- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Inspections and Handling of Returning Traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2019 03:22 AM - edited 02-21-2020 09:26 AM
Hi Experts,
After using Firepower for a while, I found myself having this question about how IPS and AMP are handling "returning" traffic (i.e. allowed connections)?
Let's use a simple example. I am allowing "inside" zone to connect to "internet" zone, using a single and simple ACP rule which also has an IPS and File poilcy enabled. And the default ACP action is "Block all". Let's just say that I'm using the system provided IPS policies (Balanced security and connectivity). And I am ok to surf the Internet without any issue. I do see some Intrusion and File events so the protections seem to be working.
The question I suddenly have is.... is IPS and AMP looking at the traffic that is coming "back" from the Internet?
I always have the assumption that, whatever is "allowed" in an ACP rule, the returning traffic will also be subjected to the same IPS and AMP policies, if they are enabled.
Do I have the correct assumption?
Thanks for your help in advance!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
-
NGIPS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2024 05:40 AM
The traffic is evaluated consistent with the ACP rule that allowed the initiating direction in the first place. There is not a "separate" rule for incoming vs. outgoing traffic in a given flow or connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2019 08:58 AM
Anyone could give me a hint about this question? Thanks in advance!
Ben
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2019 07:42 PM - edited 09-08-2019 07:43 PM
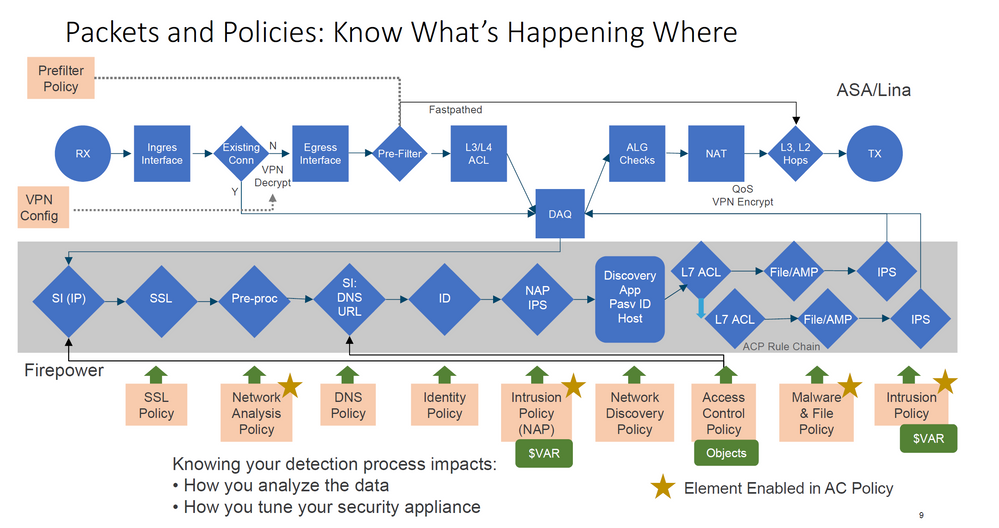
Yes- return traffic is also subject to inspection.
As shown in the graphic below, existence of an existing connection (tcp connection or udp flow) bypasses prefilter and L3/L4 ACL rules but is otherwise subject to the full suite of other NGFW inspections.
Source:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2019 11:06 AM
If you don't mind, could you please elaborate a little bit about what you said "..otherwise subject to the full suite of other NGFW inspections."? I would like to know if I can use a different IPS and AMP (File) policies for existing connections?
Thanks again for your attention and help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2024 05:09 AM
Hello Ben, I have exactly the same question. Did you get any convincing answer? None of the Cisco documents explain how the return traffic is treated. If it is simple ASA, then it is easy to understand the return traffic is automatically allowed through. But in case of FTD, what ACP rule will apply to them?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2024 05:40 AM
The traffic is evaluated consistent with the ACP rule that allowed the initiating direction in the first place. There is not a "separate" rule for incoming vs. outgoing traffic in a given flow or connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2024 06:26 AM
Thank you, Marvin. There is no Cisco document that tells how exactly the return traffic is handled by FTD.
Please also confirm that my below understanding is correct:
Though the LINA engine is from ASA, on FTD platform, there is no concept of security-levels. All interfaces are at the same security-level. For the traffic to be passed from one interface (or zone) to another, explicit ACP rules (or default action) must be in place, but this is only for connection initiation direction. The returning traffic is allowed (stateful firewall) based on the connection table on LINA engine (no explicit ACP rule is needed), but will still be subject to the same ACP rule on SNORT engine, for example, file and intrusion policies. Right?
Thank you so much!!!
Mohan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide