- Cisco Community
- Technology and Support
- Online Tools and Resources
- Cisco Bug Discussions
- Re: CSCvg35618 - Referred 9.9.1.2 not available
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CSCvg35618 - Referred 9.9.1.2 not available
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 05:50 AM - edited 03-20-2019 09:52 PM
Following the webvpn critical security notification is ASA version 9.9 which we use since december also affected. According to Cisco's reference is the first fixed version 9.9.1.2 which isn't available for download (yet).
The only version is 9.9.1 itself from december which is most likely 9.9.1.0,
When will 9.9.1.2 or higher become available?
- Labels:
-
Cisco Bugs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 08:40 AM - edited 01-31-2018 09:33 AM
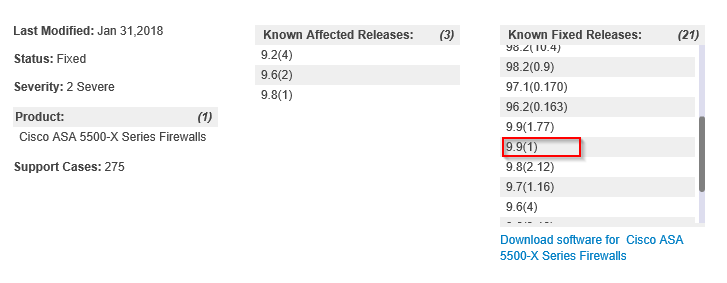
I just opened a TAC case to talk about this same thing and was told 9.9.1.2 is not yet finished and should be out in several days. I was told however that its fixed in 9.9.1 regardless, which according to the link I will paste below is correct but I have no idea which Cisco team to believe. The 9.9.1 release IS shown as a "fixed in" release though. Confusing as hell.
Would like to point out however that the 9.9.1 code was released 17 December 2017 so I HIGHLY doubt its a valid "fixed in" for this bug. Maybe but PROBABLY NOT.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvg35618/?reffering_site=dumpcr
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 09:46 AM
I agree 9.9(1.2) is not available.
I agree that CSCvg35618 is not listed as fixed in the ASA 9.9(1) Release Notes.
However, I'd proffer that Cisco has known about this vulnerability for at least a few months.
The security researcher who discovered this did extensive deep dives into the ASA during the month of September.
Assumptions Below
We can ASSUME that the researcher made Cisco aware of this in the September timeframe because he works for a White Hat Org. Plus, I've seen Fixed Interim versions of ASA OS in Nov 2017 & Dev 2017 (over a full month before we heard about this).
My feeling is that Cisco just issued this PSIRT because the researcher is going to be discussing this vulnerability at a conference in Brussels on Friday Feb 2, 2018.
https://recon.cx/2018/brussels/talks/cisco.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 09:49 AM - edited 01-31-2018 09:50 AM
I was going to say this in the other thread but I will put it in here instead:
Well, crossing my fingers that 9.9(1) fixes this but man I don't trust the vendor. How can I tell management its "probably" resolved? "Maybe" resolved?
Cisco needs to get their act together as this kind of thing removes confidence that they are handling issues correctly and there is really no reason for it. Management and organisational structure failure to have two different messages coming out of the same company about a security issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 09:59 AM
I agree that Cisco needs to get it together. There is an obvious disconnect between the Bug Known Fixed and the PSIRT Known Fixed and the Release Notes Resolved Bugs.
But honestly, it's not the first time. While I love the Bug Search Tool, the data in Bugs frequently isn't as detailed as I would like to see.
HTH, Tim
Please Rate Helpful Posts :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 09:51 AM
Thanks for the info Mr. Glen.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: