- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Fixed yet?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Traceroute through FTD Sensor?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2017 03:06 AM - edited 02-21-2020 06:01 AM
Does anyone have an FTD based firewall running, where traceroute through it works ?
In ASA, enabling inspection of icmp/icmp error, allowed traceroute to match icmp replies and allow them, without having to open icmp return packets on the outside interface.
This as far as i can tell, is not the case with FTD, I have no policies allowing any traffic from outside->inside, which is what i wan't. The FTD is not blocking the return packets for http/https or any other regular protocol, however it does seem to be blocking the return icmp packets, it seems like the old-style ASA icmp/icmp error inspection, is not working like it used to.
Anyone having problems with traceroute and FTD also ?
/Jan
- Labels:
-
Firepower Threat Defense (FTD)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2018 12:53 AM
Hi,
I have FTD's in HA. Do I need to set/change the platform settings for FTD-HA and apply the commands shown in the screenshots? Would appreciate your help!
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 12:48 AM
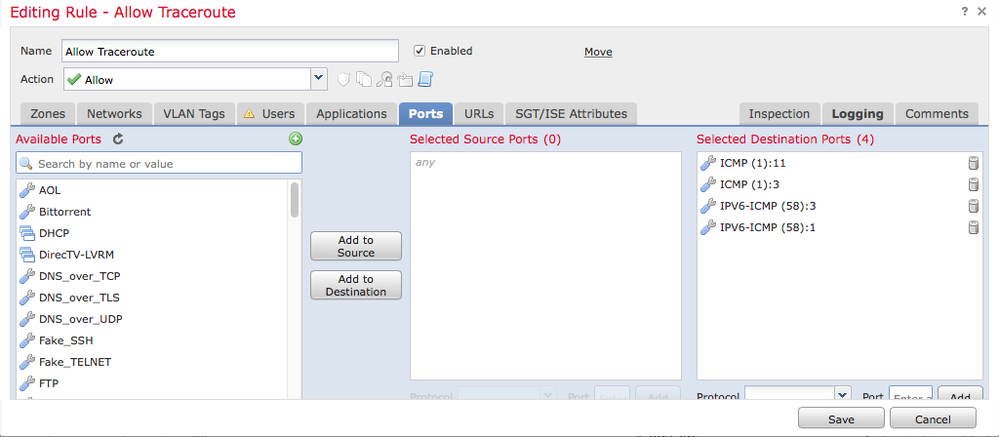
To make the icmp and traceroute work fully yes, you would apply the bits from the FMC screenshots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2018 12:23 PM
Anyone still have this issue? I have an HA pair of Firepower 2110 running 6.2.2.2 in my lab and I flat-out cannot get traceroute to work through them, even after configuring the ICMP and FlexConfig settings recommended by Marvin. I have the same symptom that Alexandre described - all the traceroute hops fail except for the final one, which does come through.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2018 06:37 AM - edited 06-02-2018 06:42 AM
Finally got an answer from TAC on a 2+ month old SR of them, and it works, no fancy settings required:
Add ICMP (either v4 or v6) Destination Unknown and Time Exceeded to the list of allowed ICMP traffic.
And that's it, plain and simple. Not what I was expecting but hey, the theory behind it makes sense if you think about it. If anyone feels brave enough digging into all the small sub-options, feel free to do so and let us know so we can tight even further our controls :)
Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 07:39 AM - edited 01-28-2020 07:44 AM
Fast forward to 2020, "set connection decrement-ttl" is not a supported CLI command anymore on FlexConfig Object, the two ICMP types added as access list rules do not do anything else anymore, and traceroute is broken again: all but the last hop doesn't time out.
Any more hints and tips, aside of moving to a PaloAlto?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 07:45 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 09:15 AM - edited 01-28-2020 09:27 AM
Removed all previous settings I had (which by the way I later found out the CLI syntax for FlexConfig should be "set conn decrease-ttl" as Cisco renamed "connection" to "conn"), gave the instructions from your referred post a try, no luck.
Worth noting the FTD capture with trace is dropping ICMP because of their short TTL, but passing UDP - except this does no good as ICMP is being blocked so the endpoint will never have any clue where on the trace the packet is stopping at.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2017 08:05 PM
OK, thanks for the guidance so far. Can someone expand or post a link on how to "use Flex config to add inspects"?.
I tried adding the System Defined, Default_Inspection_Protocol_Enable, to a new Flexconfig policy, however it seemed to do nothing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2017 10:08 PM
[@itsupport@protectorfire.com.au]
Answered in your related post:
https://supportforums.cisco.com/discussion/13338721/configuring-block-ips-isp-5508-fmc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 05:17 AM - edited 05-15-2020 02:14 AM
In an earlier version of FMC I followed Marvin's advice and created a flexconfig object to apply the following:
policy-map global_policy
class class-default
set connection decrement-ttl
This was added to a 5506 FTD and worked fine. However I have since upgraded to FMC 6.6 and decrement ttl is now configurable from the GUI (although not to the class-default, but needs to be tied to an extended ACL). I therefore tried to remove the flexconfig object. When I unassign the flexconfig policy I get a warning saying that the CLI will not be removed and a 'Negate CLI' policy needs pushing to the device to get rid of it.
Unfortunately it is no longer possible to create a flexconfig object with the same elements as above (with or without a 'no' on the set line). So it appears there is no way to remove this from the configuration.
How do I get rid of this as there is no access to change the configuration from the CLI?
Andy
EDIT: I should have just read this thread more closely... HQuest's reply helped me. You can still apply this as a FlexConfig element, however 'set connection decrement-ttl' needs changing to 'set conn decrement-ttl'. This works with a negate (no set....) as well so I have managed to fix my issue.
Cheers
Andy
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: