- Cisco Community
- Technology and Support
- Collaboration
- Contact Center
- UCCX 11.6 SSO with Azure as IDP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 12:13 AM
i've been testing UCCX 11.6 SSO with Azure as IDP, there is no real document available which gives the steps to perform on Azure side, i found a document for CuCM, which worked with CuCM at the first attempt, i thought to replicate it for UCCX , taking below points under consideration from SRND
The following are the expectations from SAML Response:
• The entire SAML response (message and assertion) is signed or only the message is signed but not the
SAML assertion alone is signed.
• SAML Assertion must not be encrypted.
• SAML response must be signed using SHA-128.
• NameIDFormat in SAML response must be urn:oasis:names:tc:SAML:2.0:named-format:transient.
• uid and user_principal attributes should be present in SAML assertion in the AttributeStatement section.
The "uid" attribute value must be the user Id using which users log in to Cisco contact centre applications
that are SSO enabled and the "user_principal" attribute value must be in uid@domain format.
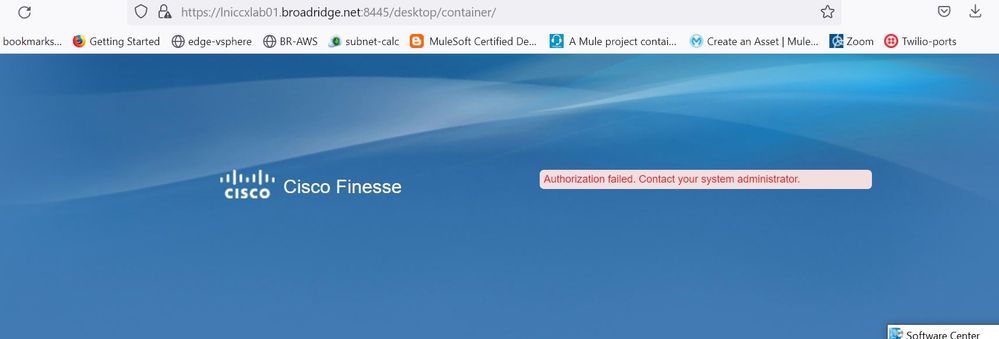
My SSO test on UCCX has been successful, then no problem when i enable it from UCCX admin page, also am able to get in to GUI using SSO, CuIC as well, but not on finesse. On cisco finesse i keep getting below error
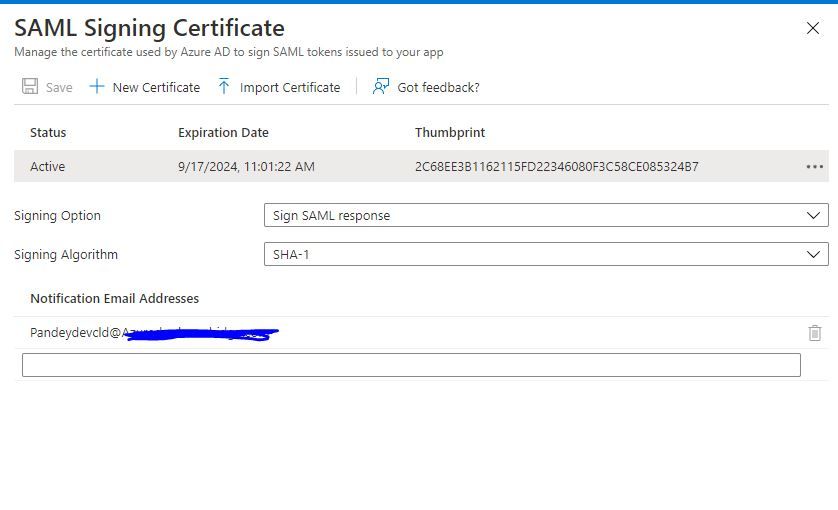
below is my SAML signing config from Azure side
Not sure if it is a bug, while setting up SSO i faced this bug which i found on google for ucce, then i asked TAC to perform the workaround:https://quickview.cloudapps.cisco.com/quickview/bug/CSCvm57749
Solved! Go to Solution.
- Labels:
-
Other Contact Center
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2021 12:12 PM
the issue was of case-sensitivity, as soon as i matched it with Azure, it fixed the issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2021 12:12 PM
the issue was of case-sensitivity, as soon as i matched it with Azure, it fixed the issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 02:18 PM
Hi Ravi,
Can you tell what certificate you are using and what kind of the user claim you are using.
I have tried signing response with configuration as per your screenshot, and user claim below
default = user.onpremiseprinciple
uid = user.onpremisesamaccount
user_principle = user.onpremiseprinciple
Still not able to pass the SSO test.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2021 11:12 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2021 01:02 AM
Thanks Ravi,
I will try the user claim by your suggestion below:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: