- Cisco Community
- Technology and Support
- Security
- Network Security
- Grant different rights to different groups of VPN users
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2019 12:44 PM - edited 02-21-2020 09:34 AM
Hi Team,
We have FMC and FTD in 6.4.0.5
We are setting up remote access VPN from FMC. As FTDs do not support local users, we use Windows NPS.
We want to grant different rights to different groups of VPN users: we have 4 groups.
We have created 4 connections profiles and each of them with a specific Group Policy with the relevant ACL.
The option "Allow Users to select connection profile while logging in" is selected
I have 2 problems:
1) In the login page, the users cannot select each profile: only the first created is available, I do not understand.
2) In the next step, we want to disable the ability to choose a connection profile and just assign it based on AD group membership.
Can you advice me?
Regarding the problem 2, I have found the url "https://community.cisco.com/t5/vpn-and-anyconnect/fmc-anyconnect-and-radius-assign-conection-profile/td-p/3698030" but I do not understand some step
- The step 2 that consists to "assign a group-url for that CP and set it to "https://<FQDN>""
- The step 3 that consists to "find the default group-policy assigned to the CP. Under that group-policy settings, set simulataneous logins to 0."
In advance, thank for your help on this matter
Regards
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2019 05:56 AM
Hi,
Thank all for the reply.
Finally, I have reviewed correctly the documentation (https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/firepower_threat_defense_remote_access_vpns.html#task_ijf_2k2_jfb) and the following link https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/117641-config-asa-00.html
The radius server set (or override) the group-policy name via the radius class attribute
All is working fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2019 03:32 AM - edited 10-11-2019 03:35 AM
(Mentioning @Rahul Govindan to make sure I got this right.)
To make Connection Profile (CP) aliases available for your users to select, you must assign them in the Aliases tab, Alias Names section as shown below:
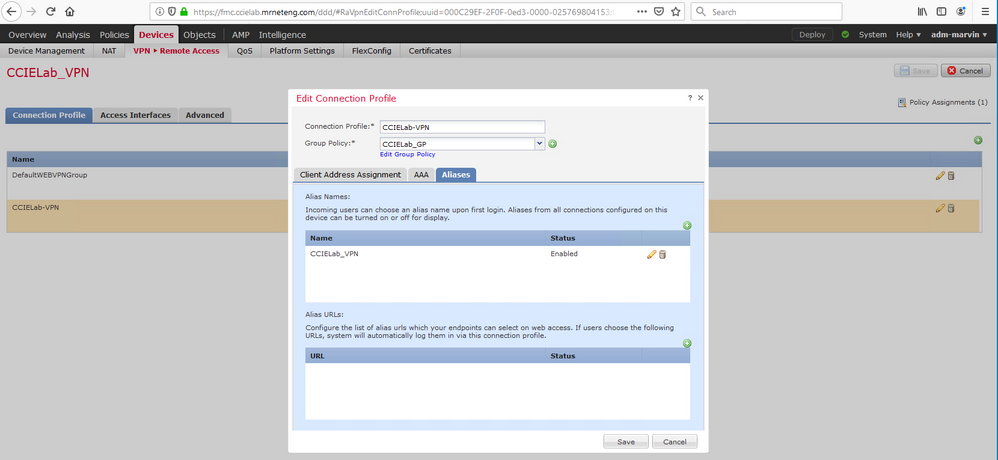
For problem 2, the second step you asked about is also done in the above section of the GUI. In that case add an Alias URL in the bottom section of the tab.
The third step is done by first checking the associated group policy as shown here:
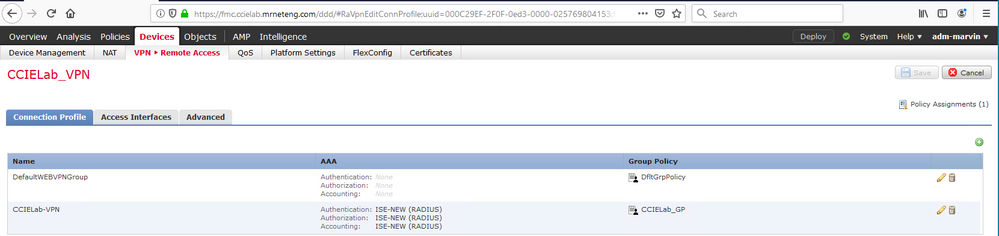
Then edit the group policy's "Simultaneous Login Per User" and make the number = 0. That's under the advanced tab, Session settings as shown here:
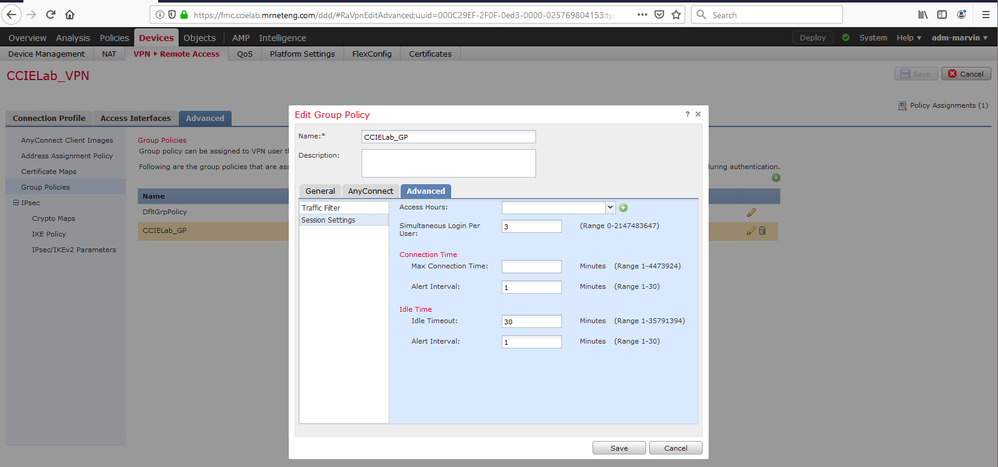
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2019 05:56 AM
Hi,
Thank all for the reply.
Finally, I have reviewed correctly the documentation (https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/firepower_threat_defense_remote_access_vpns.html#task_ijf_2k2_jfb) and the following link https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/117641-config-asa-00.html
The radius server set (or override) the group-policy name via the radius class attribute
All is working fine.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


