- Cisco Community
- Technology and Support
- Networking
- Cisco Catalyst Center
- 9800 WLC netconf failing with DNA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2022 08:31 AM
I am currently on 16.12.7 for the 9800 wlc and DNA is 2.2.2.8. I have netconf configured on the 9800 wlc. DNA discovery netconf is set with port number 830. I am not sure why netconf is not working together.
Solved! Go to Solution.
- Labels:
-
Cisco DNA Center Upgrades
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2022 06:20 AM
Could you provide the output of the following 9800 CLI command:
show run | s aaa
You may not be utilizing the default authZ and default authC methods. NETCONF does not use any other AAA method list except by the default AAA method lists for login and authorization. This does not mean that they must always use local authentication, these can use remote AAA servers instead, but ironically, default method lists are not created by default on any network device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2022 08:50 AM
Hi
Ig you go over the device in inventory> Edit device> Credentials Validate...what do you get on netconfig result?
Did you try to re-discory the device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2022 10:33 AM
After making these changes now am getting CLI Authentication Failure. User is correct its being used on all the devices connected to DNA. I have create that user on the WLC as well and still not able to connect. Netconf is still failing as well. %DMI-5-AUTHORIZATION_FAILED: Chassis 1 R0/0: dmiauthd: User 'xxxx' from xxxxxx:56486 was not authorized for netconf over ssh.
Failing over web for that user as well WEBSERVER-5-LOGIN_FAILED: Chassis 1 R0/0: nginx: Login Un-Successful from host x.x.x.x using crypto cipher 'ECDHE-RSA-AES128-GCM-SHA256'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2022 10:34 AM
Feb 17 18:14:13.085: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: xxxx] [Source: 10.27.16.231] [localport: 22] at 18:14:13 Eastern Thu Feb 17 2022
This was the user name with successful attempt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2022 03:19 PM
SSH into Cisco DNA Center (Username is Maglev / port is 2222) and attempt to ssh directly to the 9800 on port 830 using the following syntax:
ssh -l <9800User> <WLCIP> -p 830
What is the result of this ssh attempt? The user must be authenticated with privilege level 15.
You can also open a TAC case to get an engineer in a WebEx to troubleshoot this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2022 05:58 AM
When ssh -l <9800User> <WLCIP> -p 830 Permission denied. I have level 15 in ISE shell and I can login using ssh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2022 06:20 AM
Could you provide the output of the following 9800 CLI command:
show run | s aaa
You may not be utilizing the default authZ and default authC methods. NETCONF does not use any other AAA method list except by the default AAA method lists for login and authorization. This does not mean that they must always use local authentication, these can use remote AAA servers instead, but ironically, default method lists are not created by default on any network device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2022 06:53 AM
That was the issue once I change the AAA for it. Netconf started to work. Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2022 07:27 AM
Could you please describe what exactly did you change about the AAA method to make it work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2022 11:55 AM
I had this problem too. I did not have default AAA authentication and authorization groups.
I added these:
aaa authentication login default group ISE_GROUP local
aaa authorization exec default group ISE_GROUP local
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2022 03:38 AM
Thank for your configurations.
Which method do you apply on your vty lines : still default or a specific one ?
Because we have this :
aaa authentication login default group TACACS-Test local
aaa authentication login admin-access group TACACS-Test local
aaa authorization exec default group TACACS-Test local if-authenticated
aaa authorization exec admin-access group TACACS-Test local if-authenticated
line vty 0 4
authorization exec admin-access
accounting exec admin-access
login authentication admin-access
length 0
transport input ssh
line vty 5 15
authorization exec admin-access
accounting exec admin-access
login authentication admin-access
transport input ssh
Does it means for NETCONF to work, we have to apply the "default" instead of the "admin-access" under vty lines ?
Thank you in advance for your reply
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 07:52 AM
Hi @Dan Rowe,
Thank you for that information. This is what have had before
aaa authentication login TACAUTH group TACACS_GROUP local
aaa authorization exec TACAUTHZ group TACACS_GROUP local We have modified these 2 line to make netconf auth works
(config)#aaa authentication login default group TACACS_GROUP local
(config)#aaa authorization exec default group TACACS_GROUP local
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2023 05:46 PM
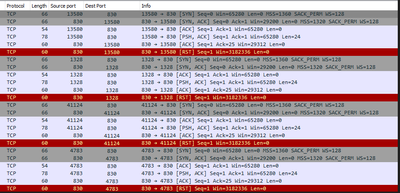
I have the following issue, from DNAC I can logging to the WLC 9800 via SSH but via NETCONF it failed.
I did a tcpdump capture in DNA and I noticed that the Switch is always sending a "Reset" to the connection.
WLC info:
cisco C9800-80-K9
Cisco IOS-XE
ROM: 16.12(5r)
Sw version 17.03.07.
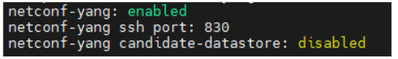
WLC config:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2024 09:54 PM
I got the same issue, ssh on the port 830 geeting refused, I did a packet capture on the WLC and I got the same, TCP RST from the controller, all checks were fine, like netconf-yang enable and all other verification that I have found on other threads.
Linux:~$ ssh 9800-WLC -p 830
ssh: connect to host 9800-WLC port 830: Connection refused
I ran the following command that gave me a light.
show logging profile netconf internal level debug to-file flash:netconf.txt
more netconf.txt
I have found this log:
2024/02/29 04:06:01.106460235 {ncsshd_R0-0}{1}: [tps-client] [2960]: (ERR): Timedout waiting for TPS query response. seqnum: 489
2024/02/29 04:06:01.106463435 {ncsshd_R0-0}{1}: [tps-client] [2960]: (note): Cert chain response, seqnum: 489, resp: 0x0[-1], keyname NULL
2024/02/29 04:06:01.106726536 {ncsshd_bp_R0-0}{1}: [ncsshd] [2630]: (ERR): [pid(2960)] error: Can't find router cert.
2024/02/29 04:06:01.106756036 {ncsshd_bp_R0-0}{1}: [ncsshd] [2630]: (note): [pid(2960)] key name from certificate chain is (null)
2024/02/29 04:06:01.106770036 {ncsshd_bp_R0-0}{1}: [ncsshd] [2630]: (ERR): [pid(2960)] error: get cert chain failed
2024/02/29 04:06:01.106783436 {ncsshd_bp_R0-0}{1}: [ncsshd] [2630]: (ERR): [pid(2960)] error: hostkeys not loaded
After I reacreated the TP-self-signed key, the netconf starts to work again,
Feb 29 05:13:30.300: %PKI-6-TRUSTPOINT_DELETE: Trustpoint: TP-self-signed-30XXXXXX deleted succesfully
Feb 29 05:16:19.650: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: TP-self-signed-30XXXXXX created succesfully
I don´t know if there is a better way to recreate this key, but I did that using the "archive" feature:
conf t revert timer 3
no TP-self-signed-30XXXXXX
After the roolback timer the TP key was recreated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2022 02:24 AM
Please check if you have these two configs in your WLC/Switch :
aaa authentication login default local
aaa authorization exec default local
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: