- Cisco Community
- Technology and Support
- Networking
- Cisco Catalyst Center
- Re: File transfer using HTTPS and SCP failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
File transfer using HTTPS and SCP failed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 04:44 AM
Hi all!
Trying to update switches OS from DNA UI and receiving this pre-check error:
File transfer using HTTPS and SCP failed
Expected : Device need to have https/scp reachability to Controller
Action : Verify HTTPS/SCP configurations, DNAC certificates on device and protocol reachability
This is switch config:
aaa new-model
aaa authentication login default local
aaa authorization exec default local
hostname DNA-SW-01
ip domain name test.ru
ip http secure-server
ip ssh version 2
ip scp server enable
interface Vlan1
ip address 172.23.84.114 255.255.255.0
DNA ip address is 172.23.84.110. There is no security devices between them.
I can ping switch from DNA CLI, transfer files manually and ssh to switch from DNA.
$ ping 172.23.84.114
PING 172.23.84.114 (172.23.84.114) 56(84) bytes of data.
64 bytes from 172.23.84.114: icmp_seq=1 ttl=254 time=0.544 ms
64 bytes from 172.23.84.114: icmp_seq=2 ttl=254 time=0.437 ms
64 bytes from 172.23.84.114: icmp_seq=3 ttl=254 time=0.456 ms
64 bytes from 172.23.84.114: icmp_seq=4 ttl=254 time=0.475 ms
^C
--- 172.23.84.114 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 0.437/0.478/0.544/0.040 ms
$ ssh admin@172.23.84.114
Password:
DNA-SW-01#quit
Connection to 172.23.84.114 closed by remote host
$ scp ld-linux-x86-64.so.2 admin@172.23.84.114:ld-linux-x86-64.so.2
The authenticity of host '172.23.84.114 (172.23.84.114)' can't be established.
RSA key fingerprint is SHA256:0Va4kQYFYOMmAYiNW89T9Z86llDvXGaLmS9FA8mo69g.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.23.84.114' (RSA) to the list of known hosts.
Password:
ld-linux-x86-64.so.2 100% 159KB 158.8KB/s 00:00
Connection to 172.23.84.114 closed by remote host.
How to fix update error in DNA UI?
- Labels:
-
Cisco DNA Center
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 08:29 AM
what's the DNA center version , Also can you check if the DNA Center certificate is been installed on Network device on which you are trying installation "show running | sec crypto"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 12:12 AM
DNAC Version 1.2.8
Command output from switch below
crypto pki certificate chain DNAC-CA
certificate ca 00E99FCCE66D61F2AA
308202F7 308201DF A0030201 02020900 E99FCCE6 6D61F2AA 300D0609 2A864886 ....
It's quite strange but after two days it started to work. With no changes at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2021 11:31 AM - edited 03-16-2021 11:32 AM
Just want to help anyone out that was going through this as well. I spent several hours trying to solve this and I think I finally got it.
1. All of my devices either failed HTTPS and succeeded on SCP, or failed both. I couldn't understand why SCP worked on some switches but not others. The answer was the ip ssh version 2 was configured on the switches that worked. I added this to the switches that were failing over SCP and they started working.
So now I could actually deploy the images and upgrade them. The problem was then that SCP was painfully slow. So I ended up getting HTTPS to work.
2. For HTTPS to succeed the switches need to have the cert of DNAC installed locally. The easiest way to do this is to obtain the PEM file from DNAC itself http://<dnac>/ca/pem then open it in notepad.
Now login to the switch and remove the DNAC-CA as a trustpoint if it already exists (for some reason I had a DNAC-CA cert on some of my switches but apparently it was not the correct cert)
no crypto pki trustpoint DNAC-CA
Now re-configure the trustpoint:
crypto pki trustpoint DNAC-CA
enrollment mode ra
enrollment terminal
usage ssl-client
revocation-check none
exit
Now add in the certficate:
crypto pki authenticate DNAC-CA
*paste in the cert from the PEM file that you have open in notepad*
At this point you should be able to successfully reach the DNAC over its IP, you can test it out with this command:
copy https://<dnac-ip>//core/img/cisco-bridge.png flash:
Now when you do an image readiness check, you should see HTTPS succeeding. In my case, using HTTPS resulted in a 10 minute transfer, while SCP was 47 minutes.
Notes:
You do not need to enable HTTPS or SCP server on the switch itself. The switch is not running the server, it is acting as the client in the HTTPS or SCP file transfer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2021 03:47 PM
@andrewohanian When Cisco DNA is managing a device, you will benefit from not having to reconfigure things on the device console on your own. It is often automated for you. When it comes to certificates, a new certificate will be pushed to all network devices when it's updated in the Cisco DNA settings. If for some reason that doesn't work, you can also try provisioning the device or updating telemetry settings.
A bad certificate is the most common reason for HTTPs SWIM upgrades to fail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 08:38 AM
What fixed the same issue for me was simply adding a DNS server to the switches config.
Commands were:
conf t
ip name-server <IP address of our DNS server 1> <IP address our DNS server 2> <IP address of our DNS server 3>
do wr
end
I hope this helps someone out there.
Seif Allaoua | LinkedIn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 02:51 AM
I found the issue was with CRL checking on the DNAC trustpoint.
After manually applying this config update Http copy worked:
crypto pki trustpoint DNAC-CA
revocation-check none
I'm using DNAC 2.2.2.9 .... hopefully this is fixed in a later version... in the meantime I'll update the provisioning template we use on all devices to automate this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
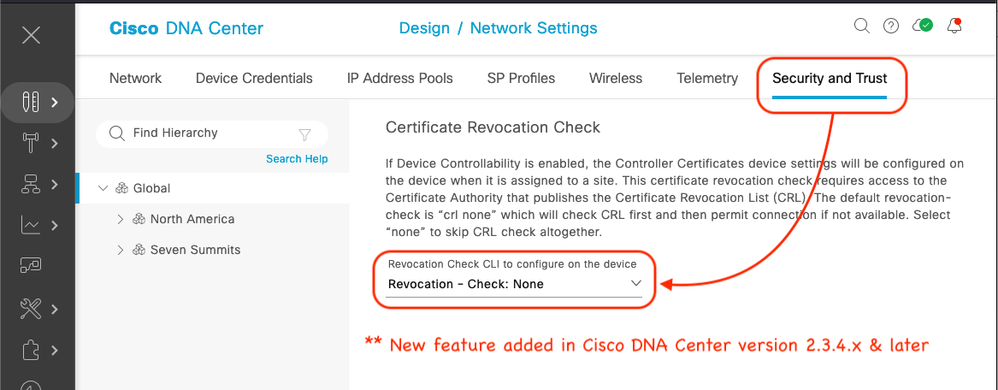
11-11-2022 07:59 AM
Just an FYI:
Design / Network Settings / Security and Trust
** New feature added in Cisco DNA Center version 2.3.4.x & later
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: