- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5505, error in Access Rule
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5505, error in Access Rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2015 06:25 AM - edited 03-11-2019 10:29 PM
Hello.
Tha ASA 5505 is working, but I try to allow http and https from internet to a server running 2012 Essentials. The server has the internal IP 192.168.0.100. I have created an Object called SERVER with IP 192.168.0.100
The outside Interface is called ICE
I have configured NAT:
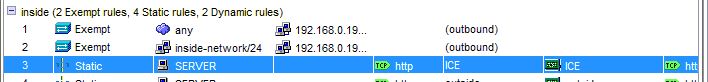
I have also configured Access Rules:
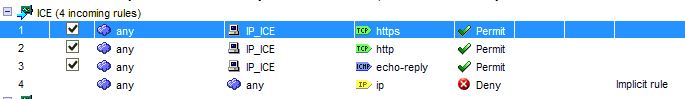
But when I test it With the Packet Tracer I get an error:
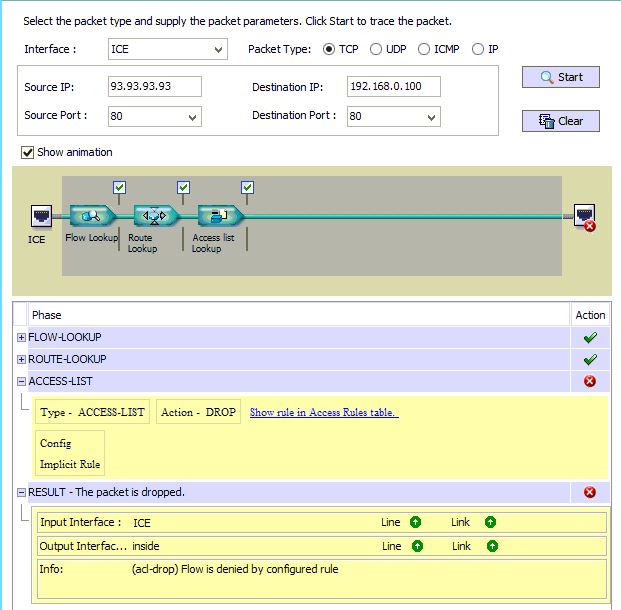
Whats wrong With the Access Rule?
I do prefer the ASDM :)
Best regards Andreas
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2015 12:32 PM
share your run-config.
Jeevak,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2015 05:57 AM
Hello Jeevak.
This is the running config (Vlan 13 (Interface ICE) is the one in use:
domain-name DOMAIN.local
names
name 192.168.0.150 Server1 description SBS 2003 Server
name 192.168.10.10 IP_ICE
name x.x.x.0 outside-network
name x.x.x.7 IP_outside
name 192.168.0.100 SERVER description Hovedserver
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface Vlan2
description Direct Connect
backup interface Vlan13
nameif outside
security-level 0
pppoe client vpdn group PPPoE_DirectConnect
ip address pppoe
!
interface Vlan3
description Gjestenettet
nameif dmz
security-level 50
ip address 10.0.0.1 255.255.255.0
!
description Backupnett ICE
nameif ICE
security-level 0
ip address IP_ICE 255.255.255.0
!
interface Vlan23
description
nameif USER
security-level 50
ip address 10.1.1.1 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
switchport access vlan 13
!
interface Ethernet0/2
switchport access vlan 23
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
switchport access vlan 3
!
interface Ethernet0/7
switchport access vlan 3
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns domain-lookup dmz
dns server-group DefaultDNS
domain-name DOMAIN.local
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_access_in extended permit tcp any host IP_outside eq https
access-list outside_access_in extended permit tcp any host IP_outside eq www
access-list outside_access_in extended permit icmp any host IP_outside echo-reply
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list outside_access_in remark For RWW
access-list DOMAINVPN_splitTunnelAcl standard permit any
access-list inside_nat0_outbound extended permit ip any 192.168.0.192 255.255.255.192
access-list inside_nat0_outbound extended permit ip 192.168.0.0 255.255.255.0 192.168.0.192 255.255.255.192
access-list DOMAIN_VPN_splitTunnelAcl standard permit 192.168.0.0 255.255.255.0
access-list ICE_access_in extended permit tcp any host IP_ICE eq https
access-list ICE_access_in extended permit tcp any host IP_ICE eq www
access-list ICE_access_in extended permit icmp any host IP_ICE echo-reply
access-list ICE_access_in remark For RWW
access-list ICE_access_in remark For RWW
access-list USER_access_in extended permit ip any any
pager lines 24
logging enable
logging asdm warnings
mtu inside 1500
mtu outside 1500
mtu dmz 1500
mtu ICE 1500
mtu USER 1500
ip local pool VPNPool 192.168.10.210-192.168.10.225 mask 255.255.255.0
no failover
monitor-interface inside
monitor-interface outside
monitor-interface dmz
monitor-interface ICE
monitor-interface USER
icmp unreachable rate-limit 1 burst-size 1
icmp permit outside-network 255.255.255.0 outside
icmp permit 192.168.10.0 255.255.255.0 ICE
asdm image disk0:/asdm-524.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
global (ICE) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
nat (dmz) 1 10.0.0.0 255.255.255.0
nat (USER) 1 10.1.1.0 255.255.255.0
static (inside,ICE) tcp interface www SERVER www netmask 255.255.255.255
static (inside,outside) tcp interface www SERVER www netmask 255.255.255.255
static (inside,ICE) tcp interface https SERVER https netmask 255.255.255.255
static (inside,outside) tcp interface https SERVER https netmask 255.255.255.255
access-group outside_access_in in interface outside
access-group ICE_access_in in interface ICE
access-group USER_access_in in interface USER
route outside 0.0.0.0 0.0.0.0 x.x.x.1 1 track 123
route ICE 0.0.0.0 0.0.0.0 192.168.10.1 254
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
http server enable
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
sla monitor 1
type echo protocol ipIcmpEcho x.x.x.1 interface outside
num-packets 3
frequency 10
sla monitor schedule 1 life forever start-time now
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto dynamic-map outside_dyn_map 20 set pfs group1
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto dynamic-map outside_dyn_map 40 set pfs group1
crypto dynamic-map outside_dyn_map 40 set transform-set ESP-3DES-SHA
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
track 123 rtr 1 reachability
no vpn-addr-assign local
telnet timeout 5
ssh timeout 5
console timeout 0
management-access inside
dhcpd auto_config outside
!
dhcpd address 10.0.0.10-10.0.0.39 dmz
dhcpd dns y.y.y.2 z.z.z.z interface dmz
dhcpd lease 6000 interface dmz
dhcpd enable dmz
!
dhcpd address 10.1.1.100-10.1.1.120 USER
dhcpd dns y.y.y.2 z.z.z.z interface USER
dhcpd lease 6000 interface USER
dhcpd domain USER interface USER
dhcpd enable USER
!
ntp server 64.0.0.2 source outside
group-policy DOMAIN_VPN internal
group-policy DOMAIN_VPN attributes
dns-server value 192.168.0.150
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value DOMAIN_VPN_splitTunnelAcl
default-domain value DOMAIN.local
!
class-map inspection_default
match default-inspection-traffic
class-map imblock
match any
class-map P2P
match port tcp eq www
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map type inspect im impolicy
parameters
match protocol msn-im yahoo-im
drop-connection log
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect pptp
policy-map type inspect http P2P_HTTP
parameters
match request uri regex _default_gator
drop-connection log
match request uri regex _default_x-kazaa-network
drop-connection log
match request uri regex _default_msn-messenger
drop-connection log
match request uri regex _default_gnu-http-tunnel_arg
drop-connection log
policy-map IM_P2P
class imblock
inspect im impolicy
class P2P
inspect http P2P_HTTP
!
service-policy global_policy global
service-policy IM_P2P interface inside
prompt hostname context
: end
asdm image disk0:/asdm-524.bin
asdm location Server1 255.255.255.255 inside
asdm location IP_ICE 255.255.255.255 inside
asdm location outside-network 255.255.255.0 inside
asdm location SERVER 255.255.255.255 inside
no asdm history enable
What is wrong? Everything Works well except port forwarding.
Andreas
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
