- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Help with troubleshooting Firepower FTD VPN not passing traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2019 07:51 AM - edited 02-21-2020 08:37 AM
Hi all
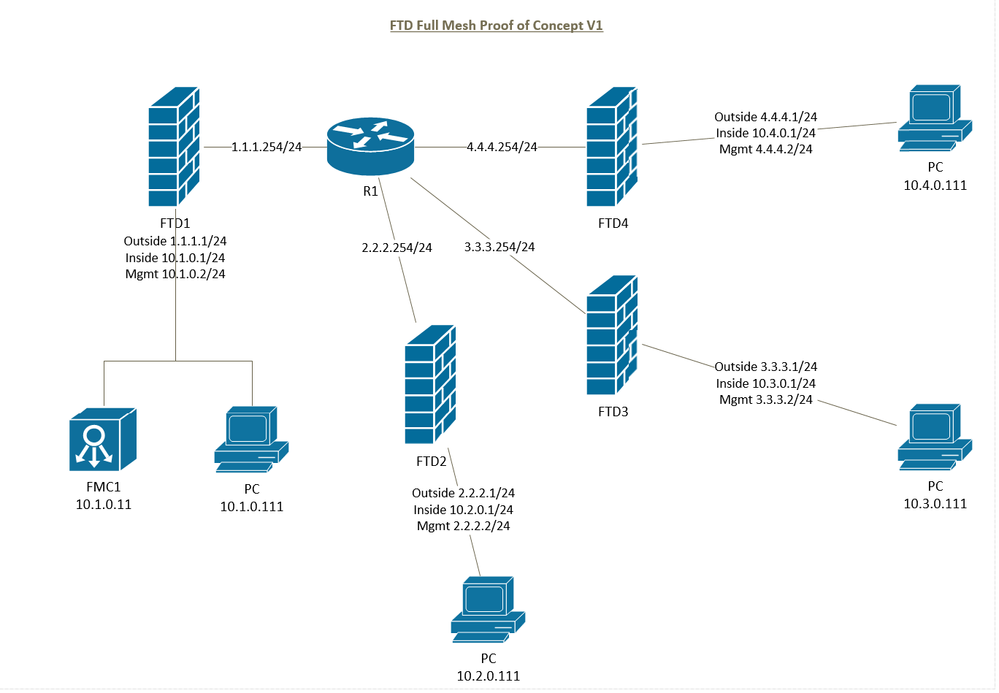
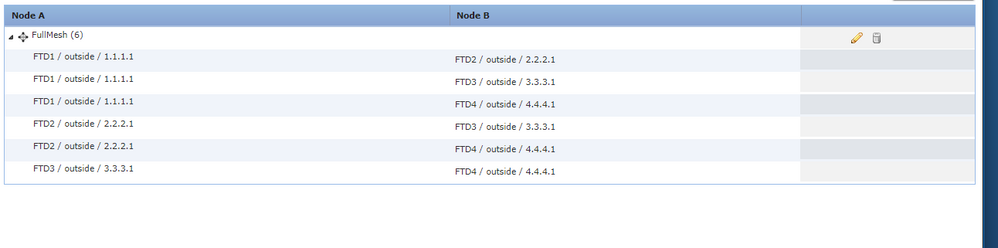
I am currently building a proof of concept with the following topology. It is all built inside a single VMware ESXI host.
I intend to configure a full mesh VPN between all four FTD devices to route between the LAN subnets (10.1.0.0/24,10.2.0.0/24,10.3.0.0/24,10.4.0.0/24)
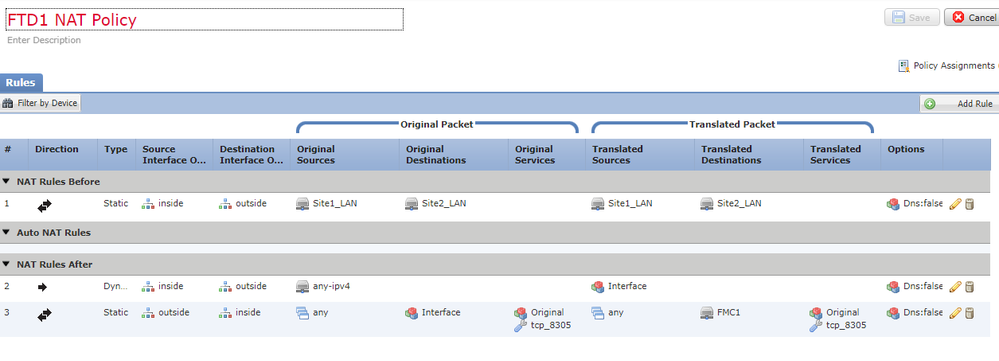
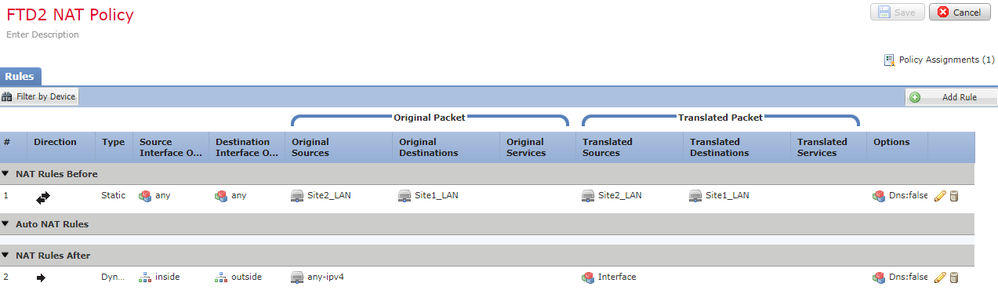
I have a basic "hide" NAT rule setup from inside to outside on each FTD and there is an "any-any" access control policy in place on all the firewalls to rule that out as an issue
PC 10.2.0.111 can ping the outside interface of FTD1 so I know the connectivity through R1 is working. The FMC can also connect to FTD2,FTD3,FTD4 management interfaces over R1 as they have been configured using this connection
The issue is I can't seem to ping the sites from each other, e.g. PC 10.2.0.111 is unable to ping 10.1.0.111. I have checked windows firewall is turned off on the VMs.
Here is the full mesh VPN config page from FMC:
And on FTD2:
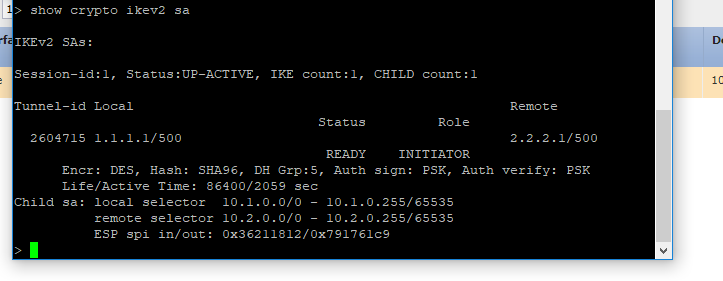
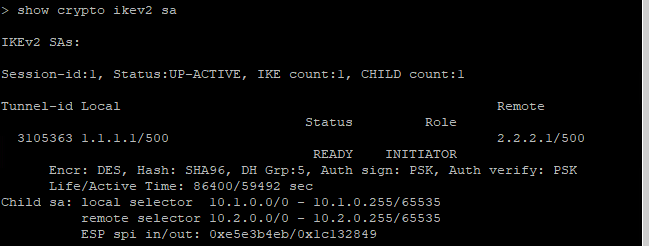
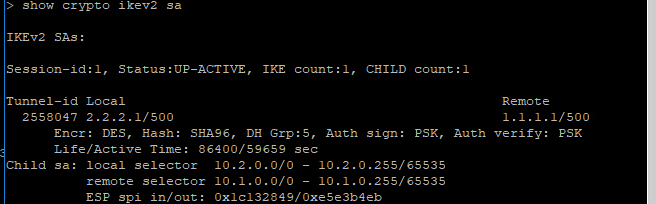
Show crypto ikev2 sa on FTD1 shows the tunnel (all other FTDs show similar)
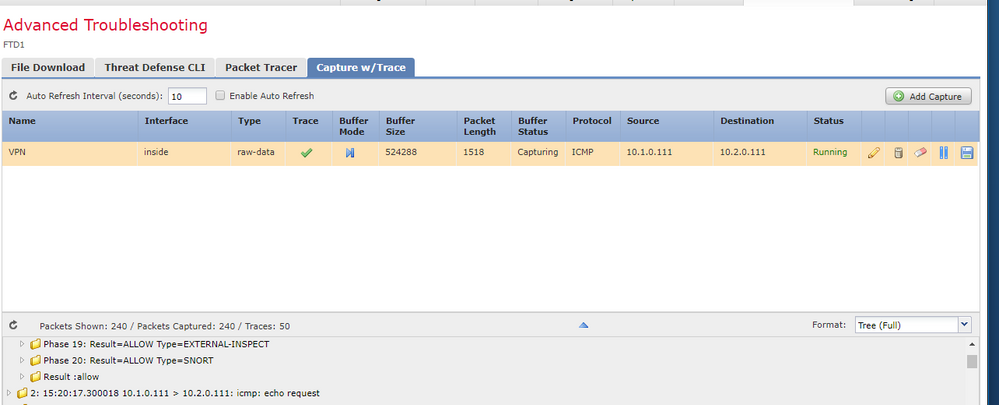
I ran a trace and it says the traffic is allowed:
Does anyopne have more tips on how to troubleshoot this as i'm really stuck
All help appreciated
Solved! Go to Solution.
- Labels:
-
Firepower Threat Defense (FTD)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 03:15 AM
Double check that FTD2 PC has FTD2 inside interface as its gateway. That's the routing that is suspect given your output that you shared.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2019 07:04 AM
Finally fixed it ... subnet mask on PC 10.2.0.111 was set to 255.0.0.0 not 255.255.255.0 ...
Stupid mistake on my part, but a mystery solved!
Thanks for the hints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2019 07:57 AM
Do you have access control policies to permit the traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2019 08:25 AM - edited 01-03-2019 08:26 AM
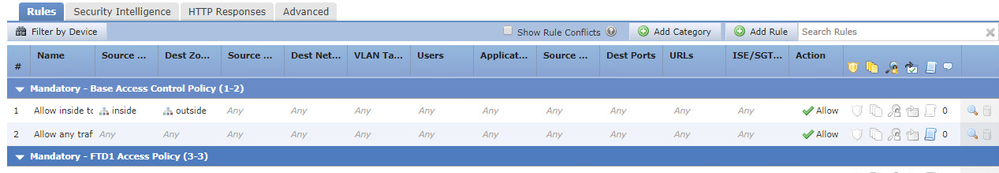
I have the following policy on all FTD devices in place in an attempt to troubleshoot this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2019 08:30 AM - edited 01-03-2019 08:43 AM
run a packet tracer to verify it first.
least it will tell you where the packet the droping
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2019 08:50 AM
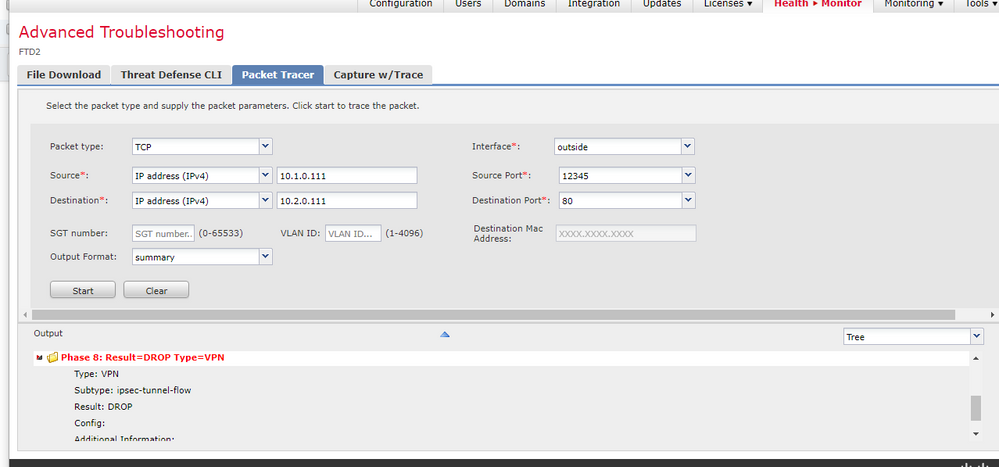
I ran the following packet tracer and it says "DROP" for ipsec-tunnel-flow but im not sure what specifically that means
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2019 09:14 AM
i think you packet trace does not give accurate result in terms of vpn.
can you sent constant ping from Site1_Lan to Site2_Lan in mean time check if phase 1 and phase 2 come up.
if you have access to CLI on FTD give command
show crypto ikev1 sa
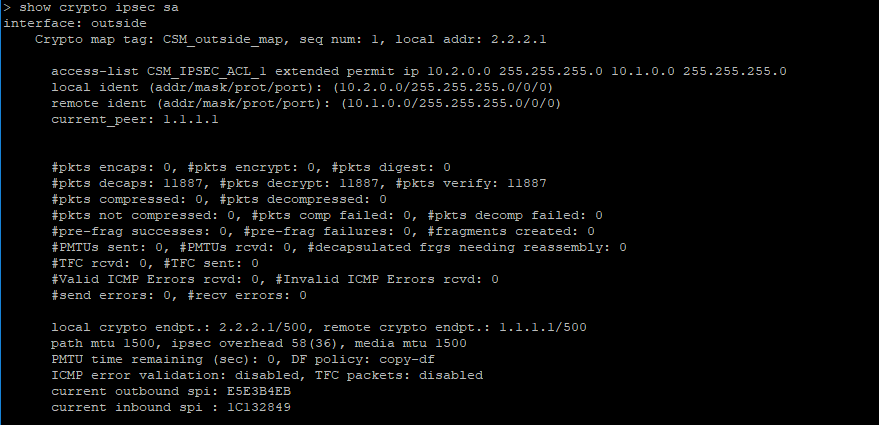
show crypto ipsec sa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:32 AM
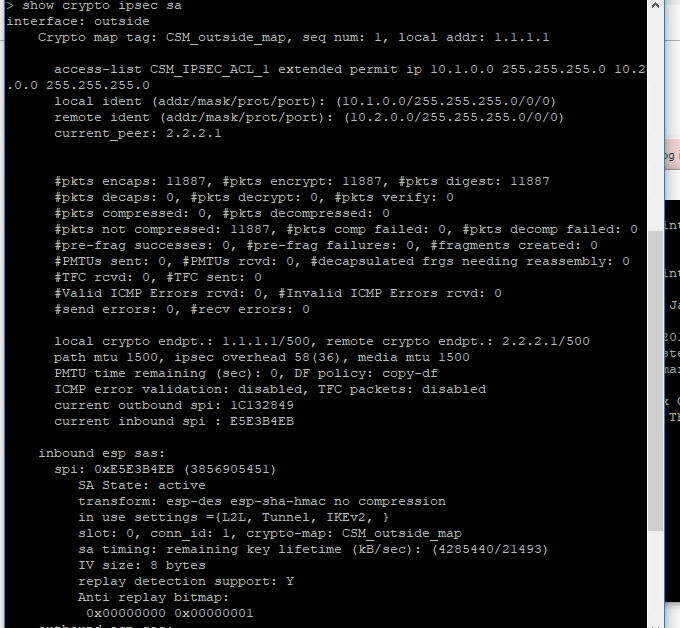
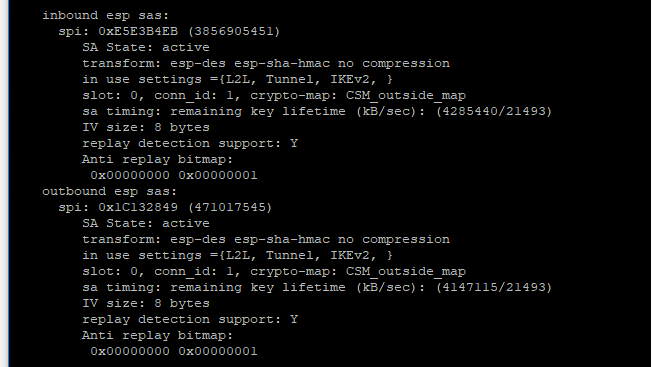
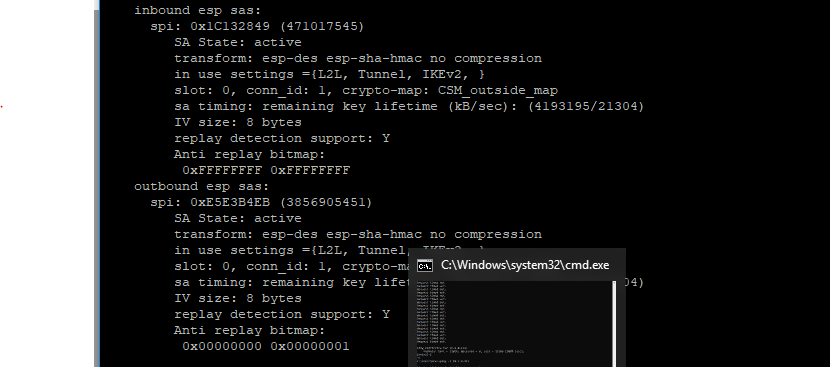
Sure
FTD1:
FTD2:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:35 AM
can you please double check if the routing is properly in place. i can see the encap and no decap. most probably it could be a routing issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:56 AM
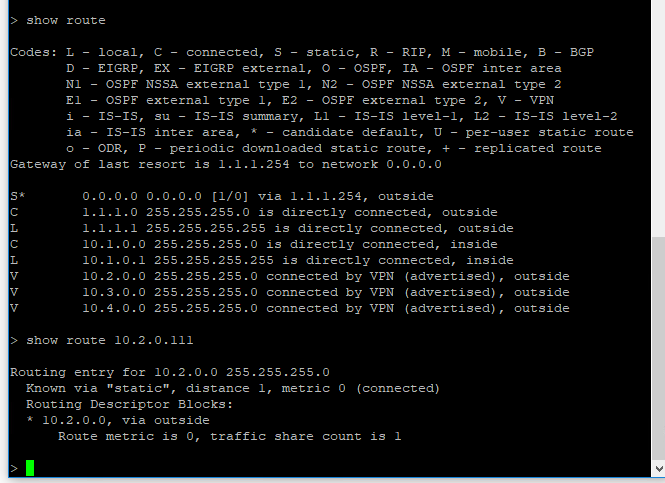
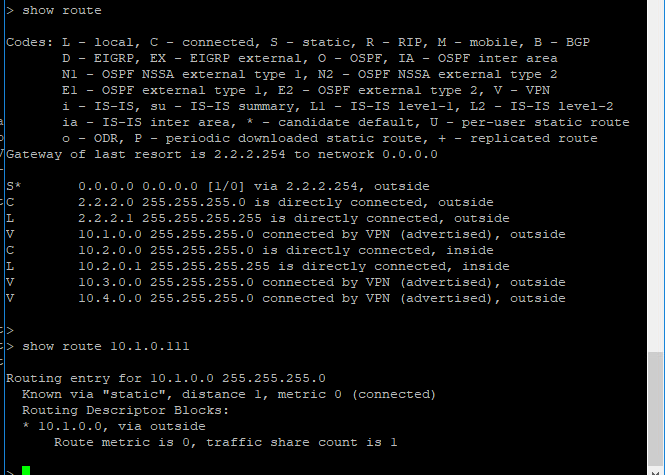
I think that it is:
FTD1:
FTD2:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 03:15 AM
Double check that FTD2 PC has FTD2 inside interface as its gateway. That's the routing that is suspect given your output that you shared.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2019 07:04 AM
Finally fixed it ... subnet mask on PC 10.2.0.111 was set to 255.0.0.0 not 255.255.255.0 ...
Stupid mistake on my part, but a mystery solved!
Thanks for the hints
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide