- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower sensor update from 6.1.0.1 to 6.2.3-88
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firepower sensor update from 6.1.0.1 to 6.2.3-88
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 03:55 AM - edited 02-21-2020 07:54 AM
Hi guys,
I have 4 sensors on 4x ASA 5525-X all managed by FMC 6.2.3.2 (build 42)
I have couple questions:
- all ASA policy-map use fail-open config; SNORT process restart guide says there should be no traffic disruption, still I read on some blogs of some 30" downtime.
+ is there a smart way to update sensors like deleting the class-map SFR from policy-map applied on the ASA during the update?
- I also read on some forums that before sensor update I need to update ASA software; on the documentation guide I see no mention. For the record I am running 9.6(3)1.
- on the FMC System \ Updates I manually uploaded Cisco_Network_Sensor_Upgrade-6.2.3-83.sh ; I see one additional button to the Install and Delete, called Push. What's the use of it?
Thanks in advance,
Florin.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 09:59 PM
Here's a post update with I did/found out so far:
- all ASA policy-map use fail-open config; SNORT process restart guide says there should be no traffic disruption, still I read on some blogs of some 30" downtime.
+ is there a smart way to update sensors like deleting the class-map SFR from policy-map applied on the ASA during the update?
I had disabled the ACL used by SFR class-map and made inactive the last line "permit ip any any"
- I also read on some forums that before sensor update I need to update ASA software; on the documentation guide I see no mention. For the record I am running 9.6(3)1.
Since I found no documentation I consider ASA and sensor software versions not tied by any constraint.
- on the FMC System \ Updates I manually uploaded Cisco_Network_Sensor_Upgrade-6.2.3-83.sh ; I see one additional button to the Install and Delete, called Push. What's the use of it?
In Version 6.2.3+, you can copy (or push) upgrade packages to managed devices before you run the actual upgrade. This helps reduce the length of your upgrade maintenance window. (Before Version 6.2.3, the Firepower Management Center copies the package to managed devices as part of the installation, and you cannot separate the tasks.)
When you push an upgrade package to a device cluster or stack, the Firepower Management Center first pushes to one unit, then to the others. When you push to a high availability pair, the Firepower Management Center pushes to the primary unit, which then synchronizes with the secondary.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2018 07:16 AM
1. fail-open only kicks in the the ASA communications to the module is lost. Other bit of the upgrade process may stop the module from passing traffic before you get to the actual module restart bit.
2. If it's a single ASA (non-HA) then removing the class map, upgrading the sensor and then re-adding the class map would be zero downtime. You'd just not have Firepower coverage in the interim. Note that if your ACPs (vs. ASA ACLs) were used to govern your traffic flow then that will cause issues. If it's an ASA pair in HA, then simply upgrade the standby unit's module, failover and then repeat for the unit that was previously active.
3. Your ASA version 9.6(3)1 is fine as far as Firepower compatibility. (Although you may want to upgrade it to the current interim release address some recent security vulnerabilities.) The relevant compatibility matrix can be found here:
4. Push is a new feature that allows you to stage the new image prior to initiating the upgrade process. It may be useful in high latency / constrained bandwidth situations where the download time may be significant (or if you just want to eliminate that wait during a scheduled maintenance window for the actual upgrade).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 05:34 AM
1. FCM \ System \ Update \ Product updates:
a) What's the role of "Download updates" button? I clicked on it, loads for some time then nothing. Obviously HTTP/HTTPS access from FMC (SSH session was tested/provided)
b) How do you guys do updates on FMC? Everytime you use "Upload update" button?
c) I have here ready to install Sourcefire Vulnerability And Fingerprint Database Updates 299 ? Before doing that how can I lookup/find out current Database updates version number?
2. I am connected on SFR; how can I check sensor uptime from CLI (SSH)? Do you guys maybe have a small SFR CLI cheatsheet with the most useful commands?
Thanks,
Florin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 09:00 AM
1a) "Download updates will check for second ordinal or lesser release (ie. it will not pull 6.3 when you have 6.2.x but it will grab 6.2.y) to your FMC and managed sensors. If any are available it will download them to FMC and make them available for installation.
1b) It depends on what's available. I subscribe to notifications from the product downloads page to stay aware of all new releases and check the release notes to understand and make an informed decision.
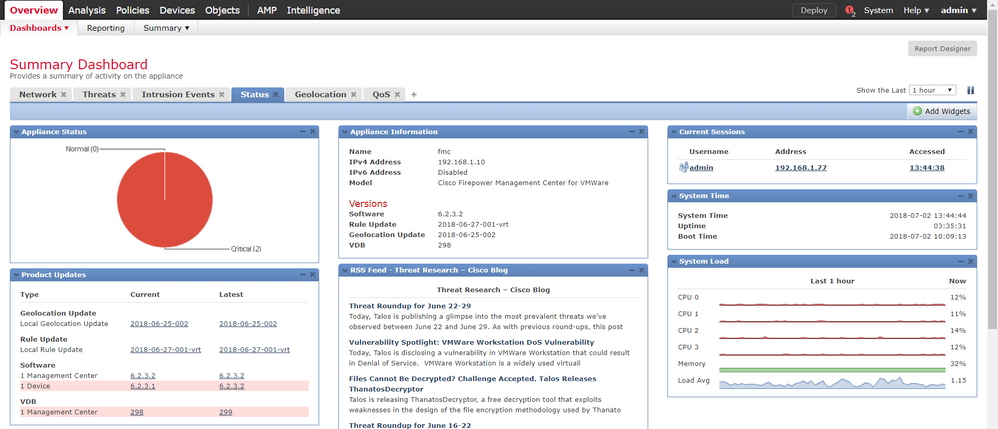
1c) Look under Overview > Dashboards > Summary Dashboard > Status. You can also see uptime there.
2. Most Linux commands are available to you so you can just type "uptime". Note however that is the OS uptime and the Firepower application may have been restarted with rebooting the OS.
admin@fmc:~$ uptime 15:57:42 up 25 days, 2:54, 1 user, load average: 0.79, 0.78, 0.72 admin@fmc:~$
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 10:47 AM
In addition to what @Marvin Rhoads mentioned, two additonal points for 1a and b
1 a) You can use the scheduling tool to set up automatically download of updates. I usually set this up to check every few days so that the download takes places on FMC during off peak hours.
b) If you set up the scheduled download, the Status tab under Summary Dashboard should also gives you the current and latest available release within the same train. It also highlights when you are running behind the latest available version (See below)
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: