- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Nexus 5600 and L2 Firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Nexus 5600 and L2 Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2018 05:34 AM
Hi there.
I have a Cisco Nexus 5600 switch and Fortigate 1500 firewall witch is working in transparent L2 mode.
The scenario is :
Nexus 5600 is my server's Gateway. for instance : (Vlan 1010 and SVI = 10.0.245.1/24)
Servers are configured in different VLAN like Vlan 1020, but obviously have same range IP address. (10.0.245.100/24)
Fortigate L2 firewall does vlan bridging here. It receives traffics from Vlan 1010 and changes to Vlan 1020 and vice versa. So, we sure all traffics pass through the L2 Firewall. We've implemented this scenario frequently in our Sites and we've never had any problem with CAT6500, Cat4500, Cisco 3750, 3850 as well as 2960 access switches. Unfortunately, we've recently faced to this problem in Nexus platform. Does anyone have idea about this challenge?
NX-OS version : 7.3.3.N1
- Labels:
-
Data Center Networking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2018 10:05 AM
Hello Vahid,
Can you tell us what the problem actually is?
I cannot get it from your post.
Thanks,
ADP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2018 12:40 AM
Hi.
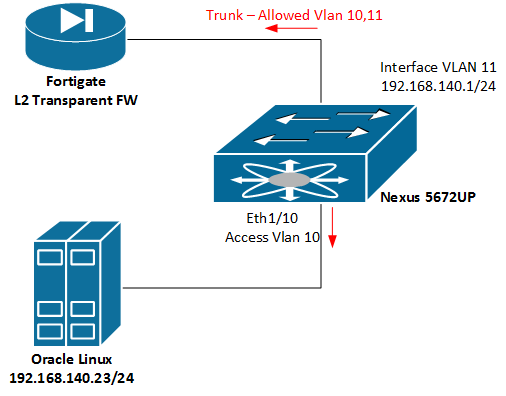
Let me explain the problem from a very simple example as it shown above. We have an Oracle DB which has the IP address of 192.168.140.23/24. The gateway is a SVI defined on nexus switch. (140.1)
Now, We are going to configure a L2 transparent firewall in order to check traffic passing between server and it's GW. Therefor we'll put server in different VLAN (VLAN 10) from Gateway. (VLAN 11), So that they are not able to communicate directly with each other. Since the interface towards the Firewall has been configured as trunk port and vlan 10 and 11 are allowed to pass, It will receive the traffic from both switch and server. Then it changes the vlan 10 to 11 and vice versa, So server would be able to access to it's gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2018 02:23 AM
Hello Vahid,
Are you looking for configuration advice or do you have this in production and it doesn't work? Cause you are mentioning a problem but you never told us what the problem actually is.
To my eyes the solution will work, just make sure that the vlan 10 doesn't have an SVI configured on the Nexus. The SVI must be only on vlan 11.
If I didn't get your question right once more please try to be more specific, not on describing the topology, but on letting us know what you would like to know.
ADP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2018 02:55 AM
Hi.
The scenario doesn't work in Nexus 5600. but in all platforms we've ever had, it does. When we check ARP in nexus, It has the server ARP record, but no any other protocol, such as PING, works. However an any to any permit policy has been configured in firewall. A strange thing in nexus is that, when we enable debug for these protocols, nothing shown!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2018 04:41 AM
Ok now it's more clear.
What about the server? does it have the SVI 11 arp entry (Linux: "arp -an")?
Do the following so we can see where this stops:
- Start a ping from the Nexus toward the Server, doesn't matter if it doesn't work. Put a high count on the ping so you will have all the time for the following capture..
- While you ping do a packet capture on the Fortigate to see if packets are flowing from one interface to the other? (diag sniffare packet any "icmp and host 192.168.140.23" 4 0) (4 0 are used to print the packet interface and direction)
- On the server do a tcpdump on the interface where 192.168.140.23 is assigned.
Now what do you see? Do you see packets getting in and out from the fortigate?
Do you see icmp echoes getting to the server? Any icmp reply out?
Thanks,
ADP
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: