- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA 5505 with VLAN trunk to Switch 2960
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5505 with VLAN trunk to Switch 2960
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2018 07:18 AM - edited 02-21-2020 08:06 AM
Hello all
We have an ASA 5505 (V9.1) with sec+ and a Cisco WS-2960X-24TS-L.
3 VLAN's have been created on the ASA and the Switch. We made a NAT on the ASA for the public IP.
As of now, we are able to connect to the outside world directly on the inside VLAN of the ASA, but we aren't able to connect from the 3 VLAN's behind the Switch. Ping from the ASA to the Switch with VLAN doesn't work either.
We tried Packet Tracer and it's always mention "No Route to host".
We tried to use NAT and routing to send the traffic between the ASA and the Switch, but can't find anyhing.
Already searched the internet for 2 days straight, but not even the simplest tutorials aren't helping to pass our traffic. ip routing & same-security-traffic[..] don't work.
One other problem is the DNS 1.1.1.1 1.0.0.1 Cisco uses and adds or replace them by the DNS 9.9.9.9 etc. we want to use.
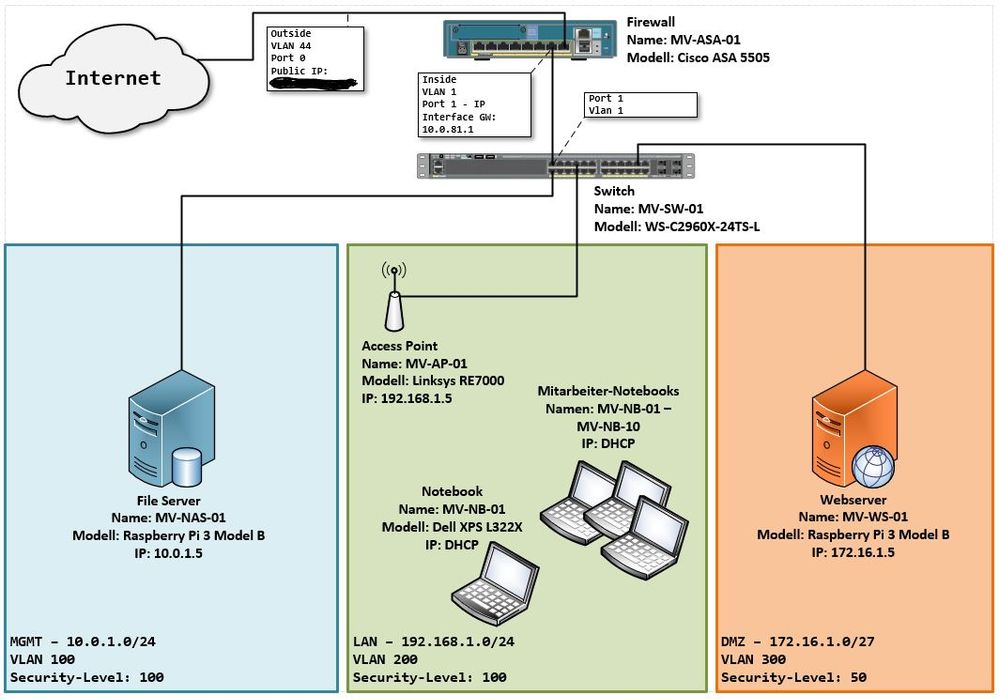 Infrastructure(Changes since last upload marked in bold)
Infrastructure(Changes since last upload marked in bold)
Config on ASA 5505:
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
:
ASA Version 9.1(5)21
!
hostname MV-ASA-01
domain-name vollpinsel.local
enable password XXXXXXXXXXXXXXX encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
!
interface Ethernet0/0
switchport access vlan 44
!
interface Ethernet0/1
switchport trunk allowed vlan 1,100,200,300
switchport mode trunk
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
switchport access vlan 200
!
interface Vlan1
nameif inside
security-level 100
ip address 10.0.81.1 255.255.255.0
!
interface Vlan44
nameif outside
security-level 0
ip address xxx.public.ip.xxx 255.255.255.240
!
interface Vlan100
nameif MGMT
security-level 100
ip address 10.0.1.1 255.255.255.0
!
interface Vlan200
nameif LAN
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan300
no forward interface Vlan100
nameif DMZ
security-level 50
ip address 172.16.1.1 255.255.255.224
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns domain-lookup outside
dns domain-lookup LAN
dns server-group DefaultDNS
name-server 10.0.81.1
name-server 9.9.9.9
name-server 8.8.8.8
domain-name vollpinsel.local
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network inside_gateway
host 10.0.81.1
object network LAN
subnet 192.168.1.0 255.255.255.0
object network inside
subnet 10.0.81.0 255.255.255.0
object network MGMT
subnet 10.0.1.0 255.255.255.0
object network DMZ
subnet 172.16.1.0 255.255.255.224
object network LAN_gateway
host 192.168.1.1
object network MGMT_gateway
host 10.0.1.1
object-group icmp-type DM_INLINE_ICMP_1
icmp-object echo
icmp-object echo-reply
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_SERVICE_1
service-object ip
service-object icmp
service-object udp
service-object icmp6
service-object tcp
service-object tcp-udp destination eq echo
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object icmp
service-object udp
service-object tcp
service-object tcp-udp destination eq echo
access-list inside_access_in extended permit ip any any
access-list allow_icmp_LAN extended permit icmp any any
access-list LAN_access_in extended permit ip any any
access-list LAN_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
access-list MGMT_access_in extended permit object-group DM_INLINE_SERVICE_2 any any
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu MGMT 1500
mtu LAN 1500
mtu DMZ 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (any,outside) source dynamic any interfacenat (inside,LAN) source static any any no-proxy-arp
access-group inside_access_in in interface inside
access-group MGMT_access_in in interface MGMT
access-group LAN_access_in in interface LAN
route outside 0.0.0.0 0.0.0.0 xxx.public.ip.xxx 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http xxx.public.ip.xxx 255.255.255.255 inside
http 10.0.81.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
sysopt noproxyarp inside
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 10.0.81.0 255.255.255.0 inside
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
management-access inside
dhcpd dns 9.9.9.9
!
dhcpd address 10.0.81.5-10.0.81.7 inside
dhcpd dns 9.9.9.9 8.8.8.8 interface inside
dhcpd lease 86400 interface inside
dhcpd domain vollpinsel.local interface inside
dhcpd enable inside
!
dhcpd address 192.168.1.2-192.168.1.254 LAN
dhcpd dns 192.168.1.1 9.9.9.9 interface LAN
dhcpd lease 86400 interface LAN
dhcpd enable LAN
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password XXXXXXXXXXXXXX encrypted privilege 15
username mst password XXXXXXXXXXXXXXX encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
Config on 2960-X
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname MV-SW-01
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$7Csl$gEpWOn6KhSr7v6G00mTlT0
enable password xxxx
!
no aaa new-model
switch 1 provision ws-c2960x-24ts-l
ip routing
no ip cef optimize neighbor resolution
!
crypto pki trustpoint TP-self-signed-303306368
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-303306368
revocation-check none
rsakeypair TP-self-signed-303306368
!
crypto pki certificate chain TP-self-signed-303306368
certificate self-signed 01
30820229 [...]
quit
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
interface FastEthernet0
no ip address
no ip route-cache
shutdown
!
interface GigabitEthernet1/0/1
switchport trunk allowed vlan 1,100,200,300
switchport mode trunk
!
interface GigabitEthernet1/0/2
switchport access vlan 100
!
# vlan 100 until port 6
!
interface GigabitEthernet1/0/7
switchport access vlan 200
!
# vlan 200 until port 20
!
interface GigabitEthernet1/0/21
switchport access vlan 300
!
# vlan 300 until port 24
!
interface GigabitEthernet1/0/25
!
interface GigabitEthernet1/0/26
!
interface GigabitEthernet1/0/27
!
interface GigabitEthernet1/0/28
!
interface Vlan1
ip address 10.0.81.2 255.255.255.0
!
interface Vlan100
ip address 10.0.1.2 255.255.255.0
!
interface Vlan200
ip address 192.168.1.2 255.255.255.0
!
interface Vlan300
ip address 172.16.1.2 255.255.255.224
!
ip http server
ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 10.0.81.1
!
no vstack
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2018 08:27 AM
From the switch check these things;
Is port gi0//0/1 trunking (show interface trunk)?
Do you see any ARP entries for the VLANs other than 1(show arp)?
Can clients ping the SVI's of the switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2018 12:51 AM - edited 08-19-2018 11:23 PM
Thank you Collin for your quick reply.
Switch:
1. show int trunk
| Port | Mode | Encapsulation | Status | Native vlan |
| Gi1/0/1 | on | 802.1q | trunking | 1 |
| Port | Vlans allowed on trunk |
| Gi1/0/1 | 1,100,200,300 |
| Port | Vlans allowed and active in management domain |
| Gi1/0/1 | 1,100,200,300 |
| Port | Vlans in spanning tree forwarding state and not pruned |
| Gi1/0/1 | 1,100,200,300 |
2. ARP
| Protocol | Address | Age (min) | Type | Interface |
| Internet | 10.0.1.2 | - | ARPA | Vlan100 |
| Internet | 10.0.81.1 | 8 | ARPA | Vlan1 |
| Internet | 10.0.81.2 | - | ARPA | Vlan1 |
| Internet | 10.0.81.5 | 8 | ARPA | Vlan1 |
| Internet | 172.16.1.2 | - | ARPA | Vlan300 |
| Internet | 192.168.1.1 | 207 | ARPA | Vlan200 |
| Internet | 192.168.1.2 | - | ARPA | Vlan200 |
| Internet | 192.168.1.5 | 0 | ARPA | Vlan200 |
3. Ping SVI
Not possible, Vlan100,200,300 can only ping their own gateway.
4. Reaching the Internet
I don't know why, but the Vlans 100,200,300 behind the switch can finally reach the internet as of today.
5. We need
- Enable the communication between the Vlan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2018 06:59 AM
Your config for inter-VLAN access looks good. Can you try some traffic, check the logs and look for "Deny" or NAT log entries and post them?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2018 08:02 AM - edited 08-20-2018 08:25 AM
I mad some changes in the config. I have marked the changen in bold.
I still don't know why the 3 VLAN can't reach each other Gateway or ping the other laptops in these VLAN's.
From Vlan200(LAN) > Vlan100(MGMT):
The request goes to the ASA but the ASA is unable to locate the Vlan100:
"Failed to locate egress interface for ICMP from LAN:192.168.1.6/1 to 10.0.1.1/0"
Switch:
show ip interface brief
| Interface | IP-Adress | OK? | Method | Status | Protocol |
| Vlan1 | 10.0.81.2 | YES | NVRAM | up | up |
| Vlan100 | 10.0.1.2 | YES | NVRAM | up | up |
| Vlan200 | 192.168.1.2 | YES | NVRAM | up | up |
| Vlan300 | 172.16.1.2 | YES | NVRAM | up |
up |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2018 08:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2018 08:40 AM - edited 08-20-2018 11:26 PM
Yes. Vlan 1,100,200,300 are defined on the ASA and Switch. Only the endings of the IP are different.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
