- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Networking
- ACE 4710 in Internal and DMZ environments
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACE 4710 in Internal and DMZ environments
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2012 11:02 PM
Hi, I am looking to deploy an ACE 4710 for use in an internal and DMZ environment simultaneosly. Everything that I have been reading indicates that we can accomplish this but I wanted to post my idea of how this would work in the environment. What I want to do looks like this:
1. I need load-balancing of internal sharepoint servers. I want this to occur on a context directly connected to the internal network
2. Reverse-proxy of external traffic for OWA, Activesync and a couple of other applications. I want this to occur on a context directly connected to our DMZ.
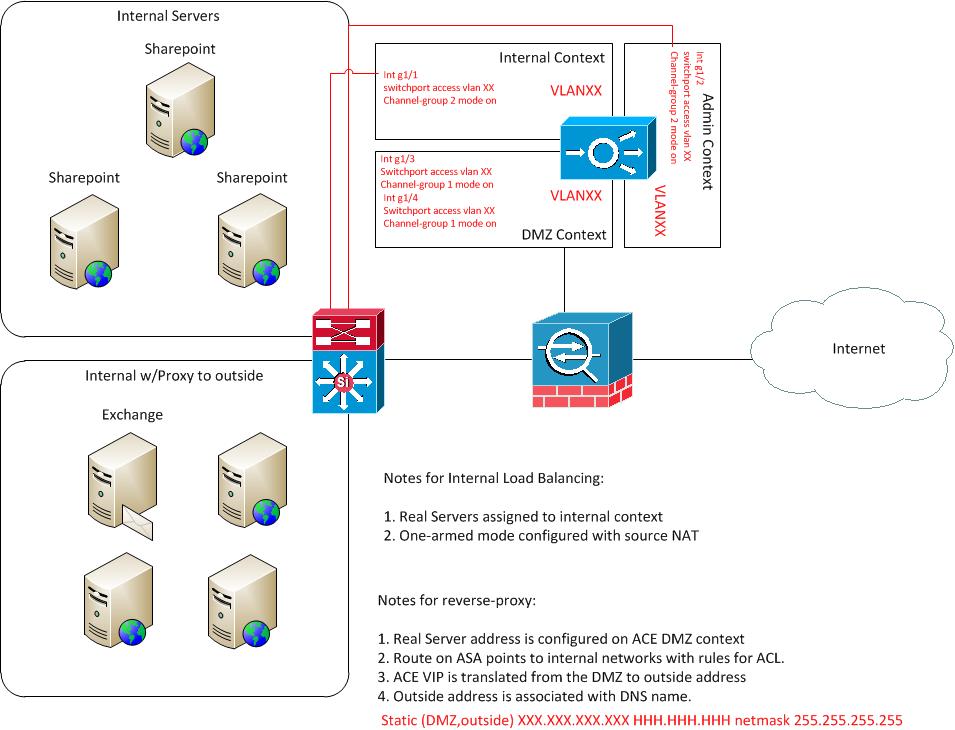
My questions are:
1. Is there any security concerns here? I do not like the idea of using one appliance between these two environments but I have no choice because we do not have multiple devices.
2. Since the servers that I need to service with the reverse proxy functionality are internal to our network, should I translate their IP's to the DMZ and then again to the outside or should I just create a route to their real (internal) addresses on the inside interface of the firewall as well as the proper ACL's?
Thanks,
MC
- Labels:
-
Application Networking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2012 04:47 AM
Hi Michael
1. Is there any security concerns here? I do not like the idea of using one appliance between these two environments but I have no choice because we do not have multiple devices.
Contexts on ACE are pretty isolated , so I'd say that such approach doesn't bring additional security issues.
2. Since the servers that I need to service with the reverse proxy functionality are internal to our network, should I translate their IP's to the DMZ and then again to the outside or should I just create a route to their real (internal) addresses on the inside interface of the firewall as well as the proper ACL's?
I'm not sure that I understood this question correctly, but it works like this : you have real servers which need to communicate with clients. Clients see those real servers as one Virtual IP , specified on ACE. So you need to have a proper routing between Virtual IP and clients (clients will never see real IPs of real servers) and you need to have a proper routing on real servers that they send backward traffic to ACE. As you mentioned that you're going to have one arm mode with source NAT - it will ensure this (if you have L2 connection between rservers and ACE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2012 06:22 AM
Hi Borys,
Thanks for the response so far.
2. Since the servers that I need to service with the reverse proxy functionality are internal to our network, should I translate their IP's to the DMZ and then again to the outside or should I just create a route to their real (internal) addresses on the inside interface of the firewall as well as the proper ACL's?
I'm not sure that I understood this question correctly, but it works like this : you have real servers which need to communicate with clients. Clients see those real servers as one Virtual IP , specified on ACE. So you need to have a proper routing between Virtual IP and clients (clients will never see real IPs of real servers) and you need to have a proper routing on real servers that they send backward traffic to ACE. As you mentioned that you're going to have one arm mode with source NAT - it will ensure this (if you have L2 connection between rservers and ACE)
Because the real servers in this case are behind the ASA on the internal network, while the ACE DMZ context is in the DMZ, I originally thought that I would have to NAT the real server IP addresses to the DMZ using a static translation and then use the translated address as my "rserver" on the ACE. However, based upon some other configurations that I have done it looks like I just need to configure a route to the "rserver" internal address on the firewall and then use the internal server addresses as my rservers on the ACE DMZ context.
Essentially, I have never used the ACE in this fashion before where I have rservers in the inside and ACE in the DMZ. Typically they both reside in one environment and it is not a question. I do not have a lab so I will need to be sure when I put this in production.
Best regards,
MC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2012 06:39 AM
Hi Michael
Thanks for clarification. Yes, it's absolutely ok from ACE point of veiw (there is no requriment to have L2 connectivity between rservers and ACE). And as you're going to have SNAT on ACE - everything should be fine.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
