- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower Threat Defense-Firepower NGIPS-Firepower Services on ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firepower Threat Defense-Firepower NGIPS-Firepower Services on ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2019 11:02 PM - edited 02-21-2020 09:14 AM
Hi,
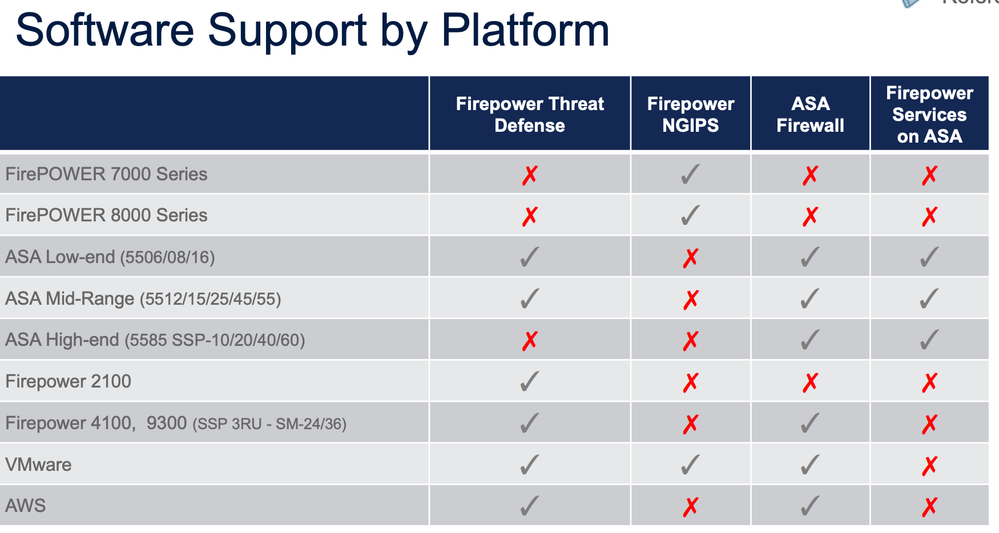
What is the difference between "Firepower Threat Defense-Firepower NGIPS-Firepower Services on ASA" ?
ASA Mid-Range (5512/15/25/45/55) does not support firepower NGIPS ?. Does it mean it does not sNG features ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2019 07:23 AM
The "Firepower NGIPS" on this table refers to the legacy Sourcefire software that can only run on the legacy Sourcefire 7000 and 8000 series appliances and the legacy NGIPSv platform. With that said, you can also run NGIPS mode on the FP9300s, 4100s and 2100s and utilize the fail-to-wire interfaces:
I hope this helps!
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2019 07:29 AM
The differences are in the features and platforms supported. the chart you included shows the platform bit. As far as features:
- FTD is the new software that combines and ASA firewall features in one unified operating system. It doesn't have 100% of either but addresses most use cases.
- NGIPS is the classic Sourcefire software running on Cisco-branded hardware that just an iteration of the Sourcefire 3D series (700 and 800 series and virtual appliances). It has very limited classic firewall type features but is a very good IPS.
- Firepower services on ASA is a software module (not counting ASA 5585-X Firepower hardware module that's now end of sales) running a port of the Firepower software that is the NGIPS. It supports 90% of the NGIPS features with the exception being those aspects that are particular to the Firepower 7000/8000 series hardware.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2019 02:02 AM - edited 06-30-2019 03:54 AM
Hi,
Thanks for the reply.
What is the difference between both datasheet
Cisco Firepower NGFW Data Sheet
https://www.cisco.com/c/en_in/products/collateral/security/firepower-ngfw/datasheet-c78-736661.html
Cisco firepower services datasheet
https://www.cisco.com/c/en_in/products/collateral/security/firepower-ngfw/datasheet-c78-736661.html
https://cdn.cnetcontent.com/34/20/342056b1-b734-4cf7-bbcd-e39599f18df6.pdf
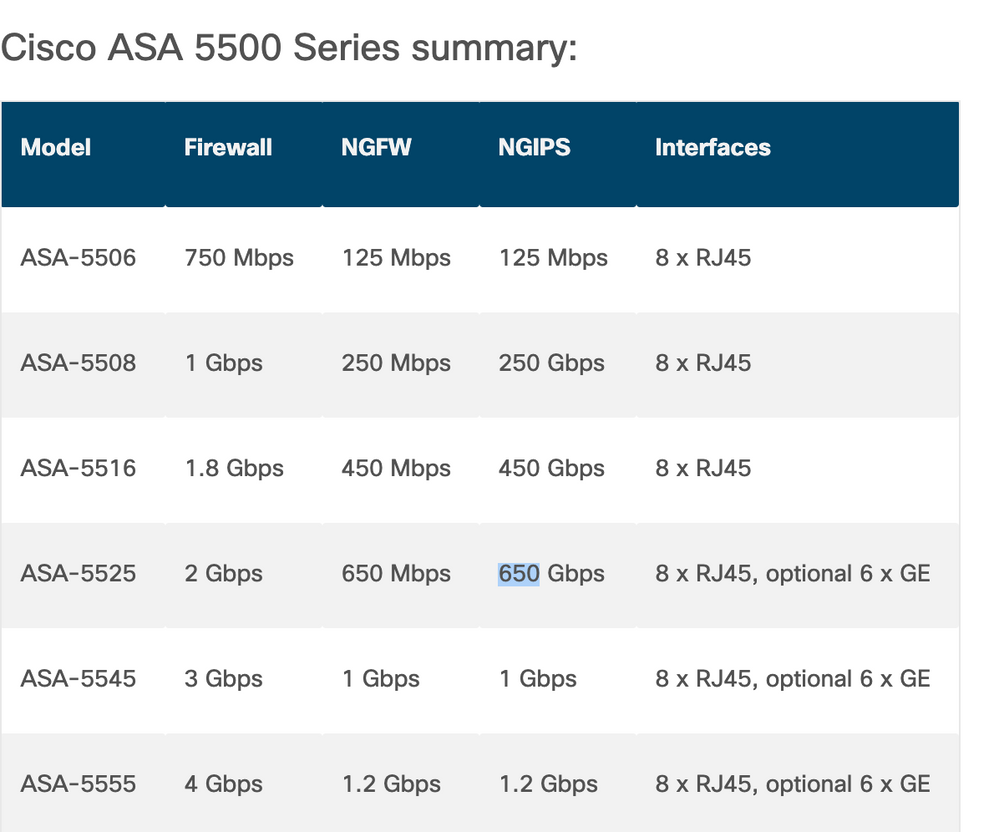
If I need only stateful firewall , where can I find the datasheet for 5525 and 5545
another datasheet shows NGIPS for asa5545 is 1 Gbps and for asa 5525 is 650Gbps
What does it mean
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2019 07:33 AM
For stateful firewall only see the table in the same document you pasted from:
"Table 2. ASA Performance and capabilities on ASA 5500 appliances"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2019 01:11 PM
What Marvin said. The same link that you provided includes both the throughput numbers for NGFW (FTD) and for stateful firewall (ASA)
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2019 10:34 PM
Hi,
What about the summary table in the same link .
is that an error , ngips for the ASA-5525 is 650 Gbps
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2019 10:46 PM
Yes, that's an obvious typo. It should be 650 Mbps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 01:29 AM - edited 07-01-2019 02:35 AM
Hi,
Thanks for the reply . final question in the thread , IF i am going for asa 5545-x with ftd image , which datasheet I have to consider , which throughput metrics i have to consider ?.
There are multiple datasheet really confusing me .
If In case i don’t want want asa with ftd ( means only stateful) which metrics ( in terms of throughput) i need to consider ?
ASA 5545-X with ftd image contains firepower service as a software module ? .
Can I consider IPS service in ASA 5545-X with FTD as NGIPS?
Can I consider asa 5545-x as NGFW
In the below link features addressed as (Table 1)
Throughput: FW + AVC + IPS (1024B)
And in the same time the link below features addressed as ( Table 1 ) “FW + AVC + NGIPS (Cisco Firepower Threat Defense)”
https://www.cisco.com/c/en_in/products/collateral/security/firepower-ngfw/datasheet-c78-736661.html
Why one place addessed as IPS and another place addressed as NGIPS
Thanks a lot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 04:35 AM - edited 07-01-2019 04:37 AM
You're reading marketing documentation - it's not a mathematical proof. As a result there are inconsistencies and outright errors (as you are observing).
Overall though the data are correct. When they talk about "FW + AVC + IPS" they are talking about an ASA appliance running ASA image with a Firepower service module. Think of the service module as a VM on the hardware. When the ASA hardware boots it assigns some CPU cores to the ASA software and others to the Firepower service module. Each has a different throughput, with the Firepower module throughput being lower since it is doing more CPU-intensive work. Therefore throughput is lower with AVC, lower still with AVC + IPS and even lower with smaller packet sizes on average.
NGIPS can generally be considered as running the unified Firepower Threat Defense (FTD) image although Cisco sometimes (confusingly) uses NGFW term for the same thing. Other times they have used NGFW to differentiate the ASA (without any service module) to differentiate it from competitive products.
If you have further questions about sizing your appliance and choosing software, you would be best off having an interactive discussion with a qualified Cisco (or partner) Security SE (Systems Engineer).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 05:03 AM
When sizing the appliance what all I have to consider
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 06:26 AM
Cisco has a tool:
...that can be used to size firewalls.
It tells us to consider:
1. Bandwidth,
2. traffic profile (typical packet size mix or something else),
3. enabled features (AVC, IPS, URL Filtering, AMP, SSL decryption and/or VPN)
4. desired utilization percentage (to account for anticipated growth) and
5. do you need certain features like specific interface types, dual power supply, HA, fail to wire, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 11:15 PM
Thanks for the reply .
how the packet size impact , if the size is smaller how it impact the throughput
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2019 05:05 AM
As shown in the data sheets we discussed earlier, smaller packet sizes result in less throughput (all other things being equal).
That's because the device needs to open each packet and analyze the payload (not exactly the case but it suffices for the sake of discussion). Think if you had 1000 bytes of data and it was all in one packet. That's one packet to analyze. If it was in 10 x 100 byte packets then it's 10 times the unit of work that doing the basic extraction of the payload consumes. There's also some reassembly to make the data back into an analyzable form. All of those units of work, while individually small, add up to affect throughput.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 12:52 AM
Hi,
"- Firepower services on ASA is a software module (not counting ASA 5585-X Firepower hardware module that's now end of sales) running a port of the Firepower software that is the NGIPS. It supports 90% of the NGIPS features with the exception being those aspects that are particular to the Firepower 7000/8000 series hardware."
Does the asa5500-x series include firepower services as a software module ?
Thanks
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: