- Cisco Community
- Technology and Support
- Online Tools and Resources
- Cisco Bug Discussions
- Re: CSCvg35618 - Cisco Adaptive Security Appliance Remote Code Execution and Denial of Service Vulne...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CSCvg35618 - Cisco Adaptive Security Appliance Remote Code Execution and Denial of Service Vulnerability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 01:45 PM - edited 03-20-2019 09:51 PM
In the Known Fixed Releases section of this bug, it states the bug is fixed in ASA 9.6(3.18).
When I read the 9.6(3) Interim Release Notes the bug is not listed as being fixed.
https://www.cisco.com/web/software/280775065/137781/ASA-963-Interim-Release-Notes.html
Can anyone confirm this is resolved in the latest interim release which is 9.6(3.20) ?
Thanks!
Tim
- Labels:
-
Cisco Bugs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 03:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 03:27 PM
So at 3 pm today I printed the Release Notes to a PDF so I could mark them up in my PDF reader.
I opened a TAC case at 5 pm to discuss the confusion with an engineer. When I was on the phone with the TAC engineer I refreshed the Release Notes on the web and the bug showed up. Wa-la!
Thanks,
Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2018 11:19 AM
a TAC to us "Unfortunately version 9.6(1) it is affected, the fixed release is 9.6.3.20. We encourage to our customers to make the necessary upgrades that ensure security"
So we proceeded to upgrade to that version. Does this mean we will need to upgrade again?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2018 11:39 AM
I agree with TAC that 9.6(1) is vulnerable.
As of this weekend, slides have been made available that detail how to exploit this issue so upgrading to fixed version should be a priority.
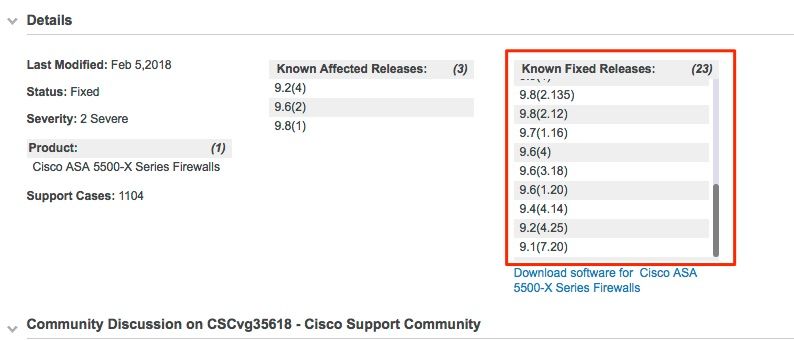
Please see the screenshot below for the versions that are known to be fixed.
Hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2018 11:45 AM
I am already off 9.6.1 ... currently using 9.6.3.20...what i want to confirm if that one is now vulnerable ,,,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2018 11:48 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2018 01:55 PM
Looks like 9.6.3.20 isnt good enough after an update to the bug report.
from tac “Initially, the fix for the issue was on 9.6(3)20 and above. However, after further research, Cisco has identified additional attack vectors and features that are affected by this vulnerability. In addition, it was also found that the original fix was incomplete so new fixed code versions are now available to completely address the vulnerability.
If you want to fully fix the issue on your ASA 5545-X, you will need to upgrade to the version 9.6(4)3.”
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2018 04:41 PM
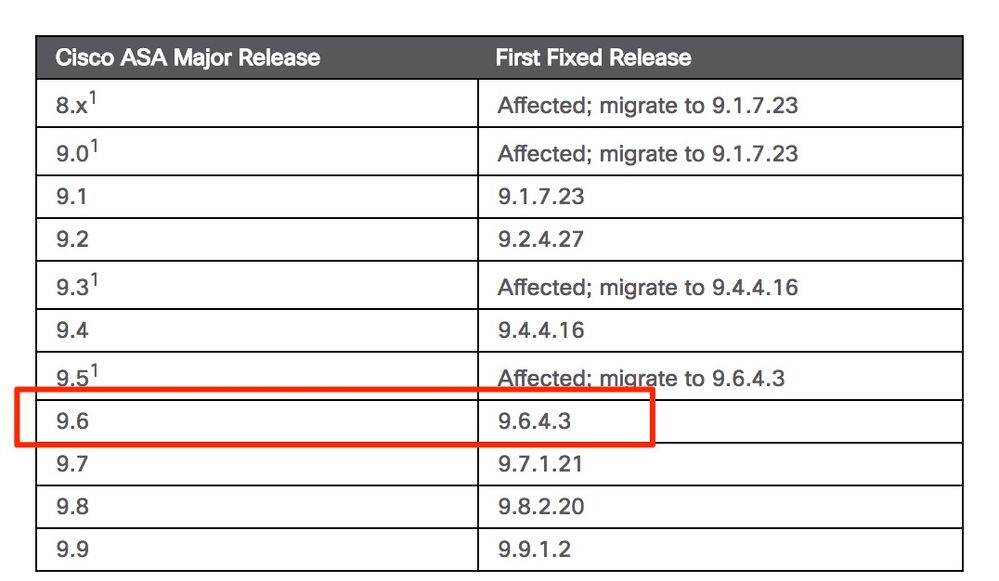
The slides from the Recon Conference are now public and I imagine exploit tools are being created right now.
The PSIRT was updated today. 9.6(3.20) is no longer considered Fixed. For 9.6.x the First Fixed is now 9.6(4.3), see screenshot below. Hope this helps, Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2018 10:33 PM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: