- Cisco Community
- Technology and Support
- Security
- Network Security
- @Dinkar Sharma ,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Traceroute through FTD Sensor?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2017 03:06 AM - edited 02-21-2020 06:01 AM
Does anyone have an FTD based firewall running, where traceroute through it works ?
In ASA, enabling inspection of icmp/icmp error, allowed traceroute to match icmp replies and allow them, without having to open icmp return packets on the outside interface.
This as far as i can tell, is not the case with FTD, I have no policies allowing any traffic from outside->inside, which is what i wan't. The FTD is not blocking the return packets for http/https or any other regular protocol, however it does seem to be blocking the return icmp packets, it seems like the old-style ASA icmp/icmp error inspection, is not working like it used to.
Anyone having problems with traceroute and FTD also ?
/Jan
- Labels:
-
Firepower Threat Defense (FTD)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2017 04:30 AM
There is a bug with 6.1, 6.2 (and even the soon-to-be-released 6.2.1) that may apply to your issue:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvb40875
The Bug description doesn't say so, but you should be able to use FlexConfig on 6.2+ to add the inspect statements back into the configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2017 10:30 AM
I filed this bug after verifying in lab. Yes you can use Flex config to add inspects. The bug has been fixed in 6.2.0.2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 02:10 AM
dinsharm ,
Thanks for the update. the BugID needs to be updated to show 6.2.0.2 as a known fixed release.
Unfortunately the fix did not make it in to 6.2.1. Maybe 6.2.2...?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 06:21 AM
Yes, The fix will be integrated for 6.2.2. We are also trying to get a document out with details. (Specially for FP2100 devices). I will correct the bug fixed versions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 06:32 AM
That's great news Dinkar - thanks.
I look forward to 6.2.2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2017 11:32 AM
By the way - fix is confirmed for 6.2.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2018 02:36 PM - edited 01-15-2018 02:41 PM
... wish I had found this thread earlier. Been bashing my head for quite a few days.
Can anyone confirm this was actually fixed? I'm running 6.2.2.1 on my lab device and the echo reply is still being blocked by the FTD sensor for any hops in the path. It works though for the destination address, but I could then just use a simple ping for that...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2018 07:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2018 06:04 AM
It's not working for me either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2018 11:05 AM
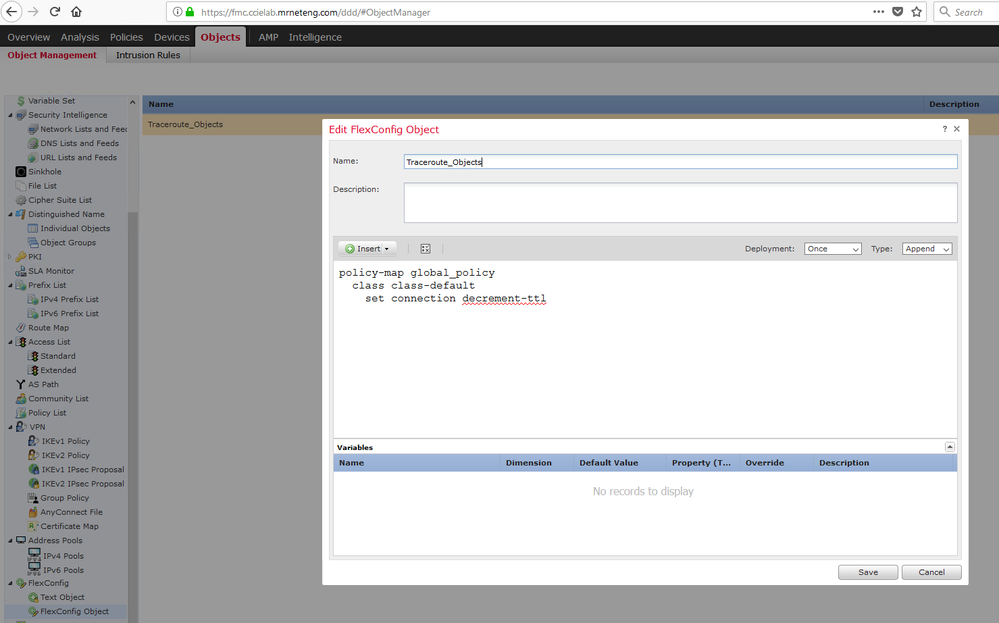
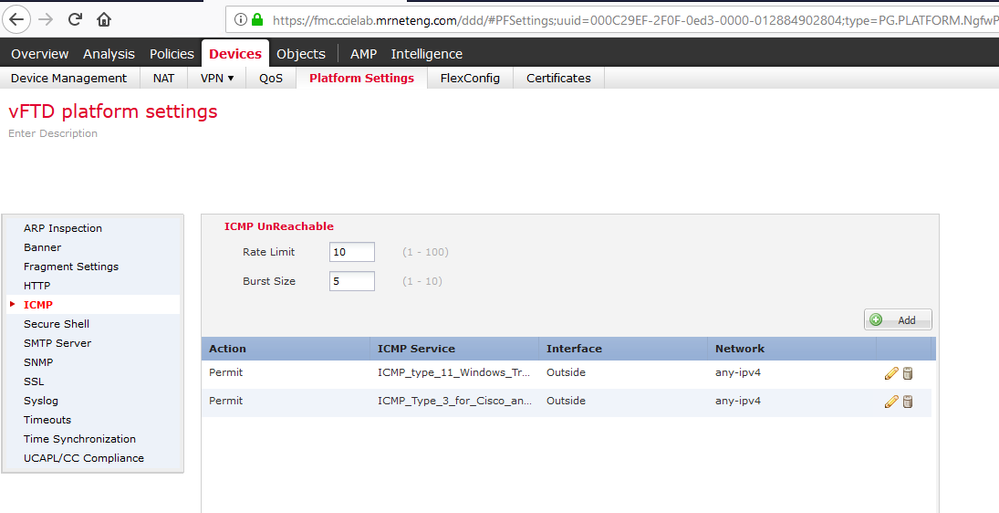
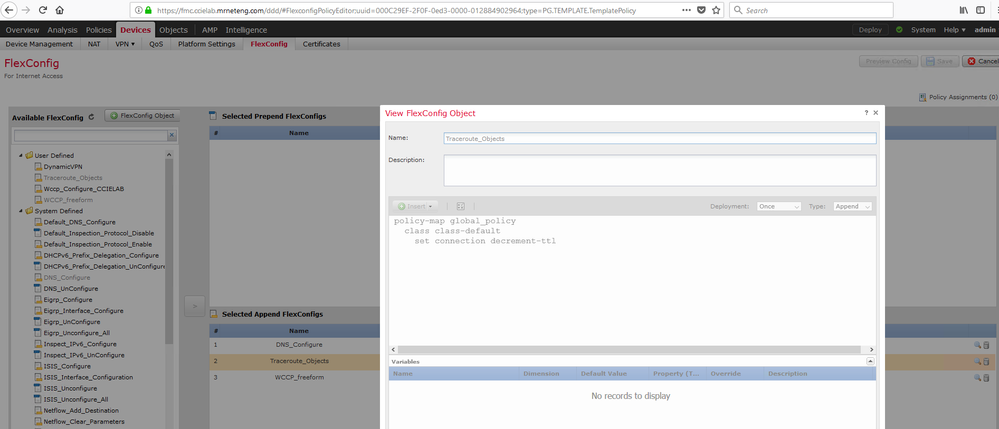
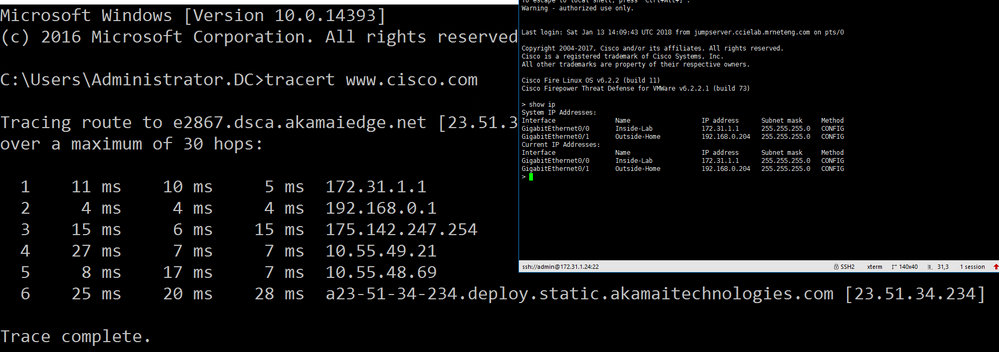
Here's my working configuration that allows both icmp reachability and proper traceroute output (i.e. with first route at FTD firewall reported) from my setup. Basically icmp is being inspected by default but I needed to add the echo replies (both Windows and Unix style) inbound (a platform setting) and also set my policy-map to decrement TTL ( a FlexConfig setup).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2018 07:56 AM
Thank you! ...but ist there a way to apply this on FTD Device Manager directly?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2018 08:06 AM - edited 01-31-2018 10:42 AM
Sorry but no - FDM does not support FlexConfigs.
Those are one of several configuration options not supported via FDM. Others include:
dynamic routing
AAA server
multiple local users
certificates (other than the self-signed one)*
HA
PPPoE
Etherchannel
redundant interface
SNMP configuration
correlation policy
centralized management of multiple devices
*limited certificate support is now available - no CSR capability.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2018 04:59 AM - edited 01-29-2018 05:00 AM
Thank you again :) haha you have removed the site-to-site VPN from the list, thats correct :)
...but I will check that with the certificates double, as I saw an option to upload your own.
Hopefully cisco pushes the development a little bit more for the FTD.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 10:52 AM
Thanks Leon for pointing out the certificate bit. I updated my earlier post to correct it.
I had missed that but found it when I dug into my ASA 5506 running FTD with FDM.
It looks like you can upload but need to generate the key off-box (i.e. no Certificate Signing Request capability). So the super simple GUI requires you also be handy with openssl cli to generate a private key and CSR and then send it off to your CA.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: