- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Applications
- Re: CUBE - Wildcard certificates
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CUBE - Wildcard certificates
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 04:59 AM
Hi,
Kindly requesting your input to on my attempt to install the wildcard certificates on a CUBE. I will be using this for MS team direct routing testing. Please find the steps and commands that i used in this.
Configured the trustpoint.
crypto pki trustpoint sbcssl
enrollment terminal
fqdn none
subject-name cn=*.mydomain.net
Placed the root certificate chain
crypto pki authenticate sbcssl
<<paste the certificate chain here >>
paste the certificate and private key
crypto pki import sbcssl certificate
<<paste the private key and then certificate >>
received the error: Cannot import certificate -
Certificate does not contain router's General Purpose public key for trust point sbcssl
please note that i am using the wildcard certificate and private key provided. I didnt generated the CSR from the CUBE router. If i remember correctly, i read it below URL that wildcard certificate worked in the MS direct routing setup. so i would like to try it from my end.
reference: Cisco ISR 4321 SBC for MS Teams Direct Routing
Please let me know if anyone can shed some light on it.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 05:49 AM - edited 08-17-2021 07:10 PM
I assume its the problem with the key. Use CSR to generate the wildcard cert. I hope it could resolve the issue.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 05:52 AM
Thanks for your reply.
I would like to get the wildcard certificate corrected if that is a possible option. Is it possible for you to verify the steps that i mentioned is correct or not?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 07:23 PM - edited 08-17-2021 07:24 PM
Below mentioned are the steps for signing a router certificate.
1) Generate the keypair
2) Create the trustpoints
3) Generate CSR (Certificate Signing Request)
4) Obtain public signed SSL/TLS certificate
5) Import certificate to trustpoint
Note sure if we can upload the private key. I assume that you didnt do the step 1 and step 3 mentioned above.
Generate CSR and use the same CSR for downloading your wildcard certificate.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2021 02:03 PM
Hello,
Not sure if you've seen this video or not, but I've used it once or twice to refresh myself on the process:
https://www.youtube.com/watch?v=IVH5PdPsQyw
I haven't done any wildcard certificates with Teams Direct Routing (yet), but on page 54 in the Direct Routing for Microsoft Phone System with Cisco CUBE doc, a CSR is generated after the RSA keys and Trust Points configured in this example. It might be that you have to do the same here too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2022 04:45 AM - edited 01-12-2022 04:48 AM
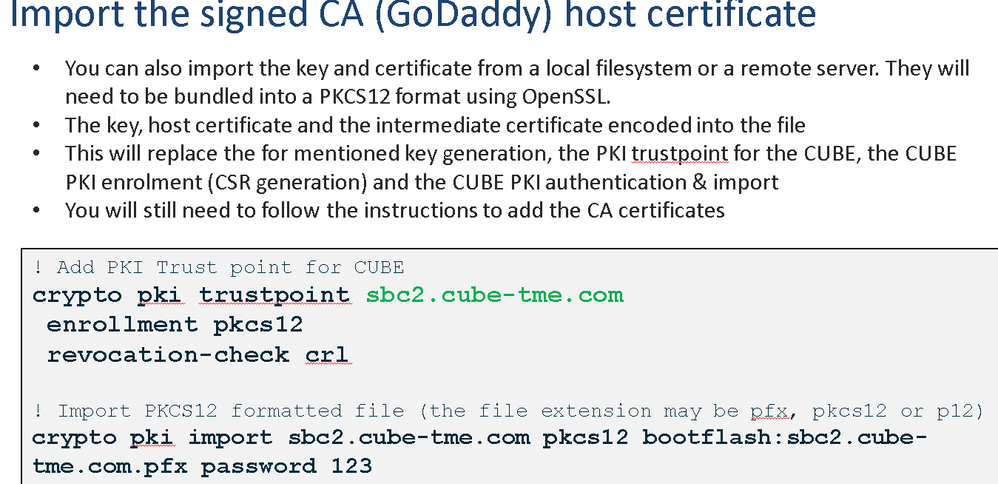
Unfortunately the direct routing documentation does not provide a clear example when we are not generating a certificate csr on the cisco cube and thus are not generating a private key.
However it should be possible to import the private key/signed certificate when bundled in .pkcs12 format, if the pfx file is uploaded to the router flash and imported as per the bellow screenshot:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-03-2023 12:20 PM
I am attempting to import our wildcard certificate but I am getting a Message that states:
% Importing pkcs12...
Source filename [wlcd_xxx_com_new_pw_2023_11.pfx]?
Reading file from bootflash:wlcd_xxx_com_new_pw_2023_11.pfx% You already have RSA keys named padsbc.xxx.com
% If you replace them, all router certs issued using these keys
% will be removed.
% Do you really want to replace them? [yes/no]: yes
% Warning: CA cert is not found. The imported certs might not be usable.
CRYPTO_PKI: Import PKCS12 operation failed to create trustpoint padsbc.xxx.com
I have tried to install the Root CA from DigiCert that the certificate is signed by but not having any luck with that either.
Please advise,
Joe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2024 06:54 AM
Recently I was working with customer to integrate CUCM and Microsoft Teams using Microsoft Teams Direct Routing. In this case, we used their existing wildcard certificate. Here is the process:
1. Do not generate any CSR on CUBE Router.
2. Customer must combine their existing Root CA, Intermediate CA, Wildcard Certificate and Private Key in single PKCS12 bundle. For more details, refer to this post here. This is the single file you need to import on CUBE Router.
3. Copy this file from FTP/SFTP to CUBE Router flash. For example:
copy ftp://<username>:<password>@<x.x.x.x>/wildcard.pfx flash:
Destination filename [wildcard]?
Accessing ftp://*:*@<x.x.x.x>/wildcard.pfx...!
[OK - 4931/4096 bytes]4. Using the below command, import the wildcard certificate to CUBE. This will automatically create the trustpoint “WILDCARD_TP”.
crypto pki import WILDCARD_TP pkcs12 flash:wildcard.pfx password ******* %
Importing pkcs12...
Source filename [wildcard.pfx]?
Reading file from bootflash:wildcard.pfx
CRYPTO_PKI: Imported PKCS12 file successfully.5. Show running configuration can be used to verify the trust point.
crypto pki trustpoint WILDCARD_TP
enrollment pkcs12
revocation-check none
rsakeypair WILDCARD_TP
!
crypto pki certificate chain WILDCARD_TP
30820676 3082055E A0030201 02021006 245011EF 815DF299 C14D422D AC6F9830
0D06092A 864886F7 0D01010B 05003060 310B3009 06035504 06130255 53311530
13060355 040A130C 44696769 43657274 20496E63 31193017 06035504 0B131077
77772E64 69676963 6572742E 636F6D31 1F301D06 03550403 13164765 6F5472755. Show crypto pki certificates can be used to display information about the wildcard certificate and the certificate of the CA.
CUBE_ROUTER#sh crypto pki certificates WILDCARD_TP
Certificate
Status: Available
Certificate Serial Number (hex): 00D868B5A81343A259
Certificate Usage: General Purpose
Issuer:
cn=Go Daddy Secure Certificate Authority - G2
ou=http://certs.godaddy.com/repository/
o=GoDaddy.com Inc.
l=Scottsdale
st=Arizona
c=US
Subject:
Name: *.example.com
cn=*.example.com
ou=Domain Control Validated
CRL Distribution Points:
http://crl.godaddy.com/gdig2s1-2592.crl
Validity Date:
start date: 22:36:28 UTC Jan 6 2021
end date: 22:36:28 UTC Jan 6 2022
Associated Trustpoints: WILDCARD_TP
Storage: nvram:GoDaddySecur#A259.cer
CA Certificate
Status: Available
Certificate Serial Number (hex): 07
Certificate Usage: Signature
Issuer:
cn=Go Daddy Root Certificate Authority - G2
o=GoDaddy.com Inc.
l=Scottsdale
st=Arizona
c=US
Subject:
cn=Go Daddy Secure Certificate Authority - G2
ou=http://certs.godaddy.com/repository/
o=GoDaddy.com Inc.
l=Scottsdale
st=Arizona
c=US
CRL Distribution Points:
http://crl.godaddy.com/gdroot-g2.crl
Validity Date:
start date: 07:00:00 UTC May 3 2011
end date: 07:00:00 UTC May 3 2031
Associated Trustpoints: WILDCARD_TP
Storage: nvram:GoDaddyRootC#7CA.cer
6. Specify the default trust point under sip-ua.
sip-ua
crypto signaling default trustpoint WILDCARD_TP
Thanks, Vaijanath S.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: