- Cisco Community
- Technology and Support
- Security
- Email Security
- Re: New Capabilities to Protect Your Users with Cisco Secure Email - AMA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
New Capabilities to Protect Your Users with Cisco Secure Email - AMA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 09:53 PM
Ask Me Anything Forum
This event is a chance to review how customers of all sizes face the same daunting challenge: email is simultaneously the most important business communication tool and the leading attack vector for security breaches. Cisco Secure Email enables users to communicate securely and helps organizations combat Business Email Compromise (BEC), ransomware, advanced malware, phishing, spam, and data loss with a multilayered approach to security.
To participate in this event, please use the 
Ask questions from Monday, February 1 to Friday, February 12, 2021
Featured Experts
 Dennis McCabe Jr is a Technical Consulting Engineer at the Cisco Global Technical Assistance Center (TAC) for Content Security Email. With more than five years of experience and a broad scope of knowledge relating to Cloud Email Security (CES) and the Email Security Appliance (ESA), Dennis holds certifications including Cisco’s Certified Specialist with Email Security and an MCITP concentrating on Microsoft Exchange. He holds a CCNA Security certification.
Dennis McCabe Jr is a Technical Consulting Engineer at the Cisco Global Technical Assistance Center (TAC) for Content Security Email. With more than five years of experience and a broad scope of knowledge relating to Cloud Email Security (CES) and the Email Security Appliance (ESA), Dennis holds certifications including Cisco’s Certified Specialist with Email Security and an MCITP concentrating on Microsoft Exchange. He holds a CCNA Security certification. Erica Parker is an experienced Technical Consulting Engineer with a demonstrated history of working in the computer networking and cybersecurity industry. With a Bachelor's degree focused in Computer Systems Networking and Telecommunications from Rochester Institute of Technology, she is skilled in Email Security, Software Deployment, and Security Penetration testing with a passion in biomedical sciences. She holds two certifications on CCNA R&S and Security.
Erica Parker is an experienced Technical Consulting Engineer with a demonstrated history of working in the computer networking and cybersecurity industry. With a Bachelor's degree focused in Computer Systems Networking and Telecommunications from Rochester Institute of Technology, she is skilled in Email Security, Software Deployment, and Security Penetration testing with a passion in biomedical sciences. She holds two certifications on CCNA R&S and Security.Please be sure to rate the Answers to your Questions
Do you know you can get answers before opening a TAC case by visiting the Cisco Community?
For more information, visit the Email Security category. To find further Cisco Community events: Click here.
- Labels:
-
Email Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 07:20 AM
Hi,
How do I install a license file onto my virtual ESA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 07:29 AM
Thanks for reaching out. You can install a license file to your virtual ESA by running the ‘loadlicense’ command and choosing which way you’d like to load the license. I would recommend the option for pasting into the CLI. To do this, open up the .xml file received into a program like notepad++ and copy the contents of the license file in its entirety. From there, paste the contents into the CLI and follow the prompts to apply the license.
I hope that helps! Please let us know if you have any further questions.
Best,
Erica
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 07:39 AM
Hi Erica,
Sounds correct to me. I will check it out, thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 07:53 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 08:19 AM
Hello,
This really depends on what type of spoofing is being referred to, with the most common being ‘From’ header spoofing. We have a great article that goes over different types of spoofing, along with some of the many different methods for mitigation, and can be found here. Another great way to combat From header spoofing specifically is to utilize a Content and/or Message Filter, similar to this.
If you have any additional questions please let me know.
Thank you!
-Dennis M.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 10:24 AM - edited 02-05-2021 02:07 PM
Hi Dennis & Erica!
Find below the new question posted by @MB6568 :
C100 Cloud Email Security Appliance
Today I'm tyring to set up a printer to use HPEprint services. When sending an email from inside our domain we get a bounce back for HPEprint.com
We are not having any other issues. We just can't send an email HPEprint.com. Here is what the logs from the C100
|
04 Feb 2021 02:33:24 (GMT +05:00) |
SMTP delivery connection (DCID 926569) opened from Cisco IronPort interface 139.138.47.215 to IP address 15.72.48.225 on port 25. |
|
04 Feb 2021 02:33:25 (GMT +05:00) |
Delivery connection (DCID 926569) successfully accepted TLS protocol TLSv1.2 cipher XXXX-RSA-AES256-XXX-SHA384 None. |
|
04 Feb 2021 02:33:25 (GMT +05:00) |
(DCID 926569) Delivery started for message 1417055 to xxxx@hpeprint.com. |
|
04 Feb 2021 02:33:25 (GMT +05:00) |
(DCID 517346) Message 1417055 to xxxx@hpeprint.com bounced by destination server. Reason: 5.3.0 - Other mail system problem ('550', ['5.7.0 bad DKIM signature data']) |
Anyone have any idea how to get around this issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 10:38 AM
Hello,
Thanks for your question. I've actually seen issues with this in the past for this domain and DKIM. Although not 100% sure without seeing the headers, I assume that this could be related to the slight modification of headers during the transit of these emails to the destination, causing a DKIM failure. One safe way to remediate this would be to place canonization (body and headers) of your DKIM profile to relaxed and test sending email again to the hpeprint.com domain. A relaxed profile takes care of the extra white spaces (in headers or body) which might lead to DKIM failing at the destination.
I hope this helps!
Erica
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 10:27 AM - edited 02-05-2021 02:08 PM
Hi Dennis & Erica!
Find a new question from @Abbas Ravat :
ESA Graymail, Sophos update fail
I have CISCO ESA Appliance, and it does not update Graymail, sophos antivirus. Give message "Attention - updates completed with Error". I can telnet the update URL and its standalone appliance.
Please advice what can be the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 10:46 AM
Hello Abbas,
Thanks for submitting a question. It may be that your ESA is having trouble establishing a connection to the updater servers. I would recommend telnetting the following for a hardware appliance:
- update-manifests.ironport.com 443
- updates.ironport.com 80
- downloads.ironport.com 80
or the following for a virtual appliance:
- update-manifests.sco.cisco.com 443
- updates.ironport.com 80
- downloads.ironport.com 80
and pulling the IP address of each of those servers. Then i'd run an 'updatenow force' on the CLI of the appliance, and tail the updater_logs. This will give you more information about the appliance's ability to reach the servers. If you notice that the appliance begins downloads but can't complete them, finish off with a packet capture while the updatenow force command is running, and filter on one of the IP addresses of the updater servers mentioned above. That should tell you a little bit more about what might be going on and just where in the network the problem lies.
Best,
Erica
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 01:21 PM
Thank you experts!
Here is another question from @shane.wilkerson1 :
sshconfig on M690 Ironport
Trying to update ssh settings on a M690 ESA running AsyncOS 13.0.0-249.
When I logon to the device and run sshconfig I am not presented with sshd as an option to configure ssh settings. The only option I have is to edit user keys. Looking in the config there is only one line there disabling ssh v1.
Ive looked thru the documentation but cant find anything referring to this. Need some assistance getting this resolved.
Thanks for your support!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2021 08:10 AM
Hello,
The sshd option was added under sshconfig for the SMA starting in AsyncOS 13.5.x. You can view the release notes for this addition here. You could make these changes prior to 13.5.x; however, they needed to be completed by manually editing the XML config (in this case - the <sshd_config> section). Though, I would not recommend manually editing the XML configuration without TAC assistance.
Thanks!
-Dennis M.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 01:25 PM
One more!
This question is from @SimonDinney02826 :
Multiple CLI connections to CES
We are running 10 ESAs and 1 SMA in our CES environment. I am able to open up a CLI connection to each server independently using putty. Unfortunately due to the method in which you have to open up a 'proxy' connection first, then the connection to the server, I am unable to have multiple sessions open at the same time. Has anyone come across a method to do this?
Thanks,
Simon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2021 08:23 AM - edited 02-06-2021 08:28 AM
Hello,
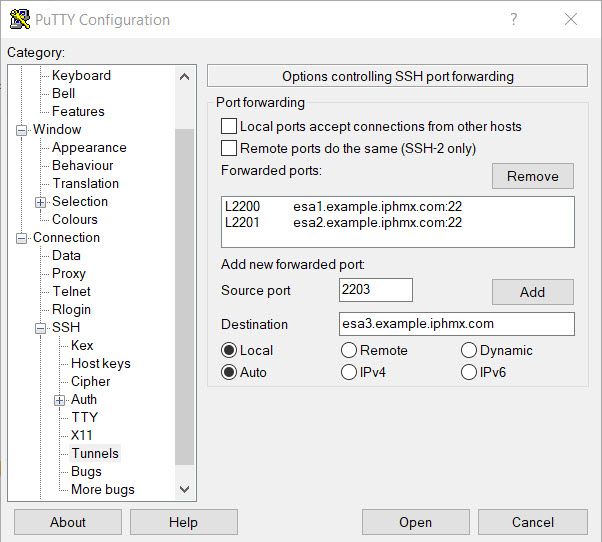
Multiple connections can be accomplished by configuring multiple proxy tunnels on separate source ports.
As an example, you would typically open up the first proxy tunnel connection using a specific source port (e.g. 2200) and destination (e.g. esa1.example.iphmx.com) and then connect to the ESA/SMA using the loopback and the configured source port. To connect to multiple devices simultaneously, you would need to configure additional tunnel forwards using different source ports.
Using the example configuration in the screenshot above, you would then be able to connect to esa1 using 127.0.0.1:2200 and to esa2 using 127.0.0.1:2201. Though, keep in mind that the tunnel forwards connections need to stay active in the background to allow connectivity. Also, be sure not to utilize any ports in use on your system as that may cause conflicts.
Thanks!
-Dennis M.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 01:29 PM
This new question is from @Mohamed Abdullah :
ESA c100 virtual and Exchange server
dears
its first time to me with mail security
i deploy the vm and configure the initial config and add listeners and smtp route and all initial
i need to move and test
is their any thing i do in exchange server or AD domain
and i need to apply HA how can i do that
can any one help me
thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide