The new Cisco Meeting Server 3.8 version supports a new feature Survey, it allows the user hosting a conference or a space to create a survey in a meeting and invite the participants to take part i...
Create two SIP Trunk Security Profiles to listen on different SIP port for Call Recording 5070 and Auto Attendant 5062.
Create two SIP Profiles.
Create two SIP Trunk.
The first SIP Trunk will be ...
The "Fresh Install with Data Import (V2V)" feature is an alternative method for DRS Disaster Recovery System. Basically the DRS allows the admin to take a backup of a Cisco Unity Connection node. The...
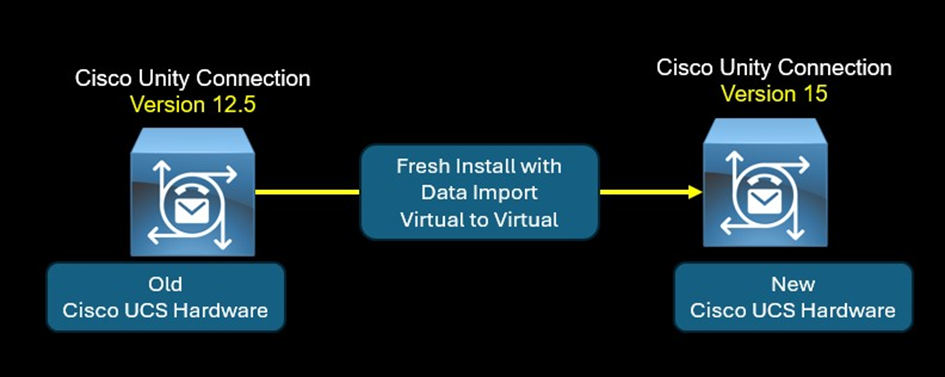
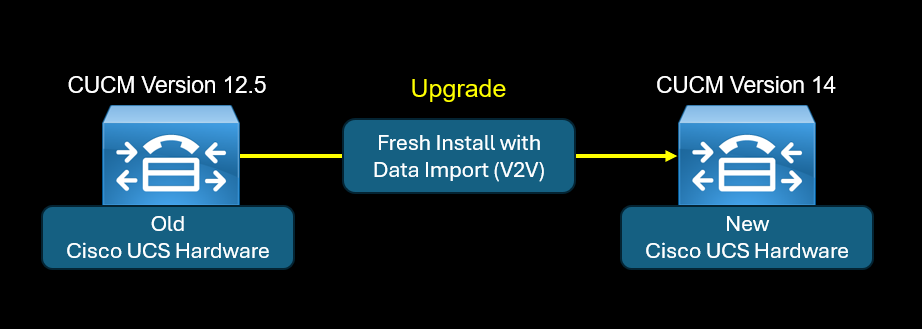
The "Fresh Install with Data Import (V2V)" feature is an alternative method for DRS Disaster Recovery System. Basically the DRS allows the admin to take a backup of a CUCM node. The DRS backup is u...
With the introduction of Cisco Webex Calling in the CCNP Collaboration Certification (CLCOR, CLACCM, CLICA and CLCEI),
These changes are reflected in the v1.1 blueprints by including, Webex App, Webex...

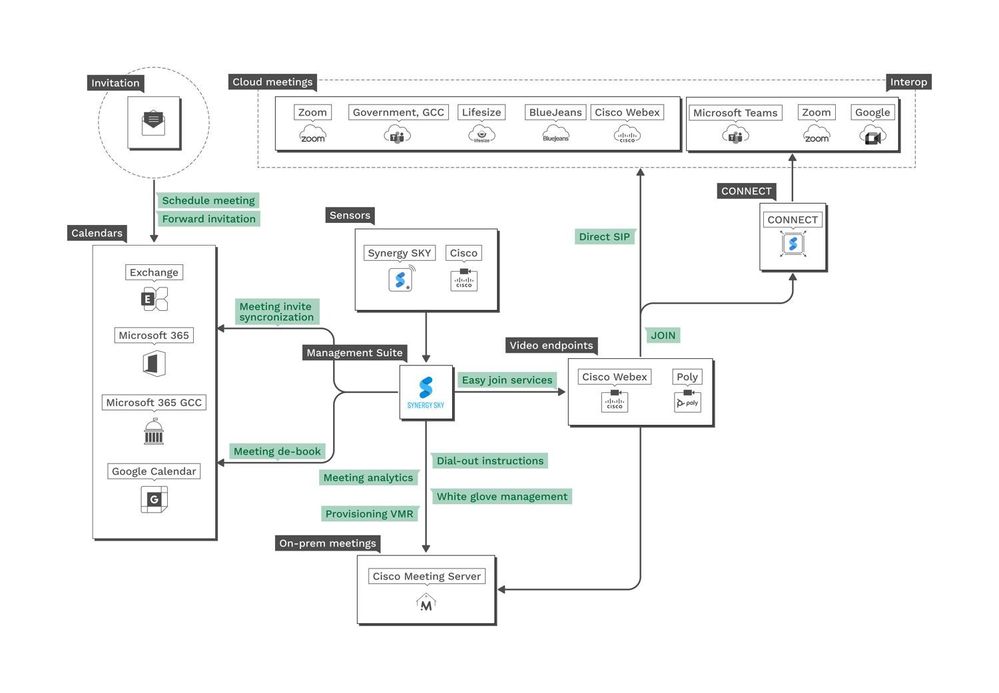
With disparate and heterogeneous Video Conferencing Ecosystems, The interoperability became a challenge for customers, as an example I read recently is : Nissan North America one of the biggest automo...
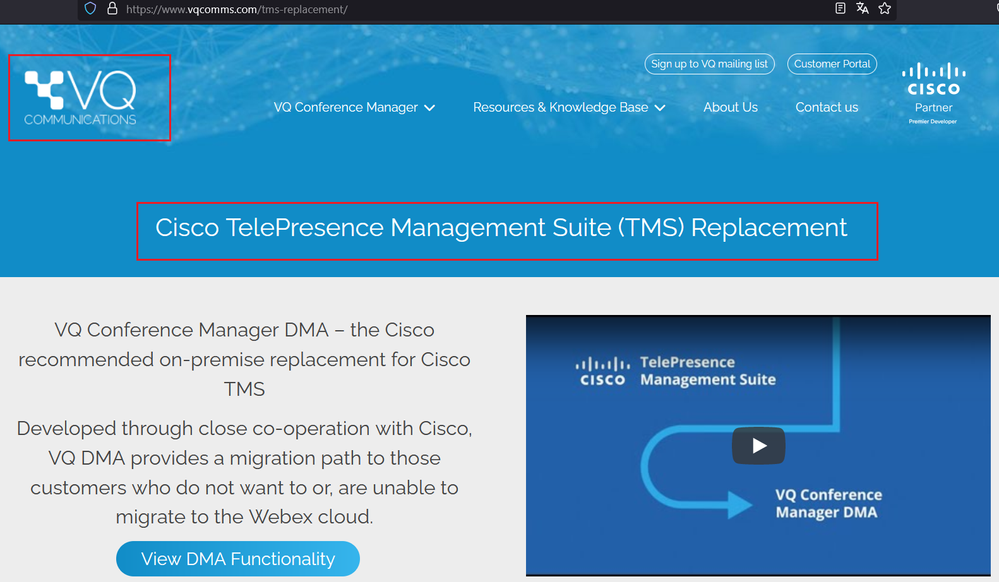
End-of-Sale and End-of-Life Announcement for the Cisco Telepresence Management Suite (TMS) and Exchange Integration (XE)
TMS and TMSXE will no longer be included in Subscription offers. Existing cu...
Security and Visibility with Webex Teams is now mandatory and a challenge for customers and end users.
Cloud access security broker (CASB) is an on-premises or a cloud-based software that sits between...
The call classification on Webex Calling determines whether a call is originating from an on-net source like on-premise PBX or from the PSTN, the concept is similar to Offnet and Onet Classificatio...

Join the ranks of some of the best, brightest, and most passionate technologists. The 2024 Cisco Champion application is now open. Apply by January 12, 2024.
As a Cisco Champion, you will:
Get early ...

In Webex Calling the routing behavior for unknown numbers is controlled by two settings. The enterprise level “Unknown Number Handling” setting and the “Calls to On-Premises Extension” setting at the ...
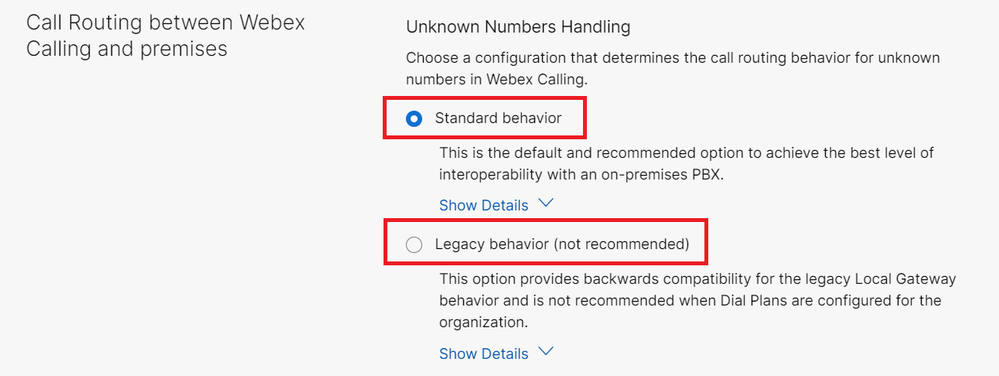
Webex Calling Call Routing Components
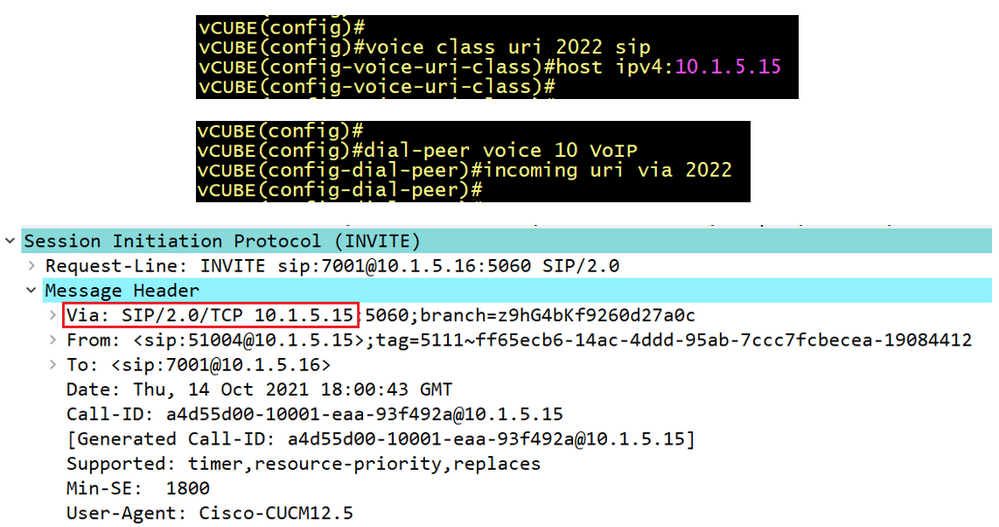
In CUCM a route pattern is a string of numbers that CUCM uses to determine where to route calls. The call can be either inter-site to another Cisco UCM Cluster o...

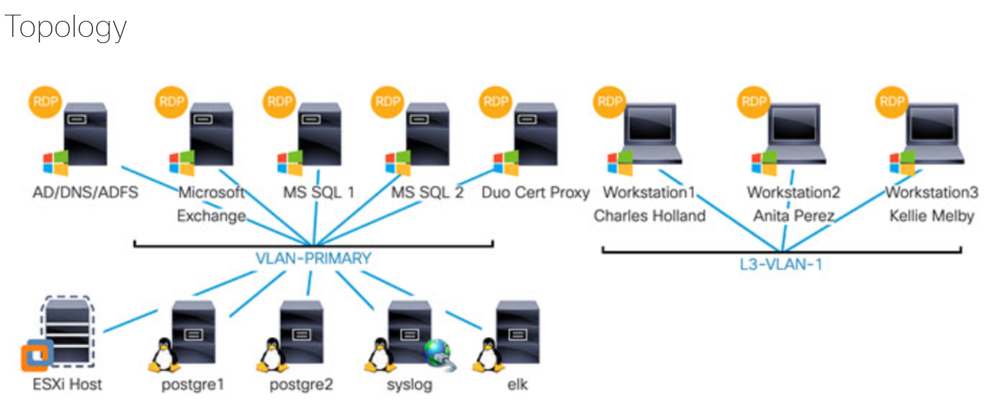
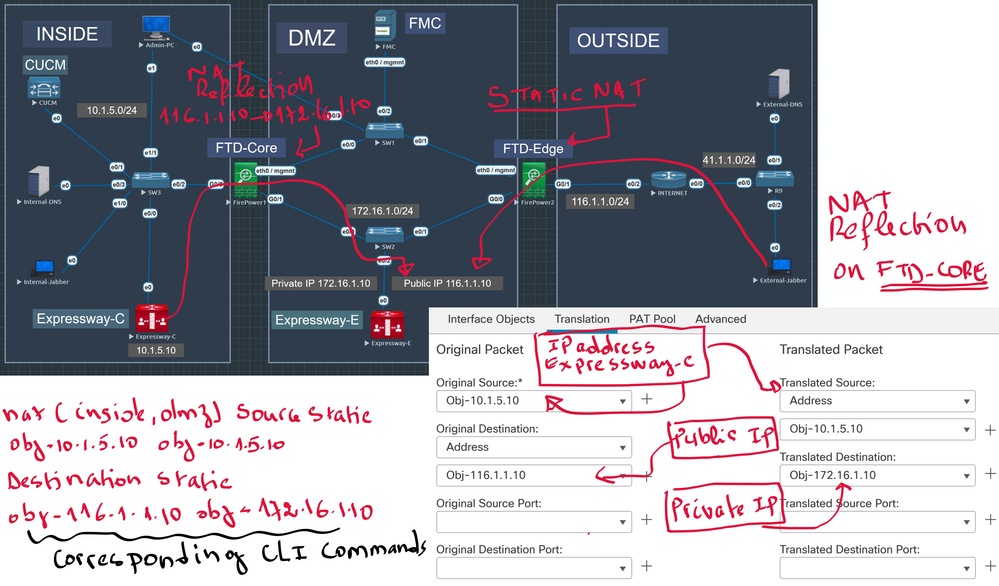
NAT Reflection is a method that allows communication of internal PCs to access DMZ Server using the Public IP Address of the server instead of the Private IP Address. One of the common use case is Cis...
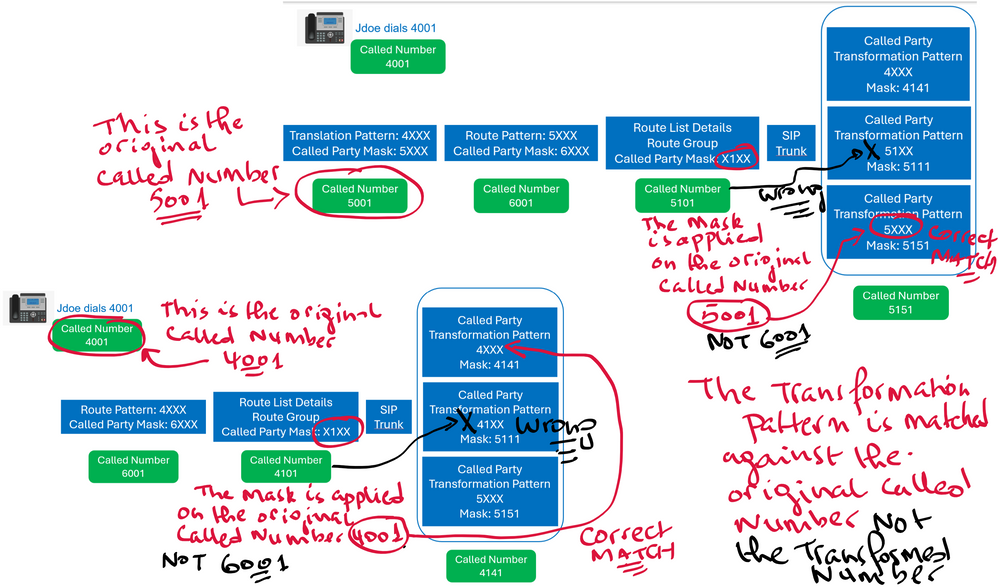
On Cisco Unified CM, multiple points and levels are availables to do Digits Manipulation, offering more granularity and flexibility, especially for outbound calls, the Called or the Calling parties ca...