- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Re: Need Help with Nexus Switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2020 03:06 PM
Dear Community Members ,
Thanks for all of you who have been supported through the years as i have used the support community frequently .
As of now i am a new into Nexus switch .
My scnario is (is very critical for me to do the configuration )
we have:
N9K-C9348GC-FXP qty =2.
N9K-C93180YC-FX qty=2.
one Firewall routed to internet and connected with nexus switch .
What are the confiuration needed , knowing that we have only a single vlan on the network (vlan 5) that needed to be routed to firewall (internet).
I know that this kind of general question but i dont know what to do .
Note switches are connected with its same model as VSS and to other switch using etherchannel .
Will be eagerly waiting for your help
Thanks
Mansour
Solved! Go to Solution.
- Labels:
-
Nexus Series Switches
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 02:24 PM
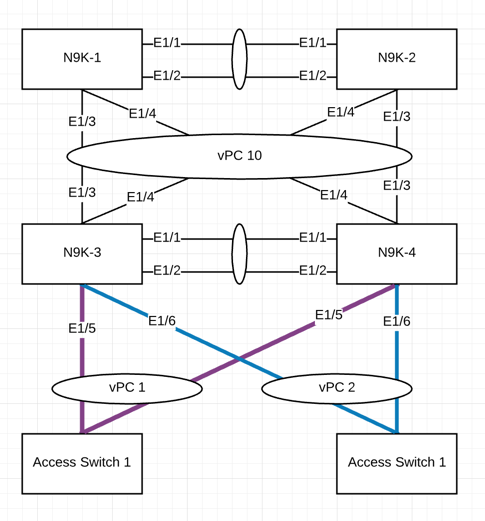
Below the design updated
I haven't put the management interfaces on this design. I assume you connected your Nexus management interface to an OOB switch (or any switch) and subnet used for OOB is 192.168.99.0/24.
I will also create a vlan 10 L3 interface with HSRP to show how to do it in the default vrf.
These configs are a sample to show you how to do a simple config but I highly recommend you take a look at Cisco documentations.
Configuration of N9K-1 to build vpc peer-link (and related config).
feature lacp
feature vpc
!
vlan 10
name test-vlan-10
vlan 20
name test-vlan-20
vlan 30
name test-vlan-30
vlan 40
name test-vlan-40
!
vrf context management
ip route 0.0.0.0/0 192.168.99.1
!
interface mgmt0
vrf member management
ip address 192.168.99.247/24
!
vpc domain 1
peer-switch
role priority 20
peer-keepalive destination 192.168.99.248 source 192.168.99.247 vrf management
delay restore 150
peer-gateway
auto-recovery reload-delay 360
ip arp synchronize
!
spanning-tree vlan vlan-range priority 4096
!
interface Ethernet1/1
switchport
switchport mode trunk
channel-group 1 mode active
no shutdown
!
interface Ethernet1/2
switchport
switchport mode trunk
channel-group 1 mode active
no shutdown
!
interface port-channel1
switchport
switchport mode trunk
spanning-tree port type network
vpc peer-link
!
int vlan 10
ip address 10.10.10.2/24
hsrp 10
ip 10.10.10.1
preempt
priority 105
no shut
Configuration of N9K-2 to build vpc peer-link (and related config).
feature lacp
feature vpc
!
vlan 10
name test-vlan-10
vlan 20
name test-vlan-20
vlan 30
name test-vlan-30
vlan 40
name test-vlan-40
!
vrf context management
ip route 0.0.0.0/0 192.168.99.1
!
interface mgmt0
vrf member management
ip address 192.168.99.248/24
!
vpc domain 1
peer-switch
role priority 40
peer-keepalive destination 192.168.99.247 source 192.168.99.248 vrf management
delay restore 150
peer-gateway
auto-recovery reload-delay 360
ip arp synchronize
!
spanning-tree vlan vlan-range priority 4096
!
interface Ethernet1/1
switchport
switchport mode trunk
channel-group 2 mode active
no shutdown
!
interface Ethernet1/2
switchport
switchport mode trunk
channel-group 2 mode active
no shutdown
!
interface port-channel2
switchport
switchport mode trunk
spanning-tree port type network
vpc peer-link
!
int vlan 100
ip address 10.10.10.3/24
hsrp 10
ip 10.10.10.1
preempt
no shut
For N9K-3 and N9K-4, you could do the same as previously but you need to change their management IPs and adapt it into the vpc domain section. Also you need to use another vpc domain. For example N9K-1 and 2 are using VPC domain 1, so use VPC-domain 2. You will also have to change the spanning-tree priority. Instead of 4096, put 8192 on the config to N9K-3 & 4.
L3 interface can be created on N9K-3 & 4 but not mandatory, depends where you want to do routing.
You see there're are some VPCs.
Below how to create a VPC. I'll do it for 1 and let you apply the same logic for others:
Let's configure VPC 10 on N9K-1 & 2.
N9K-1:
interface E1/3
switchport
switchport mode trunk
channel-group 10 mode active
!
interface E1/4
switchport
switchport mode trunk
channel-group 10 mode active
!
interface port-channel 10
switchport
switchport mode trunk
vpc 10
!
N9K-2:
interface E1/3
switchport
switchport mode trunk
channel-group 10 mode active
!
interface E1/4
switchport
switchport mode trunk
channel-group 10 mode active
!
interface port-channel 10
switchport
switchport mode trunk
vpc 10
!
This logic applies to every VPC.
I used trunk interfaces but you can use access depending on where the VPC are connecting to. Usually trunk between Nexus switches to other Nexus or between Nexus to access switches. When connecting to servers, it depends if servers are using dot1q tags or not.
Hope this will help you start
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 08:07 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2020 06:40 PM
You have only 1 vlan routed by the firewall which means your nexus switches will act as simple L2 switches.
Is it the final design or are seeking to do a new design?
You said you connected them in vss and i believe you meant vpc.
Can you share the topology you have in place because based on what you’re saying the configuration will be very basic.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 11:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 07:14 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 12:36 AM
Francesco Thanks for the reply again .
Can you please advice regrading the missing link .
BR,Mansour
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 08:33 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 10:38 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 02:24 PM
Below the design updated
I haven't put the management interfaces on this design. I assume you connected your Nexus management interface to an OOB switch (or any switch) and subnet used for OOB is 192.168.99.0/24.
I will also create a vlan 10 L3 interface with HSRP to show how to do it in the default vrf.
These configs are a sample to show you how to do a simple config but I highly recommend you take a look at Cisco documentations.
Configuration of N9K-1 to build vpc peer-link (and related config).
feature lacp
feature vpc
!
vlan 10
name test-vlan-10
vlan 20
name test-vlan-20
vlan 30
name test-vlan-30
vlan 40
name test-vlan-40
!
vrf context management
ip route 0.0.0.0/0 192.168.99.1
!
interface mgmt0
vrf member management
ip address 192.168.99.247/24
!
vpc domain 1
peer-switch
role priority 20
peer-keepalive destination 192.168.99.248 source 192.168.99.247 vrf management
delay restore 150
peer-gateway
auto-recovery reload-delay 360
ip arp synchronize
!
spanning-tree vlan vlan-range priority 4096
!
interface Ethernet1/1
switchport
switchport mode trunk
channel-group 1 mode active
no shutdown
!
interface Ethernet1/2
switchport
switchport mode trunk
channel-group 1 mode active
no shutdown
!
interface port-channel1
switchport
switchport mode trunk
spanning-tree port type network
vpc peer-link
!
int vlan 10
ip address 10.10.10.2/24
hsrp 10
ip 10.10.10.1
preempt
priority 105
no shut
Configuration of N9K-2 to build vpc peer-link (and related config).
feature lacp
feature vpc
!
vlan 10
name test-vlan-10
vlan 20
name test-vlan-20
vlan 30
name test-vlan-30
vlan 40
name test-vlan-40
!
vrf context management
ip route 0.0.0.0/0 192.168.99.1
!
interface mgmt0
vrf member management
ip address 192.168.99.248/24
!
vpc domain 1
peer-switch
role priority 40
peer-keepalive destination 192.168.99.247 source 192.168.99.248 vrf management
delay restore 150
peer-gateway
auto-recovery reload-delay 360
ip arp synchronize
!
spanning-tree vlan vlan-range priority 4096
!
interface Ethernet1/1
switchport
switchport mode trunk
channel-group 2 mode active
no shutdown
!
interface Ethernet1/2
switchport
switchport mode trunk
channel-group 2 mode active
no shutdown
!
interface port-channel2
switchport
switchport mode trunk
spanning-tree port type network
vpc peer-link
!
int vlan 100
ip address 10.10.10.3/24
hsrp 10
ip 10.10.10.1
preempt
no shut
For N9K-3 and N9K-4, you could do the same as previously but you need to change their management IPs and adapt it into the vpc domain section. Also you need to use another vpc domain. For example N9K-1 and 2 are using VPC domain 1, so use VPC-domain 2. You will also have to change the spanning-tree priority. Instead of 4096, put 8192 on the config to N9K-3 & 4.
L3 interface can be created on N9K-3 & 4 but not mandatory, depends where you want to do routing.
You see there're are some VPCs.
Below how to create a VPC. I'll do it for 1 and let you apply the same logic for others:
Let's configure VPC 10 on N9K-1 & 2.
N9K-1:
interface E1/3
switchport
switchport mode trunk
channel-group 10 mode active
!
interface E1/4
switchport
switchport mode trunk
channel-group 10 mode active
!
interface port-channel 10
switchport
switchport mode trunk
vpc 10
!
N9K-2:
interface E1/3
switchport
switchport mode trunk
channel-group 10 mode active
!
interface E1/4
switchport
switchport mode trunk
channel-group 10 mode active
!
interface port-channel 10
switchport
switchport mode trunk
vpc 10
!
This logic applies to every VPC.
I used trunk interfaces but you can use access depending on where the VPC are connecting to. Usually trunk between Nexus switches to other Nexus or between Nexus to access switches. When connecting to servers, it depends if servers are using dot1q tags or not.
Hope this will help you start
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 02:37 PM
Thanks so much Frances.
A great explanatory for someone new to the filed of nexus switches and a great way to start .
For internet connectivity all i have to do is to create layer3 vlan with ip address on the inside interface of the internet and do static route ,Right ?
Thanks so much to put this much time helping who needs your expertise and information .
BR,Mansour
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 08:07 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 11:55 PM
Hello,
it depends on your design. You can use Static Route or BGP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 02:40 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide