- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD ACL Syslog messages
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FTD ACL Syslog messages
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2018 06:39 AM - edited 02-21-2020 07:09 AM
Hi,
Versions FMC V6.2.2, FTD 2120 V8.2.2
I have configured Logging to a syslog server on my ACP Default action. The aim is to Log acl deny messages.
From the cli on the FTD 2120 device I can see hits on the acl.
However my Syslog Server does not receive them. They are visible via FMC event Logs.
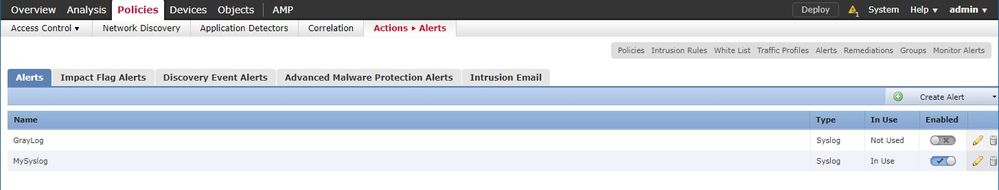
Syslog has been defined in Policies - Actions - Alerts with Facility = Local4 and Severity = Warning.
My Syslog Server has also been configured in my Device Platform settings Policy.
I also enabled Syslog logging on another acl rule which has valid permit hit count. These do not appear in my Syslog server.
The syslog server is reachable via pings form my FTD device.
Any suggestions to resolve this issue would be appreciated.
thanks
Ian
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2018 09:28 AM
Hi,
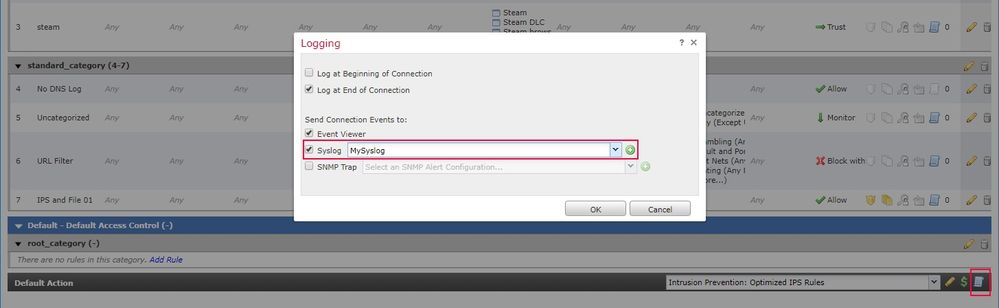
Just to verify, you have configured "Alert" syslog server and activated it under the ACP rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2018 11:02 AM
Thanks for the response.
I have configured "alert" Syslog server and activated it in the ACP rule.
Regards
Ian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2018 11:20 AM
I checked in my home device that is a Firepower Services module and the syslog is sent from the device and not the FMC.
br, Micke
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2018 01:22 AM
Hi Micke,
I agree that syslog messages are sourced from the FTD Interface connected to the syslog server.
The syslog server is reachable from the inside interface and there are no other devices in the path that could block syslog on UDP Port 514.
regards
Ian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2018 01:29 AM
Is the syslog server getting messages from other systems?
br, Micke
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2018 01:35 AM
Hi Micke,
Syslog is receiving messages from other systems including 5585X ASA's with Firepower modules. They are managed by the same FMC at the FTD 2120 deices.
regards
Ian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2018 04:16 AM
I need to dig into some more documentation if nobody else know exact steps to configure this? :)
br, Micke
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2018 11:15 PM
Hey Mate,
Did you get solution for this ?
I have the same issue , I have enabled syslog logging on one of the ACPs ( action as block) as a part of prefilter policy. however cound't see logs coming to syslog server.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2018 07:48 AM
Looks like I managed to activate the logging following this guide:
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/200479-Configure-Logging-on-FTD-via-FMC.html
But I need to do some more testing to see exactly what needs to be configured.
Looks like the FTD is configured with regular "ASA" logging commands, you can see them with the troubleshooting commands in the end of the document.
> system support diagnostic-cli
Attaching to ASA console ... Press 'Ctrl+a then d' to detach.
Type help or '?' for a list of available commands.
><Press Enter>
firepower# sh run logging
logging enable
logging console emergencies
logging buffered debugging
logging host inside 192.0.0.192
logging flash-minimum-free 1024
logging flash-maximum-allocation 3076
logging permit-hostdown
br, Micke
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2018 08:41 AM
Hi,
Unfortunately not resolved so far.
br
Ian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2018 09:13 AM - edited 01-29-2018 09:59 AM
Now when I try to remove the configuration it's still logging.
At the moment I have disabled the logging from device profile and still getting logs to the syslog server.
Guess they are sent now by the configuration settings under alert.
Edit: Ok, so it looks like I get things working by configuring the syslog server under actions/alerts and then adding the server in the rule.
The syslog message is sent from the FTD mgmt IP address.
You can check the IP with following commands:
>expert
~$ ip address
9: management0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP
link/ether 38:90:a5:3a:c2:80 brd ff:ff:ff:ff:ff:ff
inet 10.215.240.219/24 brd 10.215.240.255 scope global management0
br, Micke
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2018 05:46 PM
Thanks, did you configure SYSLOG Facility and Severity as "alert" and have applied this in a prefilter rule or at ACP ?
I need to apply this to the rule which is the part of pre-filter policy.
Can you please share the syslog output ( if this possible) i want to know if log messages contain rule name as well .
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 12:58 AM
Not seeing anything from the prefilter logging just ACP.
The ACP rule log includes this:
Jan 30 08:52:27 FPR2110-LAB-P SFIMS: Protocol: TCP
SrcIP: 172.16.0.101
OriginalClientIP: ::
DstIP: 136.243.5.166
SrcPort: 59143
DstPort: 443
TCPFlags: 0x0
IngressZone: LAN
EgressZone: INTERNET
DE: Primary Detection Engine (61cf9bfe-6c84-11e7-9bbc-b2da5b7afba6)
Policy: FPR2110-DEF-ACP
ConnectType: Start
AccessControlRuleName: internet-access
AccessControlRuleAction: Allow
Prefilter Policy: prefilter-test
UserName: No Authentication Required
Client: SSL client
ApplicationProtocol: HTTPS
InitiatorPackets: 3
ResponderPackets: 1
InitiatorBytes: 691
ResponderBytes: 66
NAPPolicy: Balanced Security and Connectivity
DNSResponseType: No Error
Sinkhole: Unknown
URLCategory: Web Advertisements
URLReputation: Well known
URL: https://dc546.s372.meetrics.net
br, Micke
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 12:30 AM
Thanks mate!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: