the Nexus Dashboard side to see what's going on with the LDAP attempt to get Validation from the IDM.
Because there is no tcpdump and no sudo on the Nexus Dashboard side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 10:20 AM - edited 05-30-2023 10:21 AM
You don't set anything from the CLI. You can adjust the timezone from the UI.
Collecting a techsupport bundle will grab all logs.
Might want to consider opening a TAC case as your issue is a little more complex than a forum can assist with.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 10:24 AM
I see, so the time in the cli of the nexus dashboard when I type "date" has nothing to do with the LDAP request?
Because the time set there is different from what is set in the UI.
I will open a TAC , but firstly I will upgrade the NXD to 2.3.
Is the Validation that you said exists only in 2.2 and earlier is only DNS related or also the LDAP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 10:57 AM
It's DNS related only. Advise TAC about the time discrepency, if they need to change/update it, they'll have root access.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 12:00 PM
Thanks about everything Robert!
I'll update here about the solution if I would find one and about the logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2023 01:07 AM - edited 06-01-2023 06:10 AM
I think I might have found the problem, When setting up the LDAP in ACIP there is a field of "filter" while NXD doesn't have one.
After checking logs I see that "user doesn't exist" and a filter set to be "(sAMAccountName={username})" .
@Robert Burns
Now I don't know how to change the filter in the NXD to check if it is the problem, But I set a filter in the APIC and it is working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2023 06:21 AM
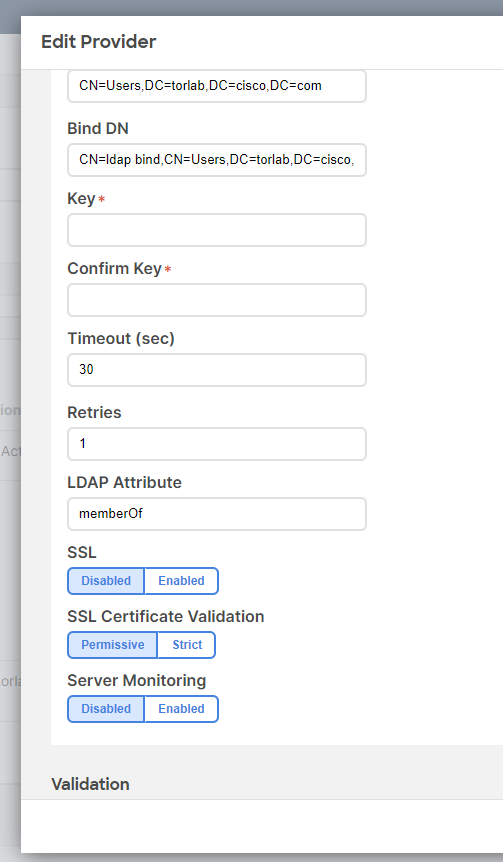
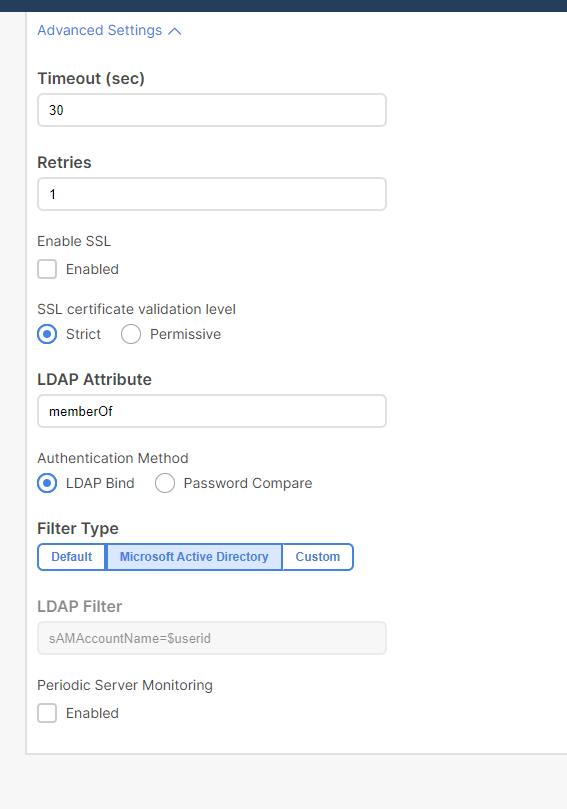
On ND you only need to set the "LDAP Attribute" under the Provider configuration. I'm using memberOf since I'm authenticating against MS AD with group maps
Here's my ND LDAP Provider settings
Here's my APIC LDAP provider settings (both to same provider):
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2023 07:23 AM
But that's exactly the problem. do you see the LDAP Filter in the APIC ? for us it is set to custom and to a different filter, In The Nexus Dashboard there is no way to change it and I need to change it.
The problem is that the IDM doesn't under stand "sAMAccountName = $userid" and I need it to be something else, "uid=$userid".
For some reason there is an option to change it in the APIC with "LDAP Filter" but no way to Change it in the Nexus Dashboard.
@Robert Burns
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2023 09:27 AM
I've confirmed that this functionality (Custom LDAP filter) does not yet exist on Nexus Dashboard. I've opened an enhancement request to port the AAA functionality from APIC > ND so they're functionally similiar. I'd suggest you open a TAC SR, and ask them to link to this CDET (will help prioritze this enhancement). https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwf51550
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2023 03:02 PM
Thank you so much @Robert Burns for all the help ! I will update what Cisco will say in the TAC and hopefully it will be fixed.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide