- Cisco Community
- Technology and Support
- Security
- Network Security
- Firepower FMC Remote Access VPN & Cisco ISE override group policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 05:25 AM - edited 02-21-2020 09:52 AM
Hi,
We have Firepower FMC 6.4 as RA VPN device and Cisco ISE 2.3 as radius server. We have one connection profile and different group policies on Firepower. We want to use different group policies for different AD groups. on ISE we have configured ASA VPN attribute as the name of the group policy created on Firepower. ISE is working correctly and it says on logs it applies the correct ASA VPN attribute but on firepower it could not override group policy. Every user hits the group policy defined on connection profile.
If we create different connection profile with different aliases it works but we do not work on this way because we do not want clients to see and choose alias.
Thanks,
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 10:04 AM - edited 01-28-2020 10:18 AM
Are you performing posture? If so are you applying the group policy once posture status changes from unknown to compliant? If so, that doesn't appear to work, it only works when first establishing the VPN. So when performing posture, create multiple AuthZ rules (using AD groups to differentiate the users) for the posture unknown state, apply the GP on this first authorisation.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 06:56 AM
Hi,
Did you modify the configuration to permit group policies to be assigned to VPN users from RADIUS? See example below
Which RADIUS values did you configure in the Authorisation Profiles?
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 08:00 AM
Hi,
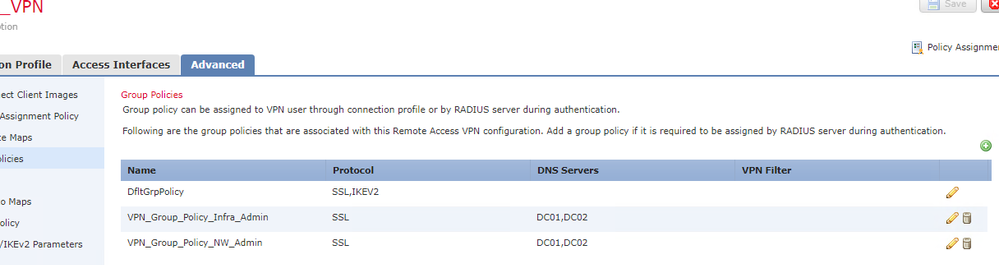
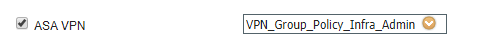
Yes i have already modified, you can see the screenshot below. I am using "ASA VPN" attribute on ISE.
Firepower config :
ISE auth policy config :
@Rob Ingram wrote:Hi,
Did you modify the configuration to permit group policies to be assigned to VPN users from RADIUS? See example below
Which RADIUS values did you configure in the Authorisation Profiles?
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 10:04 AM - edited 01-28-2020 10:18 AM
Are you performing posture? If so are you applying the group policy once posture status changes from unknown to compliant? If so, that doesn't appear to work, it only works when first establishing the VPN. So when performing posture, create multiple AuthZ rules (using AD groups to differentiate the users) for the posture unknown state, apply the GP on this first authorisation.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 10:35 AM
@Rob Ingram wrote:Are you performing posture? If so are you applying the group policy once posture status changes from unknown to compliant? If so, that doesn't appear to work, it only works when first establishing the VPN. So when performing posture, create multiple AuthZ rules (using AD groups to differentiate the users) for the posture unknown state, apply the GP on this first authorisation.
HTH
Yes we are performing posture and yes applying the group policy once posture status changes from unknown to compliant. Ok i will try it now, but i have a question for this; on unknown policy we are redirecting the users to CPP, will i use ASA VPN attribute on the same policy ?
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 10:42 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 12:52 PM
Very very thanks :) it works by that way :)
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: