- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- Re: Find relationship between BD -> EPG - >Physical port binding ->Domain(Phy/VMM), IPG for all all ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2021 08:07 AM
Hi,
I want to extract the APIC config that which BD(subnets) is linked with which EPG & further how that EPG is configured with , Physical port, encap, Domain(Phy/VMM) and IPG.
I want to extract the information on excel to get an overview of the APIC configuration for clarity.
I think moquery commands may help, but unable to find the perfect moquery command. Please help.
I am sure it will help many others.
Thanks,
Solved! Go to Solution.
- Labels:
-
APIC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2021 11:16 AM
Hi @raza555,
I am afraid there is no single moquery to find out which BDs have subnets and pull the corresponding EPG information. Probably, you write a script to find out all the BDs with fvSubnet class and then match this with the fvAEPg->fvRsBd->tnFvBDName to find out the corresponding EPG(s). Once you have the EPG you can poll the respective fvAEPg class to get all the info you need.
[or]
Using this command
moquery -c fvAEPg -x rsp-subtree=full rsp-prop-include=config-only -o xml
you can extract the following from the fvAEPg class and its subclasses,
EPG Name (fvAEPg.name)
Associated BD (fvRsBd.tnFvBDName)
Associated Domain (fvRsDomAtt.tDn)
Encap (fvRsPathAtt.encap)
Static Path (fvRsPathAtt.tDN)
and also get the BD info as a separate request,
moquery -c fvAEPg -x rsp-subtree=full rsp-prop-include=config-only -o xml
Save both the files as xml and then import these as data sources in Excel. You can use Excel functions to map and match the configs. This is the easy and dirty way to view configs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 02:53 AM - edited 06-21-2021 11:35 PM
Hi @raza555 ,
[Edit: 2021.06.22] I found a far better answer. It still has some of the problems (1-5) I mentioned in my first reply, but the output of this is MUCH better, especially where multiple paths, VLANs or Domains are used in a single EPG.
apic1# bash
chris@apic1:~> icurl -s -k "http://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only" | jq --raw-output '.imdata[].fvAEPg | {EPG: .attributes.name, BridgeDomain: .children[].fvRsBd.attributes.tnFvBDName| select( . != null ), PathList: [.children[] | {interface: .fvRsPathAtt.attributes.tDn | select( . != null ), VLAN: .fvRsPathAtt.attributes.encap | select( . != null ), Tagging: .fvRsPathAtt.attributes.mode| select( . != null )}], DomainList: [.children[].fvRsDomAtt.attributes.tDn | select( . != null )]}'
Original Answer Below
My first though is I probably should have used https:// rather than http:// - BUT that doesn't make sense because you GOT a reply.
My second thought is to remove the -s (for silent) from the icurl command:
apic1# bash
chris@apic1:~> icurl -k "https://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only"
or for the filtered version:
chris@apic1:~> icurl -k "https://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only" \
| jq --raw-output \
'.imdata[].fvAEPg | .attributes.name, .children[].fvRsBd.attributes.tnFvBDName, .children[].fvRsDomAtt.attributes.tDn, .children[].fvRsPathAtt.attributes.tDn, .children[].fvRsPathAtt.attributes.encap, .children[].fvRsPathAtt.attributes.mode | select( . != null )'
My third thought is based on the 301 reply you got - seems to indicate that maybe there is a different path in different versions, but I find that hard to believe.
I did my testing on v5.2(1g) and v4.2(7f) - both work fine (except I had to use https:// on our production APIC
My 4th thought is I'll post this much and have a think again in the morning...
Forum Tips: 1. Paste images inline - don't attach. 2. Always mark helpful and correct answers, it helps others find what they need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2021 11:16 AM
Hi @raza555,
I am afraid there is no single moquery to find out which BDs have subnets and pull the corresponding EPG information. Probably, you write a script to find out all the BDs with fvSubnet class and then match this with the fvAEPg->fvRsBd->tnFvBDName to find out the corresponding EPG(s). Once you have the EPG you can poll the respective fvAEPg class to get all the info you need.
[or]
Using this command
moquery -c fvAEPg -x rsp-subtree=full rsp-prop-include=config-only -o xml
you can extract the following from the fvAEPg class and its subclasses,
EPG Name (fvAEPg.name)
Associated BD (fvRsBd.tnFvBDName)
Associated Domain (fvRsDomAtt.tDn)
Encap (fvRsPathAtt.encap)
Static Path (fvRsPathAtt.tDN)
and also get the BD info as a separate request,
moquery -c fvAEPg -x rsp-subtree=full rsp-prop-include=config-only -o xml
Save both the files as xml and then import these as data sources in Excel. You can use Excel functions to map and match the configs. This is the easy and dirty way to view configs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2021 11:05 PM - edited 06-21-2021 02:56 AM
Hi @raza555 ,
Where I was planning to lead was a similar path to @ecsnnsls - except using icurl instead of moquery (I keep finding bugs in moquery) and using json output
So - here is @ecsnnsls 's answer re-worked: Note the bash prompt - you'll have trouble typing the ? character if you don't exit to bash.
apic1# bash
chris@apic1:~> icurl -s -k "https://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only"
or if you want it pretty:
chris@apic1:~> icurl -s -k "https://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only" | jq '.'
But to extract just the bits you want form above, you'll need to use the jq (JSON Query) utility
So try this (then guess how I spent my rainy Sunday!)
chris@apic1:~> icurl -s -k "https://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only" \
| jq --raw-output \
'.imdata[].fvAEPg | .attributes.name, .children[].fvRsBd.attributes.tnFvBDName, .children[].fvRsDomAtt.attributes.tDn, .children[].fvRsPathAtt.attributes.tDn, .children[].fvRsPathAtt.attributes.encap, .children[].fvRsPathAtt.attributes.mode | select( . != null )'
Now the output is not perfect by any stretch of the imagination. Here are the flaws I've noticed:
- My output is NOT in Excel or even a suitable .csv format as you asked for
- If the same EPG exists in multiple tenants, there is no indication of which tenant the EPG belongs to. This could be fixed (if not elegantly) by changing .attributes.name to.attributes.dn in the line above
- The path for a VPC doesn't reveal the port numbers, but does reveal the VPC Interface Policy Group (you asked for both)
- The path for a single port reveals the port number, but I didn't extract the Access Port Policy Group - and that would take another iteration somewhere. That's in the "too hard" basket for now.
- Although I have a VMM Domain configured, I didn't have any active VMs, so I didn't get to chase that bit either before Sunday ran out. Possibly also in the "too hard" basket.
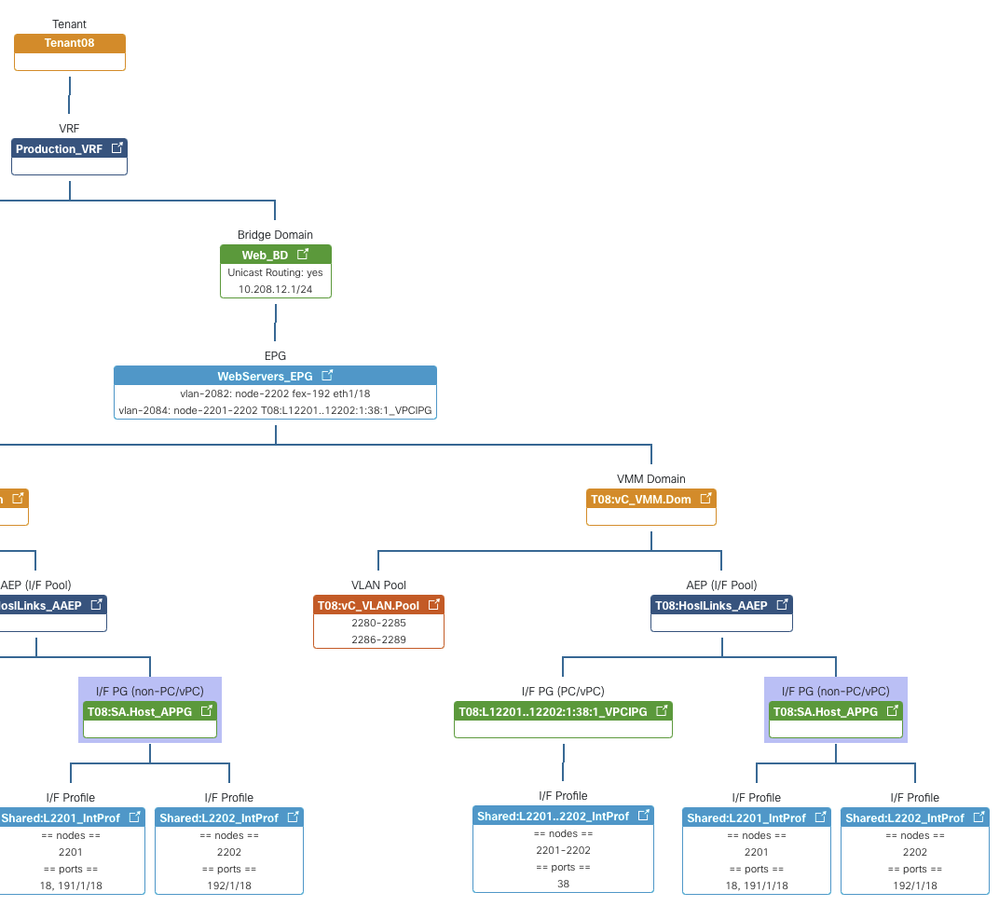
- If an EPG has multiple static paths, the paths, encapsulation and mode don't get grouped. In my example output below, the WebServers_EPG has two paths, the first mapped to vlan-2084 tagged (regular) on a VPC, the second mapped to a FEX port on vlan-2082 untagged.
WebServers_EPG Web_BD uni/vmmp-VMware/dom-T08:vC_VMM.Dom uni/phys-T09:MappedVLANs_PhysDom topology/pod-1/protpaths-2201-2202/pathep-[T08:L2201..2202:1:38_VPCIPG] topology/pod-1/paths-2202/extpaths-192/pathep-[eth1/18] vlan-2084 vlan-2082 regular untagged
I would have been happier if I'd been able to get the query to produce the above as
WebServers_EPG
Web_BD
uni/vmmp-VMware/dom-T08:vC_VMM.Dom
uni/phys-T08:MappedVLANs_PhysDom
topology/pod-1/protpaths-2201-2202/pathep-[T09:L2201..2202:1:38_VPCIPG]
vlan-2084
regular
topology/pod-1/paths-2202/extpaths-192/pathep-[eth1/18]
vlan-2082
untagged
But I'll leave that as an exercise for the reader (BTW - if you manage it, DO let us know how you did it)
Bonus Addendum!
What you are seeking might already be available in graphical form rather than Excel format. Did you know about the Policy Viewer App for the Cisco APIC?
It will give you a graphical representation of all the things you asked for.
To install and use this App, download the app to your local PC, then log into the APIC with admin rights and navigate to the Apps > Installed Apps, then stare at the screen for five minutes (: until you spot the highly-obscure and un-obvious Add Application icon on the right-hand side that enables you to upload the app to the APIC.
You access the Policy Viewer via the Tenant - look for an extra sub-menu on the right hand side of several Tenant objects.
However, no matter how pretty this looks, it doesn't delver you an Excel spreadsheet.
To achieve that goal, I believe you are going to have to write a program of some sort.
And to do that, you'll need to understand the relationships between the objects, which aren't necessarily as simple as the above diagram might suggest. And a good learning tool to assist with this is another APIC App - the APIC Managed Object Browser and for this one you'll need to read the documentation carefully.
[Edit: Updated http:// to https://]
Forum Tips: 1. Paste images inline - don't attach. 2. Always mark helpful and correct answers, it helps others find what they need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 02:24 AM
Thanks a lot to both @ecsnnsls & @RedNectar Much appreciated.
@RedNectar Thanks a lot for spending your Sunday time for me
When I enter below cmd, I get output as below, hope something not gone wrong, please advise
apic1# bash
APIC-01:~> icurl -s -k "http://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only"
<html>
<head><title>301 Moved Permanently</title></head>
<body bgcolor="white">
<center><h1>301 Moved Permanently</h1></center>
<hr><center>Cisco APIC</center>
</body>
</html>
APIC-01:~>
I will also look into the "Policy Viewer App for the Cisco APIC", didn't knew about it.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 02:53 AM - edited 06-21-2021 11:35 PM
Hi @raza555 ,
[Edit: 2021.06.22] I found a far better answer. It still has some of the problems (1-5) I mentioned in my first reply, but the output of this is MUCH better, especially where multiple paths, VLANs or Domains are used in a single EPG.
apic1# bash
chris@apic1:~> icurl -s -k "http://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only" | jq --raw-output '.imdata[].fvAEPg | {EPG: .attributes.name, BridgeDomain: .children[].fvRsBd.attributes.tnFvBDName| select( . != null ), PathList: [.children[] | {interface: .fvRsPathAtt.attributes.tDn | select( . != null ), VLAN: .fvRsPathAtt.attributes.encap | select( . != null ), Tagging: .fvRsPathAtt.attributes.mode| select( . != null )}], DomainList: [.children[].fvRsDomAtt.attributes.tDn | select( . != null )]}'
Original Answer Below
My first though is I probably should have used https:// rather than http:// - BUT that doesn't make sense because you GOT a reply.
My second thought is to remove the -s (for silent) from the icurl command:
apic1# bash
chris@apic1:~> icurl -k "https://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only"
or for the filtered version:
chris@apic1:~> icurl -k "https://localhost/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only" \
| jq --raw-output \
'.imdata[].fvAEPg | .attributes.name, .children[].fvRsBd.attributes.tnFvBDName, .children[].fvRsDomAtt.attributes.tDn, .children[].fvRsPathAtt.attributes.tDn, .children[].fvRsPathAtt.attributes.encap, .children[].fvRsPathAtt.attributes.mode | select( . != null )'
My third thought is based on the 301 reply you got - seems to indicate that maybe there is a different path in different versions, but I find that hard to believe.
I did my testing on v5.2(1g) and v4.2(7f) - both work fine (except I had to use https:// on our production APIC
My 4th thought is I'll post this much and have a think again in the morning...
Forum Tips: 1. Paste images inline - don't attach. 2. Always mark helpful and correct answers, it helps others find what they need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 04:53 AM
Hi @raza555
Try connecting to port 7777:
icurl 'http://localhost:7777/api/class/fvAEPg.json?rsp-subtree=full&rsp-prop-include=config-only'
HTH
Marcel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 07:45 AM
Hi Guys,
Thanks a lot for the great help. Much appreciated.
It worked with https://
Thankyou
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 08:55 AM
Hi, Chris.
I heard about sometimes the APIC APP in general can cause CPU and/or MEM spike, and might cause issues at upgrade. So still very cautious of installing them.
Leo
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide