- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- interconnect aci and campus
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
interconnect aci and campus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2020 05:28 AM
Hi,
2 questions here :
1. if a campus network has only access layer switches in the buildings of the campus and multiple distribution layer switches in the datacenter building, is it recommended to aggregate the traffic from the DILs with a core layer and then attach the core to the aci leafs or connecting directly the DIL switches to the leafs is the best way to go?
2. Related to the previous question : does it make sense to put firewalls between the core or DIL (depending on the design selected in question 1 ) and the leafs or it makes more sense to attach the firewalls on different leafs and use a service graph to redirect the traffic to the firewalls ?
Thank you
- Labels:
-
Cisco ACI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2020 07:53 AM
Hi @taytibob ,
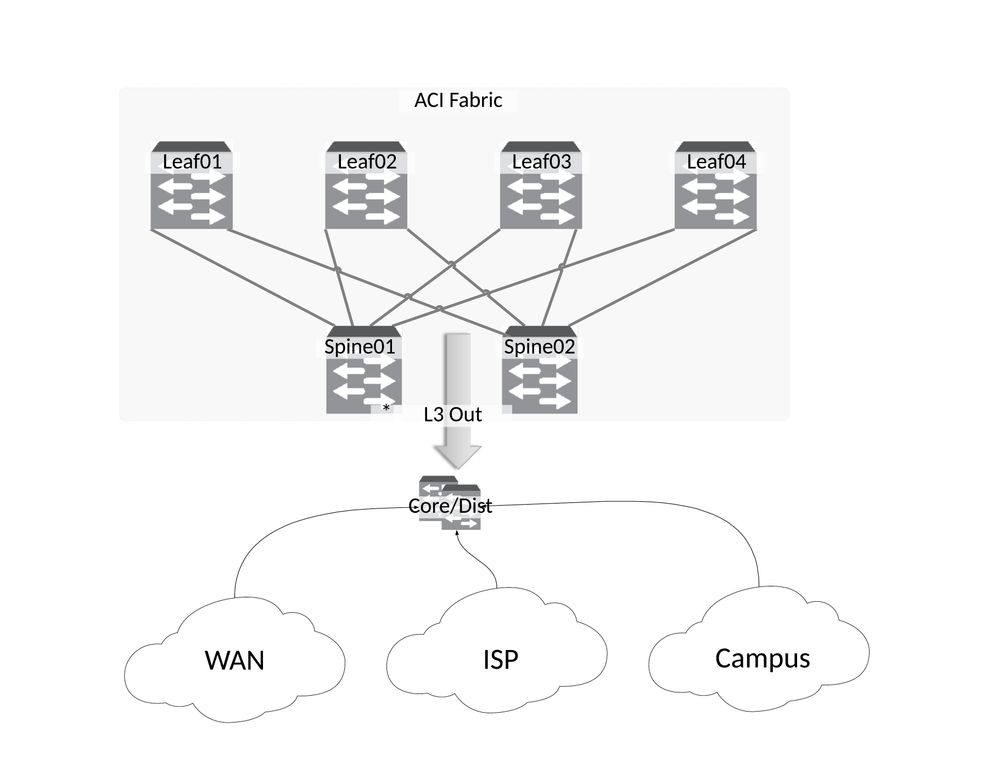
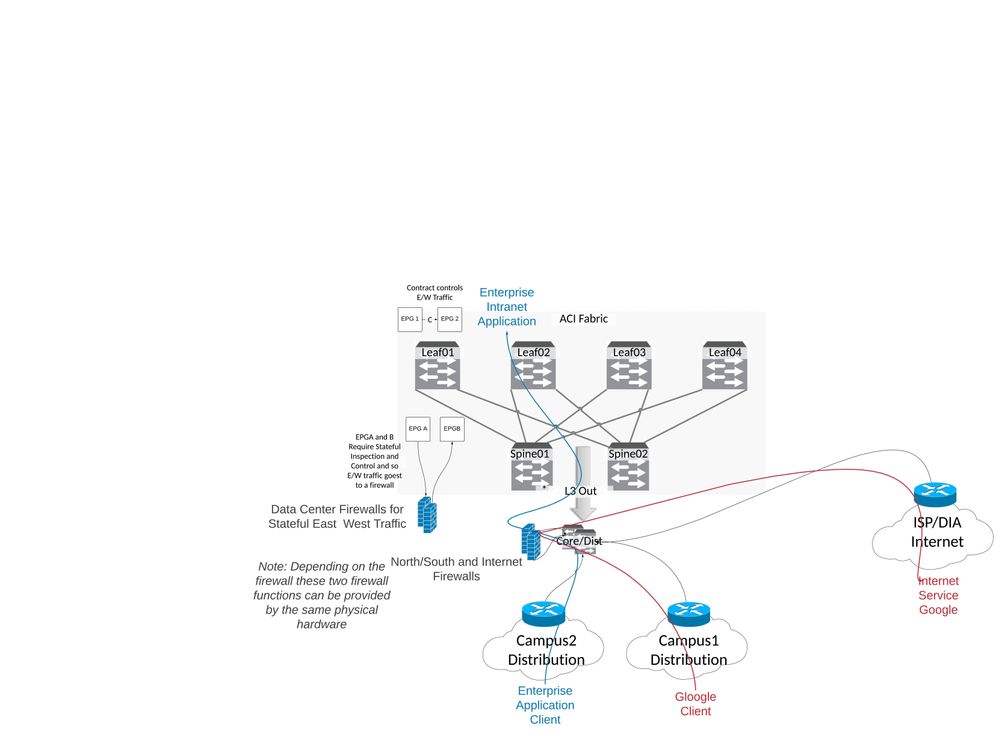
I always recommend your data center fabric go to a Core or Collapsed Core/Distribution via Layer 3 in its production state. (I say that because its very common to have Layer 2 connections to your old data center during your migration into ACI). Your Core does what your core commonly does, it ties WAN, ISP, Campus, and other services together and lets you deal with routing etc. You can certainly have an L3Out to our campus aggregation and another to a different core that handles WAN/Internet. It really depends on what you are trying to do.
Its very common to have a Firewall between the Core and your Data Center, or lets just say in front of your Data Center, to control your North/South traffic. ACI contracts control your data center East/West traffic and you can also use Firewalls for stateful control for your East West traffic within the data center. If your design does have two L3Outs for example, one to "Other" and one to "Campus" then its up to you and your organization to determine if a firewall is required. Knowing nothing else about your environment, I would strongly recommend it as your Campus probably represents a pretty large attack vector and you want to protect your data center assets. If nothing else you want a control point into your data center.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2020 09:16 AM
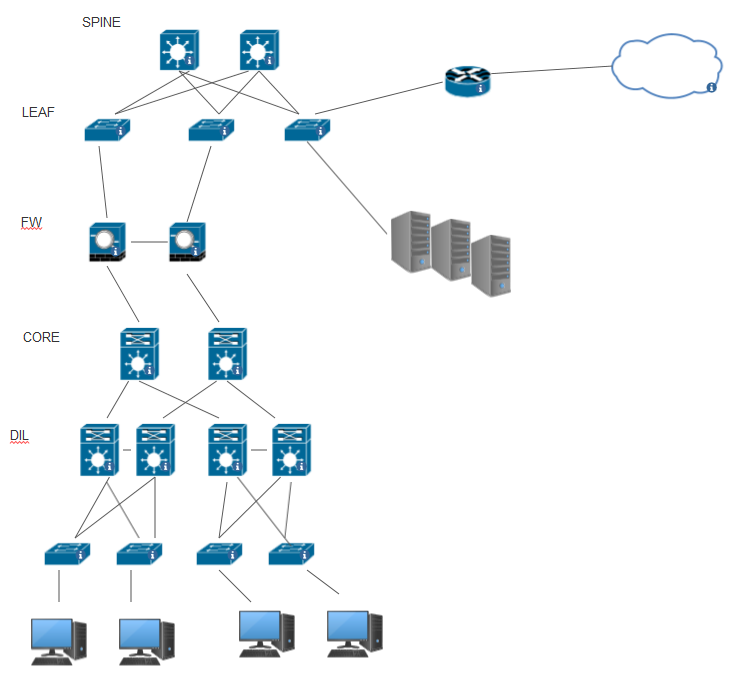
The first option is the following :
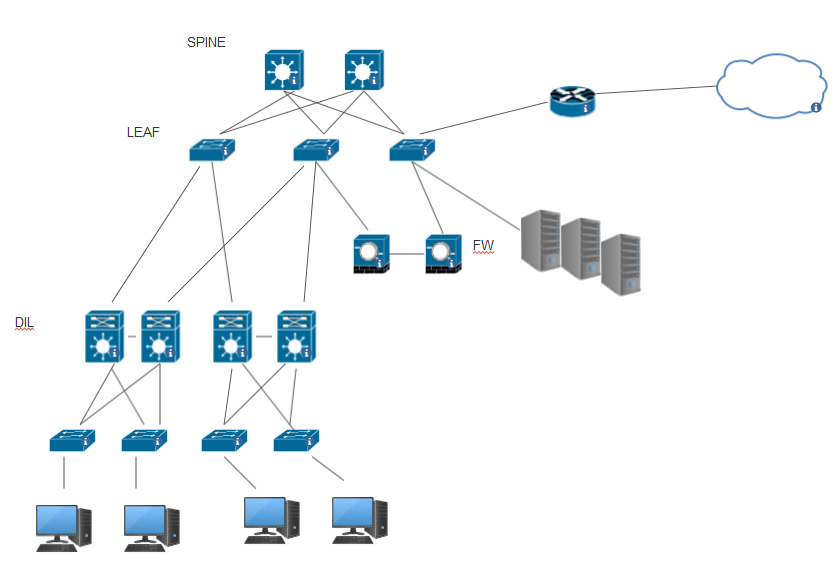
The second option is the following:
The benefit that i see for the second option is that i can control the traffic between the 2 domains (DIL 1 and DIL 2) using the ACI EPG features and redirect to the firewalls.
In addition it reduces the number of hops/devices between the clients and servers.
What do you think?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 07:26 AM
Hi @taytibob,
Here is what I would tell a client who came to me with Option 2.
I don't recommend the Option2 design.
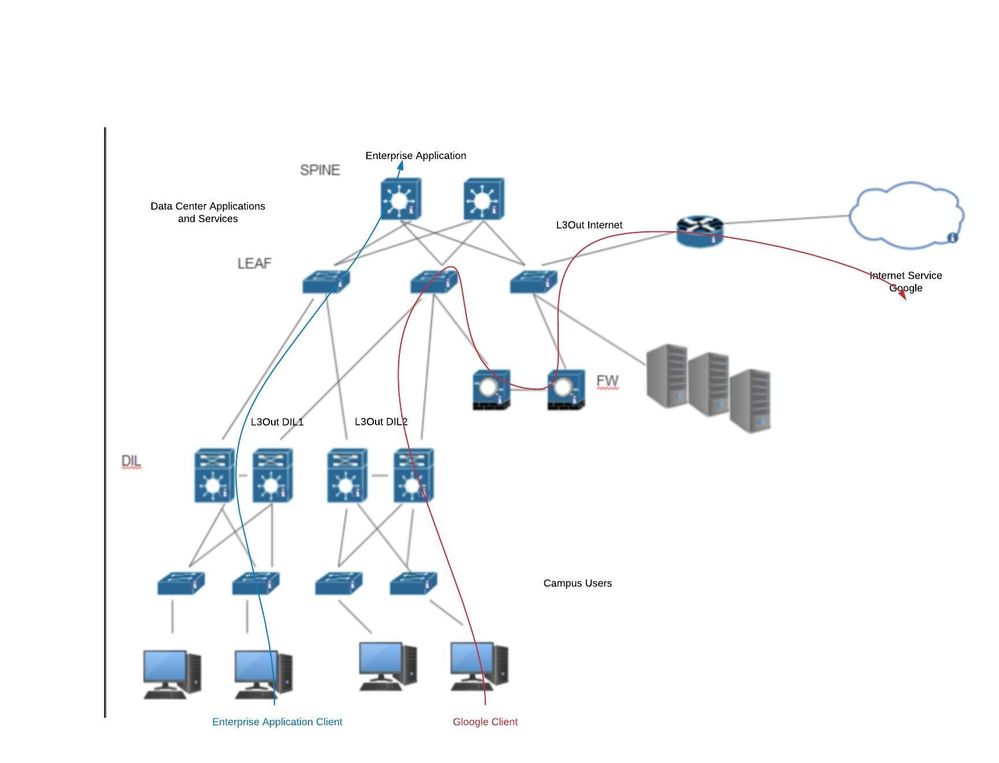
First its mixing functional domains and treats the data center fabric like core. If I understand Option 2 correctly, the data center has the link to the internet and has the links to the campus distribution. Firewalls are available to control traffic but now a client in the Campus accessing something on the internet has to bounce that traffic through your data center and perhaps it is routed to your firewall then back up to go out the Internet link that is also hanging off your data center. So the data center is now hair pinning all traffic to the Internet. Thats the job of a core. The core sends appropriate traffic to the Data center or to the Internet or wherever its going. The data center only sees traffic destined for data center applications and services. it also looks like the expectations it to use ACI contracts to control North/South traffic (the traffic from the Campus). ACI contracts are there to help control East West (along with Firewalls as needed).
I generally recommend something along the lines shown in the diagram below. I don't know why the inclination is to treat the fabric like a core. Can you do it, sure. But I always ask: "Are you running all your campus, wan, and internet traffic through your data center switches today? In some cases the answer is "yes" because the current design has the core acting as a core and also as a data center distribution (the SVIs are there) but when you introduce ACI you don't want to move all of that core function into the data center fabric, just the data center distribution part of it! But I get that they are Nexus switches and its easy to think of them in the same way you might think of your Nexus 7K core today. If client traffic is going out to the Internet or out to the WAN, I don't want my data center fabric involved at all. My data center fabric is for my enterprise services. its an endpoint, not a pass through.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide