- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Re: Route Leaking issue in Global to vrf
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Route Leaking issue in Global to vrf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2020 02:13 AM
Hello Everyone,
We recently are doing a cloud setup and facing an issue with VRF Route-Leaking. Let me explaing you the Scenario.
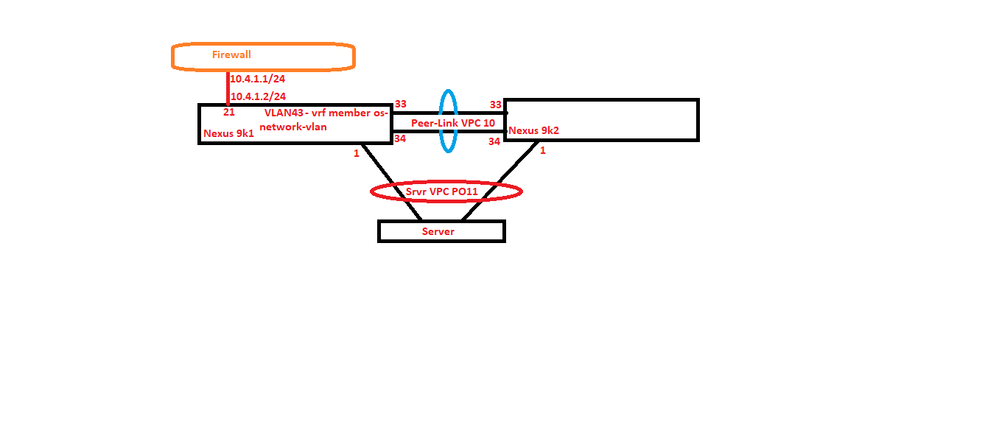
Bellow is the simple network connection diagram. I have attached the detailed one on the discussion.
Problem Statement : From the Vlan42 which is in the Default VRF , i am able to reach the Firewall. But from the Customer VRF( Non-Default VRF ) i am not able to reach my Firewall.
Firewall ( Reverse routes for all subnets are given )
|
|
Nexus 9k1 ------- Nexus9k2 ( Both running in VPC )
\ /
\ /
\ /
\ /
Cisco Server ( Core is in VPC Portchannel with the Nexus 9K - Nic Teamed )
Now i have created multiple vlans on the 9K Peers .
Vlan 42 - 10.4.2.0/24 - Default vrf
Vlan 43 - 10.4.3.0/24 - Os-Nw-Vrf
Below is the configuration of vlans.
vlan 42
name Mgmt-Vlan
interface Vlan42
description "Mgmt-Vlan-Gateway"
no shutdown
ip address 10.4.2.2/24
hsrp 42
priority 110
ip 10.4.2.1
vlan 43
name OS-Network-Vlan
vlan 43
name OS-Network-Vlan
interface Vlan43
description "OS-Network-Vlan-Gateway"
no shutdown
vrf member OS-Network-Vlan
no ip redirects
ip address 10.4.3.2/24
no ipv6 redirects
hsrp 43
priority 110
ip 10.4.3.1
Now BGP Route-Leaking Configuration.
ip prefix-list Default-to-BGP seq 5 permit 0.0.0.0/0 le 32
route-map ALL permit 10
match ip address prefix-list Default-to-BGP
ex
ip prefix-list NETWORK seq 1 permit 0.0.0.0/0 le 32
route-map Default-To-VRF43 permit 10
match ip address prefix-list NETWORK
router bgp 100
address-family ipv4 unicast
network 0.0.0.0/0
network 10.4.1.0/24
network 10.4.2.0/24
redistribute direct route-map ALL
redistribute static route-map ALL
vrf OS-Network-Vlan
address-family ipv4 unicast
network 10.4.3.0/24
redistribute direct route-map ALL
I Have done the route-leaking and the ip routing table lokks something like this
Ip route for Default VRF:
0.0.0.0/0, ubest/mbest: 1/0
*via 10.4.1.1, [1/0], 1d18h, static
10.4.1.0/24, ubest/mbest: 1/0, attached
*via 10.4.1.2, Eth1/21, [0/0], 1d18h, direct
10.4.1.2/32, ubest/mbest: 1/0, attached
*via 10.4.1.2, Eth1/31, [0/0], 1d18h, local
10.4.2.0/24, ubest/mbest: 1/0, attached
*via 10.4.2.2, Vlan42, [0/0], 3d02h, direct
10.4.2.1/32, ubest/mbest: 1/0, attached
*via 10.4.2.1, Vlan42, [0/0], 3d02h, hsrp
10.4.2.2/32, ubest/mbest: 1/0, attached
*via 10.4.2.2, Vlan42, [0/0], 3d02h, local
10.4.3.0/24, ubest/mbest: 1/0, attached
*via 10.4.3.2%OS-Network-Vlan, Vlan43, [20/0], 00:56:01, bgp-100, external
, tag 100
VRF OS-Network-Vlan IP Route Table
ITI-N9K-1(config)# sh ip route vrf os-Network-Vlan
IP Route Table for VRF "OS-Network-Vlan"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%<string>' in via output denotes VRF <string>
0.0.0.0/0, ubest/mbest: 1/0
*via 10.4.1.1%default, [20/0], 00:58:22, bgp-100, external, tag 100
10.4.1.0/24, ubest/mbest: 1/0, attached
*via 10.4.1.2%default, Eth1/21, [20/0], 00:58:22, bgp-100, external, tag 10
0
10.4.2.0/24, ubest/mbest: 1/0, attached
*via 10.4.2.2%default, Vlan642, [20/0], 00:58:22, bgp-100, external, tag 10
0
10.4.3.0/24, ubest/mbest: 1/0, attached
*via 10.4.3.2, Vlan43, [0/0], 3d02h, direct
10.4.3.1/32, ubest/mbest: 1/0, attached
*via 10.4.3.1, Vlan43, [0/0], 3d02h, hsrp
10.4.3.2/32, ubest/mbest: 1/0, attached
*via 10.4.3.2, Vlan43, [0/0], 3d02h, local
==========================================================================================
I AM NOT ABLE TO REACH THE FIREWALL FROM MY "OS-NETWORK-VLAN" vrf . I am able to reach my Siwtchport connecting to Firewall, but i am not able reach the firewall. Please help.
ITI-N9K-1(config)# ping 10.4.1.2 vrf os-Network-Vlan ---- PINGING MY SWITCHPORT-CONNECTIGN_TO FIREWALL
PING 10.4.1.2 (10.4.1.2): 56 data bytes
64 bytes from 10.4.1.2: icmp_seq=0 ttl=255 time=0.51 ms
64 bytes from 10.4.1.2: icmp_seq=1 ttl=255 time=0.349 ms
64 bytes from 10.4.1.2: icmp_seq=2 ttl=255 time=0.397 ms
64 bytes from 10.4.1.2: icmp_seq=3 ttl=255 time=0.346 ms
64 bytes from 10.4.1.2: icmp_seq=4 ttl=255 time=0.311 ms
--- 10.4.1.2 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 0.311/0.382/0.51 ms
ITI-N9K-1(config)# ping 10.4.1.1 vrf os-Network-Vlan --- PINGING TO FIREWALL FROM VRF os-Network-Vlan
PING 10.4.1.1 (10.4.1.1): 56 data bytes
Request 0 timed out
Request 1 timed out
Request 2 timed out
Request 3 timed out
Request 4 timed out
--- 10.4.1.1 ping statistics ---
5 packets transmitted, 0 packets received, 100.00% packet loss
Hello Everyone,
We recently are doing a cloud setup and facing an issue with VRF Route-Leaking. Let me explaing you the Scenario.
Bellow is the simple network connection diagram. I have attached the detailed one on the discussion.
Problem Statement : From the Vlan42 which is in the Default VRF , i am able to reach the Firewall. But from the Customer VRF( Non-Default VRF ) i am not able to reach my Firewall.
Firewall ( Reverse routes for all subnets are given )
|
|
Nexus 9k1 ------- Nexus9k2 ( Both running in VPC )
\ /
\ /
\ /
\ /
Cisco Server ( Core is in VPC Portchannel with the Nexus 9K - Nic Teamed )
Now i have created multiple vlans on the 9K Peers .
Vlan 42 - 10.4.2.0/24 - Default vrf
Vlan 43 - 10.4.3.0/24 - Os-Nw-Vrf
Below is the configuration of vlans.
vlan 42
name Mgmt-Vlan
interface Vlan42
description "Mgmt-Vlan-Gateway"
no shutdown
ip address 10.4.2.2/24
hsrp 42
priority 110
ip 10.4.2.1
vlan 43
name OS-Network-Vlan
vlan 43
name OS-Network-Vlan
interface Vlan43
description "OS-Network-Vlan-Gateway"
no shutdown
vrf member OS-Network-Vlan
no ip redirects
ip address 10.4.3.2/24
no ipv6 redirects
hsrp 43
priority 110
ip 10.4.3.1
Now BGP Route-Leaking Configuration.
ip prefix-list Default-to-BGP seq 5 permit 0.0.0.0/0 le 32
route-map ALL permit 10
match ip address prefix-list Default-to-BGP
ex
ip prefix-list NETWORK seq 1 permit 0.0.0.0/0 le 32
route-map Default-To-VRF43 permit 10
match ip address prefix-list NETWORK
router bgp 100
address-family ipv4 unicast
network 0.0.0.0/0
network 10.4.1.0/24
network 10.4.2.0/24
redistribute direct route-map ALL
redistribute static route-map ALL
vrf OS-Network-Vlan
address-family ipv4 unicast
network 10.4.3.0/24
redistribute direct route-map ALL
I Have done the route-leaking and the ip routing table lokks something like this
Ip route for Default VRF:
0.0.0.0/0, ubest/mbest: 1/0
*via 10.4.1.1, [1/0], 1d18h, static
10.4.1.0/24, ubest/mbest: 1/0, attached
*via 10.4.1.2, Eth1/21, [0/0], 1d18h, direct
10.4.1.2/32, ubest/mbest: 1/0, attached
*via 10.4.1.2, Eth1/31, [0/0], 1d18h, local
10.4.2.0/24, ubest/mbest: 1/0, attached
*via 10.4.2.2, Vlan42, [0/0], 3d02h, direct
10.4.2.1/32, ubest/mbest: 1/0, attached
*via 10.4.2.1, Vlan42, [0/0], 3d02h, hsrp
10.4.2.2/32, ubest/mbest: 1/0, attached
*via 10.4.2.2, Vlan42, [0/0], 3d02h, local
10.4.3.0/24, ubest/mbest: 1/0, attached
*via 10.4.3.2%OS-Network-Vlan, Vlan43, [20/0], 00:56:01, bgp-100, external
, tag 100
VRF OS-Network-Vlan IP Route Table
ITI-N9K-1(config)# sh ip route vrf os-Network-Vlan
IP Route Table for VRF "OS-Network-Vlan"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%<string>' in via output denotes VRF <string>
0.0.0.0/0, ubest/mbest: 1/0
*via 10.4.1.1%default, [20/0], 00:58:22, bgp-100, external, tag 100
10.4.1.0/24, ubest/mbest: 1/0, attached
*via 10.4.1.2%default, Eth1/21, [20/0], 00:58:22, bgp-100, external, tag 10
0
10.4.2.0/24, ubest/mbest: 1/0, attached
*via 10.4.2.2%default, Vlan642, [20/0], 00:58:22, bgp-100, external, tag 10
0
10.4.3.0/24, ubest/mbest: 1/0, attached
*via 10.4.3.2, Vlan43, [0/0], 3d02h, direct
10.4.3.1/32, ubest/mbest: 1/0, attached
*via 10.4.3.1, Vlan43, [0/0], 3d02h, hsrp
10.4.3.2/32, ubest/mbest: 1/0, attached
*via 10.4.3.2, Vlan43, [0/0], 3d02h, local
==========================================================================================
I AM NOT ABLE TO REACH THE FIREWALL FROM MY "OS-NETWORK-VLAN" vrf . I am able to reach my Siwtchport connecting to Firewall, but i am not able reach the firewall. Please help.
ITI-N9K-1(config)# ping 10.4.1.2 vrf os-Network-Vlan ---- PINGING MY SWITCHPORT-CONNECTIGN_TO FIREWALL
PING 10.4.1.2 (10.4.1.2): 56 data bytes
64 bytes from 10.4.1.2: icmp_seq=0 ttl=255 time=0.51 ms
64 bytes from 10.4.1.2: icmp_seq=1 ttl=255 time=0.349 ms
64 bytes from 10.4.1.2: icmp_seq=2 ttl=255 time=0.397 ms
64 bytes from 10.4.1.2: icmp_seq=3 ttl=255 time=0.346 ms
64 bytes from 10.4.1.2: icmp_seq=4 ttl=255 time=0.311 ms
--- 10.4.1.2 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 0.311/0.382/0.51 ms
ITI-N9K-1(config)# ping 10.4.1.1 vrf os-Network-Vlan --- PINGING TO FIREWALL FROM VRF os-Network-Vlan
PING 10.4.1.1 (10.4.1.1): 56 data bytes
Request 0 timed out
Request 1 timed out
Request 2 timed out
Request 3 timed out
Request 4 timed out
--- 10.4.1.1 ping statistics ---
5 packets transmitted, 0 packets received, 100.00% packet loss
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2020 02:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2020 03:30 PM - edited 01-19-2020 03:31 PM
Helo
1) First of all the Fw need to have a route back towardsthe Nxos core for the vrf subnet 10.4.3.0/24.
2) Then the nxos core needs to be aware of its own vtf subnet - ip route 10.4.3.0 255.255.255.0 vlan 43
3) The nexus core need to have a valid route towards 10.4.1.0/24 in it global route table
4) Lastly the vrf table needs to know how to reach non vrf subnets including 10.4.1.0/24 - ip route vrf os-network-vlan 10.4.1.0 255.255.255.0 xxx (nexthop towards 10.4.1.0/24) global
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2020 07:11 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2020 09:37 PM
Dear Paul,
I have mentioned outputs of both of the routing tables.
Ip route for Default VRF:
0.0.0.0/0, ubest/mbest: 1/0
*via 10.4.1.1, [1/0], 1d18h, static ( Default Route Pointing towards Firewall 10.64.1.1 )
10.4.1.0/24, ubest/mbest: 1/0, attached
*via 10.4.1.2, Eth1/21, [0/0], 1d18h, direct
10.4.1.2/32, ubest/mbest: 1/0, attached
*via 10.4.1.2, Eth1/31, [0/0], 1d18h, local
10.4.2.0/24, ubest/mbest: 1/0, attached
*via 10.4.2.2, Vlan42, [0/0], 3d02h, direct
10.4.2.1/32, ubest/mbest: 1/0, attached
*via 10.4.2.1, Vlan42, [0/0], 3d02h, hsrp
10.4.2.2/32, ubest/mbest: 1/0, attached
*via 10.4.2.2, Vlan42, [0/0], 3d02h, local
10.4.3.0/24, ubest/mbest: 1/0, attached ( Route Pointing Towards my OS-NW-VRF ( Customer VRF )
*via 10.4.3.2%OS-Network-Vlan, Vlan43, [20/0], 00:56:01, bgp-100, external
, tag 100
IP Routre for VRF OS-NW-Vlan
0.0.0.0/0, ubest/mbest: 1/0 ( Default Route From Customer VRF to Firewall )
*via 10.4.1.1%default, [20/0], 00:58:22, bgp-100, external, tag 100
10.4.1.0/24, ubest/mbest: 1/0, attached
*via 10.4.1.2%default, Eth1/21, [20/0], 00:58:22, bgp-100, external, tag 10
0
10.4.2.0/24, ubest/mbest: 1/0, attached
*via 10.4.2.2%default, Vlan642, [20/0], 00:58:22, bgp-100, external, tag 10
0
10.4.3.0/24, ubest/mbest: 1/0, attached
*via 10.4.3.2, Vlan43, [0/0], 3d02h, direct
10.4.3.1/32, ubest/mbest: 1/0, attached
*via 10.4.3.1, Vlan43, [0/0], 3d02h, hsrp
10.4.3.2/32, ubest/mbest: 1/0, attached
*via 10.4.3.2, Vlan43, [0/0], 3d02h, local
I have a proper reverse route from firewall for10.4.3.0/24 network pointing to my 9K Siwtch. I have checked it.
But Still i am not able to reach the firewall.. Please help.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2020 03:59 PM - edited 01-21-2020 04:01 PM
Hello
Can you confirm you have this applied?
FW
route inside 10.4.3.0 255.255.255.0 10.4.1.2
Nexus
ip route 10.4.3.0 255.255.255.0 xxx (specify the Interface NOT IP)
ip route 0.0.0 0.0.0 10.4.1.1
ip route vrf os-network-vlan 0.0.0.0 0.0.0.0 10.4.1.1 global
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2020 08:20 AM
Dear Sir,
The issue was solved.. we actually have to create sub interfaces for each of the vlans on nexus... We did that and it was working.. but we kind off reverted everything back and made firewall as the lan gateway.. Thanks for the reply sir.. 😊
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide