- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Allowing OpenVPN through ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 08:57 AM - edited 02-21-2020 08:27 AM
Hi,
I am pretty new to ASA's, and I've been given this task to do. I've set up NAT a few times on ASDM, which seemed quite straightforward: 1) create network objects, 2) config NAT on the internal network object, 3) create an ACL to allow traffic through. I'm still a Cisco noob though.
I have been tasked with allowing access through out 5512X to an OpenVPN server, using UDP port 443. The choice to do this was made above my paygrade.
I have created the 2 network objects - int_OpenVPN and ext_OpenVPN, and an ACL configured as shown below.
When we use the OPenVPN GUI to connect to the internal IP, we connect. When we use the external IP, we get a TLS error - see the log below. Any assistance or pointers much appreciated - I am sure I missed something basic and obvious.
Tue Nov 13 11:52:33 2018 OpenVPN 2.4.6 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 26 2018
Tue Nov 13 11:52:33 2018 Windows version 6.1 (Windows 7) 64bit
Tue Nov 13 11:52:33 2018 library versions: OpenSSL 1.1.0h 27 Mar 2018, LZO 2.10
Tue Nov 13 11:52:33 2018 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Tue Nov 13 11:52:33 2018 Need hold release from management interface, waiting...
Tue Nov 13 11:52:33 2018 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Tue Nov 13 11:52:33 2018 MANAGEMENT: CMD 'state on'
Tue Nov 13 11:52:33 2018 MANAGEMENT: CMD 'log all on'
Tue Nov 13 11:52:33 2018 MANAGEMENT: CMD 'echo all on'
Tue Nov 13 11:52:33 2018 MANAGEMENT: CMD 'bytecount 5'
Tue Nov 13 11:52:33 2018 MANAGEMENT: CMD 'hold off'
Tue Nov 13 11:52:33 2018 MANAGEMENT: CMD 'hold release'
Tue Nov 13 11:52:33 2018 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Tue Nov 13 11:52:33 2018 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Tue Nov 13 11:52:33 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]<MY EXT IP>:443
Tue Nov 13 11:52:33 2018 Socket Buffers: R=[8192->8192] S=[8192->8192]
Tue Nov 13 11:52:33 2018 UDP link local: (not bound)
Tue Nov 13 11:52:33 2018 UDP link remote: [AF_INET]<MY EXT IP>:443
Tue Nov 13 11:52:33 2018 MANAGEMENT: >STATE:1542127953,WAIT,,,,,,
Tue Nov 13 11:53:33 2018 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Tue Nov 13 11:53:33 2018 TLS Error: TLS handshake failed
Tue Nov 13 11:53:33 2018 SIGUSR1[soft,tls-error] received, process restarting
Tue Nov 13 11:53:33 2018 MANAGEMENT: >STATE:1542128013,RECONNECTING,tls-error,,,,,
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 10:32 PM
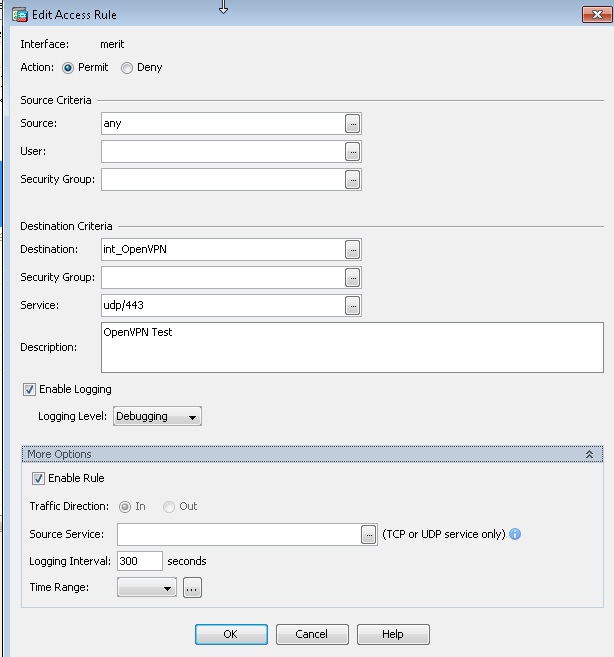
TCP/443 is open on ACL (On ACL screenshot it shows only UDP/443/
As per your NAT command you had configured identity NAT, that is Both Real Host and Mapped Host as same (ext_OpenVPN). It should be the case.
nat (inside,merit) source static any any destination static ext_OpenVPN ext_OpenVPN net-to-net no-proxy-arp route-lookup
If your Int_OpenVPN is behind inside network, you need below NAT Command
nat (inside, merit) static int_OpenVPN ext_OpenVPN
Also before testing VPN, I would recommend to open all port on ACL and do ping test before testing VPN
Please share current asa config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 10:17 AM
What NAT configuration do you have in place? Can you provide the output of the running config?
Can you also run packet-tracer and provide the output.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 10:43 AM
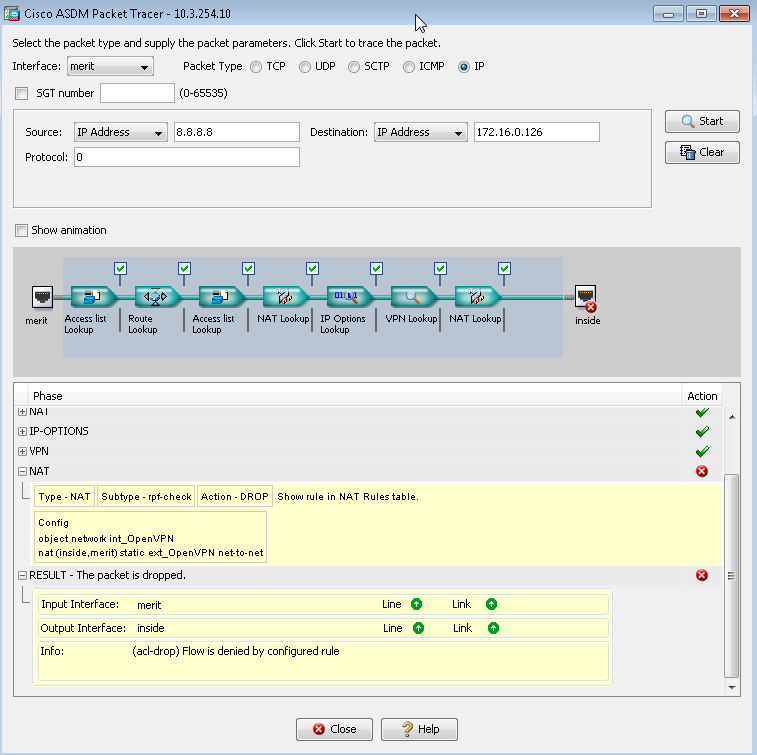
The only way I know how to run packet tracer is on ASDM - here is what I see at the end.
Is this the part of running-config you need to see? (I have changed from udp/443 to ip to test if that was the issue).
nat (inside,merit) source static any any destination static ext_OpenVPN ext_OpenVPN net-to-net no-proxy-arp route-lookup
access-list merit_access_in extended permit ip any object int_OpenVPN log debugging
object network int_OpenVPN
nat (inside,merit) static ext_OpenVPN net-to-net
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 10:32 PM
TCP/443 is open on ACL (On ACL screenshot it shows only UDP/443/
As per your NAT command you had configured identity NAT, that is Both Real Host and Mapped Host as same (ext_OpenVPN). It should be the case.
nat (inside,merit) source static any any destination static ext_OpenVPN ext_OpenVPN net-to-net no-proxy-arp route-lookup
If your Int_OpenVPN is behind inside network, you need below NAT Command
nat (inside, merit) static int_OpenVPN ext_OpenVPN
Also before testing VPN, I would recommend to open all port on ACL and do ping test before testing VPN
Please share current asa config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2018 08:33 AM
Thanks for your help - my manager became impatient and asked someone else to solve the problem.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide