- Cisco Community
- Technology and Support
- Networking
- Cisco Catalyst Center
- Re: DNAC Certificate - Authority "Self Signed"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DNAC Certificate - Authority "Self Signed"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2019 02:57 AM
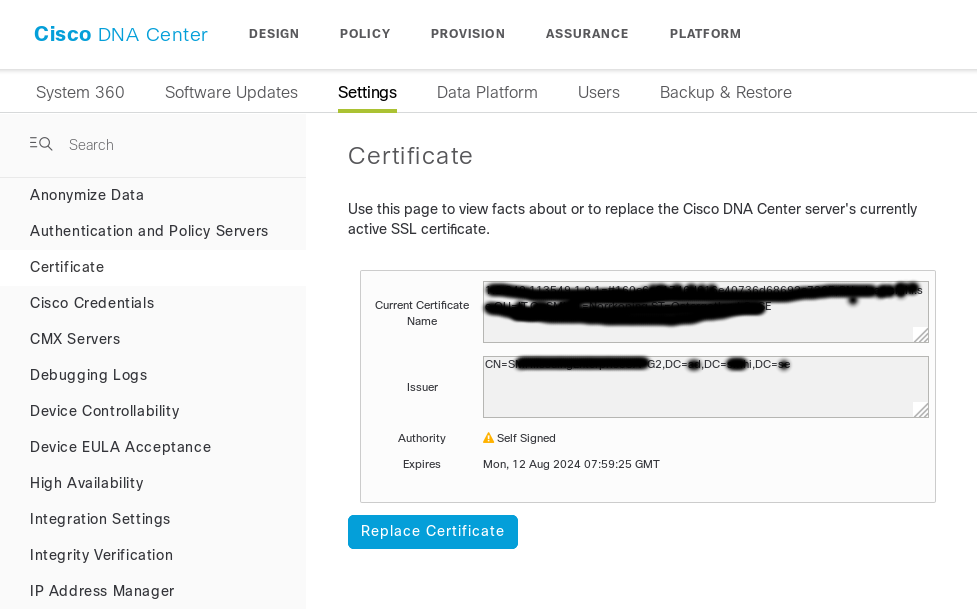
Hi! I am trying to import a certificate to DNAC signed by our internal RootCA. I have followed the guide, but, it is still "self signed" according to DNAC. Guide: https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/dna-center/hardening_guide/b_dnac_security_best_practices_guide.html#d54e1532a1635
I have made a PEM file with "Signed Cisco DNA Center certificate + subordinate CA + RootCA" in it. I can load the cert in correctly, but if I query the API for cert validation: https://dnac.xxxx.se/api/v1/certificate/validate
Response from API: "[SAN check failed, Certificate not signed by trusted CA]"
Can I import the RootCA cert in some way to get DNAC to trust my internal RootCA?
- Labels:
-
Cisco DNA Center
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2019 11:35 AM
Can you please open a TAC case for this so they can investigate? If DNA Center indicated that your certificate was uploaded correctly, then it doesn't make sense that it isn't reflected by the system later on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2019 03:08 AM
Hi! I opened a case via DNA Solution Support and got the response from them that it is a bug and also that there is no ETA on a fix: "There is indeed a bug id but hasn’t been yet released. There is no ETA for this fix yet. And yes, you can treat it as a cosmetic issue."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 11:58 PM
I have the exact same issue and I'm not convinced that it is just a cosmetic issue. Have you tried connecting to your DNA Center on CLI and run any maglev commands?
Like: maglev catalog settings display
For me this fails with the message: ERROR: [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:590)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 09:05 AM
Please open a TAC case and see if they can give you a bug id.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2019 04:43 AM
I found out what the issue was. I ended up reinstalling my DNAC and imported the certificate again. Still got the self-signed issue, but now all the maglev commands from CLI worked so that must have been a different problem.
Next I imported my AD Root certificate into the Trustpool and now everything works. I have not seen this step listed in the best practices guide, but for me at least it was needed. I would have thought that as long as you downloaded the whole cert chain it would automatically import the root certificate into the Trustpool, but it seems like it doesn't do that.
Anyway; it fixed my issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 09:04 AM
Hi robo003c,
TAC is supposed to give you a bug id. I suggest following up with the TAC engineer to ask for that. If there is no bug id, then it's possible the request gets lost, and you'd end up waiting for nothing.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: