- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- Re: Again "Access (802.1P)" vs "Access (Untagged)"...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Again "Access (802.1P)" vs "Access (Untagged)"...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2020 10:05 AM
Honestly I have been working on ACI for a while now...But I still have trouble to fully understand the "Access (802.1P)" vs "Access (Untagged)"...
I was working on a issue diagnose for a customer and a physical Windows server plugged into the Leaf switches experiencing packet lost...The server dual connection is setup as vPC and the static path was in mode "Access (802.1P)" for VLAN 192.
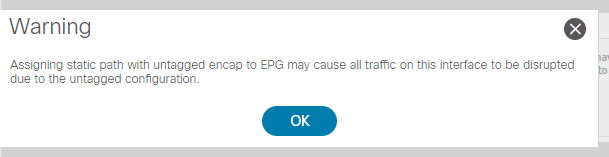
When I login to try to switch to "Access(untagged)", I got warning below which scares me as this is not my network and I do not know whole a lot of the details yet...Anyway long story short, the issue was fixed but nothing to do with ACI...But that leaves me wonder more about the reason of that warning and questioning about my understanding of "Access (802.1P)" vs "Access (Untagged)"...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2020 10:58 AM - edited 11-03-2020 11:03 AM
It's really simple. It's a matter of Trunk tagged, Trunk Native and Access port configurations. The only confusion is how we apply a native VLAN on a trunk interfaces - which involves using an 802.1p CoS field. Just ignore this, and understand its essentially the equivalent of a native VLAN for an interface operating as a Trunk.
Trunk = Trunk mode. All ingress/egress traffic is tagged. Other EPGs can be bound also utilize the same interface as long as they use a different VLAN ID.
Access 802.p = Trunk mode, but the VLAN assigned will be untagged/native. Allows other EPGs to use this port with other tagged VLAN IDs.
Access = Access Port . All Traffic to/from this port for this EPG will be untagged. No other EPG can leverage this port.
The only caveat I'd warn is if doing PXE boot, ensure you're using "Access" mode, since the 802.1p can cause issues with it.
The reason we toss a warning when switching to Access (untagged) is because IF you had other EPGs trying to use this port, you could kill that communication. Only a single EPG can use an Access(untagged) configured port.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2020 12:42 PM
The reason we toss a warning when switching to Access (untagged) is because IF you had other EPGs trying to use this port, you could kill that communication. Only a single EPG can use an Access(untagged) configured port.
Thanks! Say I have two EPGs: EPG-A and EPG-B under the same tenant and same VRF (same or different Application Profiles). For whatever the reason, I would like to use VLAN 101 as the "Access (untagged)" in followings. Will both or either of them work?
1. Static bind EPG-A and EPG-B to Port 1/3 with VLAN 101 as "Access (Untagged)" on Leaf 101 and 102 respectively.
2. Static bind EPG-A and EPG-B to Port 1/3 and 1/4 respectively with VLAN 101 as "Access (Untagged)" on Leaf 101.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2020 02:18 PM
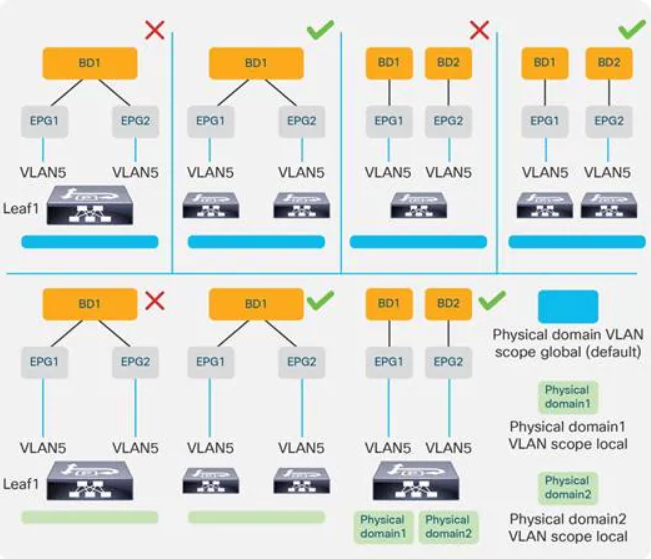
1. You cannot associate the same vlan on same switch, same port to two different EPG. Never.
2. You cannot associate the same vlan on same switch on different interfaces, by default. You can do that however, if you enable vlan scope local option.
But since one image is worth a 1000 words, I hope this will clarify:
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2020 03:04 PM
Thanks for the picture and link.
I donot think your #1 matches mine. My #1 should match the second topology in the picture. Your #1 should work if the mode is set to trunk or 802.1p.
regarding #2, I will further check the local scope option. BTW, Do you mean the port vlan?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2020 09:06 AM
Only a single EPG can use an Access(untagged) configured port.
This statement does not apply if using VLAN10 as "Access(untagged)" for Leaf101 Eth1/2 under EPG1 and VLAN20 as "Access(untagged)" for Leaf101 Eth1/3 OR Leaf102 Eth1/2 under EPG2, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 05:48 AM
Correct. My statement applies only to the same specific interface.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2022 07:52 AM
Thanks for the clarification, just like the topic requester, the Cisco ACI message regarding the Access (untagged) scared me! hahahaha
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2020 04:36 AM
Hi Guys,
Before explaining the differences between Trunk, Access 802.1P and Access (untagged), a limit of Cisco ACI fabrics should be mentioned:
Error:400 - Validation failed: Validation failed for fv::EPg: uni/tn-TenantName/ap-AppProfile/epg-EpgName vlan: vlan-200 fvMode should be either set tagged or untagged on all ports.
In other words, in a leaf, inside the same EPG, VLANs can be tagged (trunk or access 802.1P) or untagged, but not both. Or, if a VLAN is defined inside a trunk, it cannot be defined as access (in the same leaf, in the same EPG).
But what’s the difference between access 802.1P and access untagged?
802.1P refers to a QoS implementation using 802.1Q protocols. In other words, a port in Access (802.1P) should send and receive frames tagged with VLAN 0 (using 802.1Q). Untagged ports should send and receive frames untagged (without 802.1Q). Most of modern operating system should be able to manage tagged frames with VLAN 0 like untagged frames. But using PXE across a Cisco ACI fabric could lead to some issues, because small BIOS/firmware could not read VLAN 0 tagged frames.
Moreover there are two generation of switches:
Generation 1 Switches
If the port is configured in Access (802.1p) mode:
On egress, if the access VLAN is the only VLAN deployed on the port, then traffic will be untagged.
On egress, if the port has other (tagged) VLANs deployed along with an untagged EPG, then traffic from that EPG is zero tagged.
On egress, for all FEX ports, traffic is untagged, irrespective of one or more VLAN tags configured on the port.
The port accepts ingress traffic that is untagged, tagged, or in 802.1p mode.
If a port is configured in Access (Untagged) mode:
On egress, the traffic from the EPG is untagged.
The port accepts ingress traffic that is untagged, tagged, or 802.1p.
Generation 2 Switches
Generation 2 switches, or later, do not distinguish between the Access (Untagged) and Access (802.1p) modes. When EPGs are deployed on Generation 2 ports configured with either Untagged or 802.1p mode:
- On egress, traffic is always untagged on a node where this is deployed.
- The port accepts ingress traffic that is untagged, tagged, or in 802.1p mode
I hope you find it helpful.
Regards,
Ali
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 10:36 AM
Thank you Ali that was informative. So If I understood you correctly, An untagged VLAN on Dot1Q ports will have no tag, but on 802.1P ports it WILL have a tag (VLAN 0), as long as thee are also other (tagged) VLANs on that same port?
Also that, this VLAN 0 has something to do with QoS?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: