- Cisco Community
- Technology and Support
- Security
- Network Security
- FTD: Anyconnect VPN restriction to authenticate on other Connection Profile
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2018 02:31 AM - edited 02-21-2020 08:29 AM
HI,
I have two Anyconnect Profile one for Sales user and one for admin. How to restrict Sales user to login in to Admin user Connection profile.
In ASA i was doing it with Radius attributes and DAP policy, but how to do it in FTD.
Solved! Go to Solution.
- Labels:
-
Firepower Threat Defense (FTD)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2018 07:21 AM
Hi Piyush_Sharma,
You can try setting up radius mapping with attribute 25 on the NPS, the following guide includes exactly what you need to do from the server perspective since there is nothing you need to do on the FTD:
Pass Group-policy Attribute (Attribute 25) from the NPS RADIUS Server
If the group-policy needs to be assigned to the user dynamically with the NPS RADIUS server, the group-policy RADIUS attribute (attribute 25) can be used.
Complete these steps in order to send the RADIUS attribute 25 for dynamic assignment of a group-policy to the user.
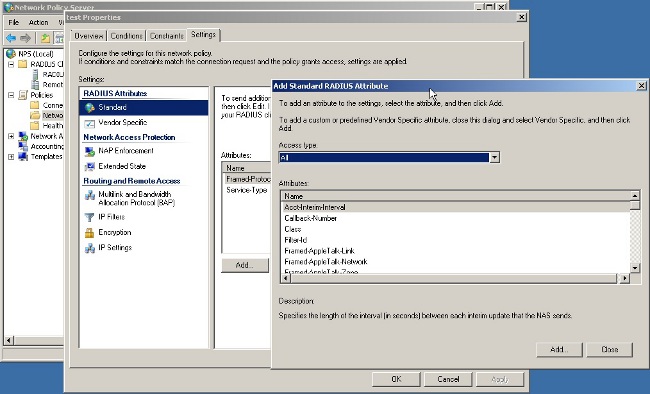
- After the Network Policy is added, right -click the required Network Policy and click the Settings tab.
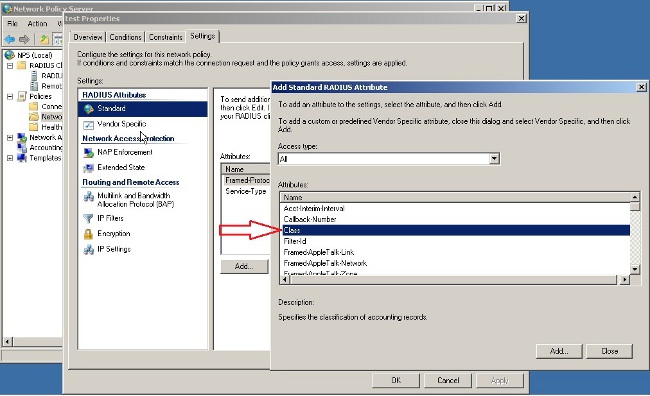
- Choose RADIUS Attributes > Standard. Click Add. Leave the Access type as All.
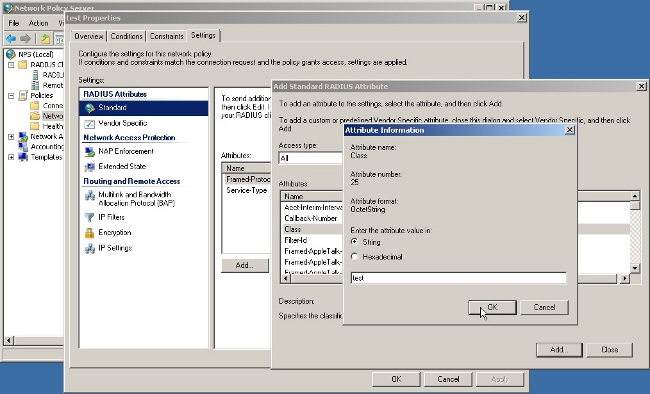
- In the Attributes box, choose Class and click Add. Enter the attribute value, that is, the name of the group-policy as a string. Remember that a group-policy with this name has to be configured in the ASA. This is so that the ASA assigns it to the VPN session after it receives this attribute in the RADIUS response.
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2018 07:21 AM
Hi Piyush_Sharma,
You can try setting up radius mapping with attribute 25 on the NPS, the following guide includes exactly what you need to do from the server perspective since there is nothing you need to do on the FTD:
Pass Group-policy Attribute (Attribute 25) from the NPS RADIUS Server
If the group-policy needs to be assigned to the user dynamically with the NPS RADIUS server, the group-policy RADIUS attribute (attribute 25) can be used.
Complete these steps in order to send the RADIUS attribute 25 for dynamic assignment of a group-policy to the user.
- After the Network Policy is added, right -click the required Network Policy and click the Settings tab.
- Choose RADIUS Attributes > Standard. Click Add. Leave the Access type as All.
- In the Attributes box, choose Class and click Add. Enter the attribute value, that is, the name of the group-policy as a string. Remember that a group-policy with this name has to be configured in the ASA. This is so that the ASA assigns it to the VPN session after it receives this attribute in the RADIUS response.
Hope this info helps!!
Rate if helps you!!
-JP-
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide