- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower Rule Design / Ordering
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firepower Rule Design / Ordering
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 05:52 AM - edited 03-12-2019 07:15 AM
Hello,
I would like to know how you guys order and design the FMC Access Control Rules?
Sadly the FMC is not really optimized for a lot of rules, compared to the ASDM or FortiNet etc.. Its really painful in my opinion.
Currently I've went with 2 strategies:
1.
One Access Control Policy, seperated with Categories for each interface/zone:
You can compare this setup with the ASA / ASDM, the source zone of the rule defines the categorie. In this setup multiple source zones arent meant to happen.
I use the default and mandatory category for seperating rules like this:
network -> network = default
network -> host = mandatory
host -> network = mandatory
host -> host = mandatory
this way I cant masquerade host rules, with network rules.
Example:
Mandatory category
-> custom category: Inside-Mandatory or Inside-Hosts
-> sz: inside-zone -> dz: dmz-zone -> sIP: inside host -> dIP: dmz network -> port 443
-> custom category: dmz-Mandatory or dmz-Hosts
-> sz: dmz-zone -> dz: outside-zone and mpls zone -> sIP: dmz host -> dIP: any and mpls locations -> port 443
Default category
-> custom category: Inside or Inside-Network
-> sz: inside-zone -> dz: dmz-zone -> sIP: inside network -> dIP: dmz network -> ICMP
2.
One Access Control Policy per zone with inheritation
With this option there is one base ACP and then i create 1 ACP for each zone and use the inherit feature. I bind the last ACP to the device and then the inherit feature takes care of the rest. Just like the first design I use categories for each source zone, but with this design only the rules i wanna see are being extended and the other rules will be minimized.
This design doesnt scale well with many Interfaces though. But the rule are more transparent and doesnt look like a huge mess.
ACP:
Base ACP
-> Inside Zone ACP
mandatory category -> sz: inside-zone -> dz: dmz-zone -> sIP: inside host -> dIP: dmz network -> port 443
default category-> sz: inside-zone -> dz: dmz-zone -> sIP: inside network -> dIP: dmz network -> ICMP
-> DMZ Zone ACP
mandatory category -> sz: dmz-zone -> dz: outside-zone and mpls zone -> sIP: dmz host -> dIP: public-any and mpls locations -> port 22
default category-> sz: dmz-zone -> dz: outside-zone -> sIP: dmz network -> dIP: public-any -> 443
-> Outside Zone ACP
-> DMZ-Web Zone
Basically these 2 designs all use the old ASDM / ASA scheme, on dCloud Cisco also creates ACP for Services, e.g. SSH or Web. But this is good for couple of rules, but soon as you hit 200 or more rules, nobody will ever really find this useful anymore, since you spend more time searching for rules and where to place them, than really creating rules.
What do you think about these 2 designs?
Kind regards
Lukas
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 06:01 AM - edited 01-24-2019 06:06 AM
to be honest it really depends what you after/what you want to achieve. having said that, looking at your rules example its all upto you how to want to implement and how comfortable are you to deal with this in case some thing is not working and to do a tshoot.
personally, i would go for the 1 strategies, as you will acheive same from the rule 2 but again its going up and down. make the rules simplified so you can deal it easily don't do so complex that you struggle with. this is my input.
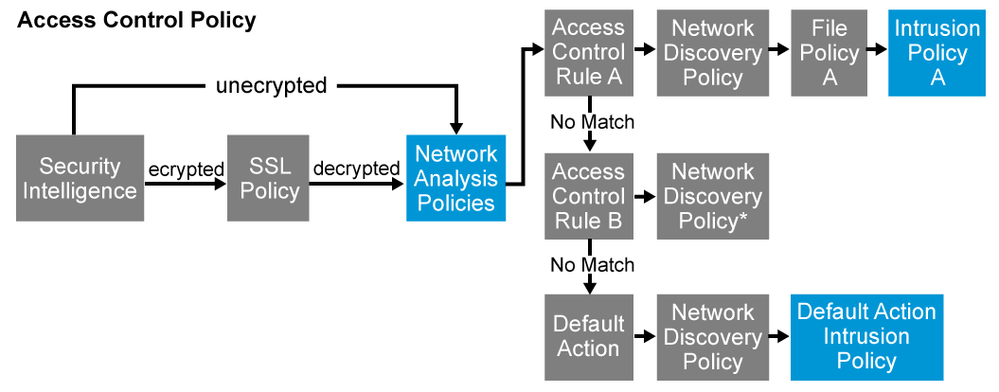
just make sure you have a intrusion policy in place with your interested subset/file policy etc. also i wanted to add the way i do the ACP is i put block rule on top than permit rule under block., also you need to understand the flow of SFR packet flow.
here is a useful diagram for you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 06:44 AM
Thanks for your input!
So you would go with design 1? Or do you have other preferences? I'm always looking for newer and better solutions, also cherry picking some features or designparts ;)
Kind regards
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 06:47 AM
I would go for design 1. however, take the route which ever suit you. as you are a cherry picker and i am old school. I like to do things simple (so in design 1 i shall build my all ACP policy) so i can tshoot in case i need to :).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 06:53 AM
Yeah, i also prefer 1 in most situations, as an example on datacenter firewalls with 100s of interfaces etc.
Old School ASA design is still the most favorable, I've also tried to use the new zone feature and created rules which hold multiple source and destination zones etc. but this ended up in a huge mess. This only looks good on marketing slides, but is not really transparent and easy to understand, especially when having a helpdesk behind which only casually takes a look at the system for creating new rules.
Kind regards
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 06:59 AM
I do agree with you :)
if you think i am helpful kindly please do not forget this to mark as answered so other can benefit too.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: