- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA and policy based routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA and policy based routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2019 09:11 AM - edited 02-21-2020 08:44 AM
Hello,
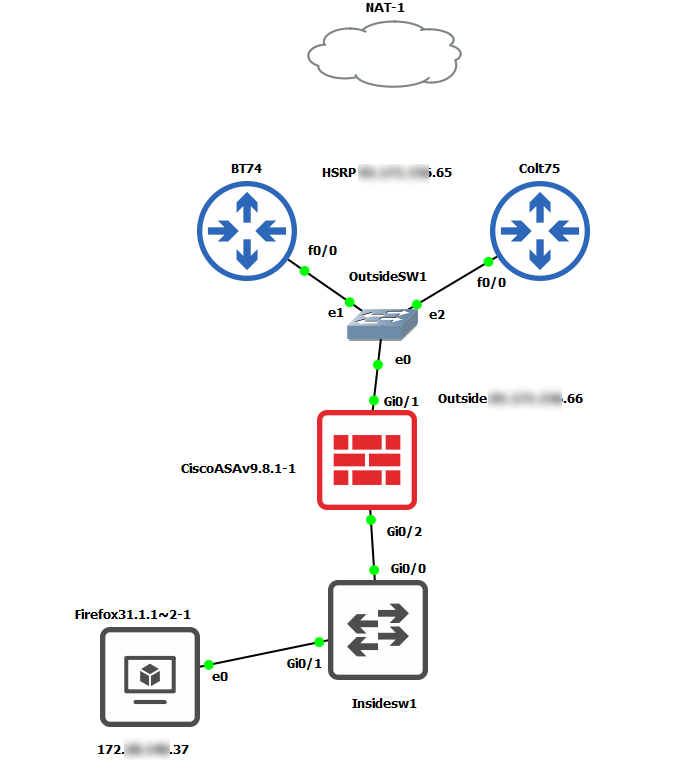
We have 2 x 5516x ASAs in active/standby and their outside interfaces go into a stack of 2 x 3750s. In this switch we also have our ISP routers which are setup as a HSRP. The active router is on 100MB line and the standby router is on 30MB.
Out 100MB line is quite heavily used and I was wondering if it's possible to router certain traffic to the standby router (physical IP) by using policy based routing?
I've only every seen this on routers and we don't manage our routers, our ISP do and will charge for any changes. I thought maybe the ASAs could do it?
As a test I was wondering if I can just route my laptop IP through the backup router for traffic destined for the internet on port 80 via the ASA and policy based routing on it?
Our current route for all users for http/https uses the 0.0.0.0 0.0.0.0 x.x.x.65 which is the HSRP public IP of the routers. THe primary router is on .71 and standby on .72.
Thanks in advanced for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2019 09:21 AM
https://www.cisco.com/c/en/us/td/docs/security/asa/asa99/configuration/general/asa-99-general-config/route-policy-based.html#ID-2182-00000032
Yes, you could configure PBR on ASA to route specific traffic to the standby router. But don't forget to add IP SLA to monitor the availability of the standby router's address. In short, the configuration would be like:
sla monitor 1
type echo protocol ipIcmpEcho x.x.x.72 interface outside
num-packets
timeout
frequency
sla monitor schedule 1 life forever start-time now
track 1 rtr 1 reachability
route-map ISP1 permit 10
match <interesting traffic here>
set ip next-hop verify-availability x.x.x.72 1 track 1
set ip next-hop x.x.x.65
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2019 09:54 AM
Thanks, so the IP SLA will monitor if the standby route is available for this policy based route and if not revert to the using the primary router?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2019 10:26 AM
Yes. Don't forget to apply the route-map to your interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2019 01:54 AM
Hi,
Do you have an example of the route map and does it go on the inside or outside interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2019 02:40 AM
sla monitor 1
type echo protocol ipIcmpEcho x.x.x.72 interface outside
num-packets
timeout
frequency
sla monitor schedule 1 life forever start-time now
track 1 rtr 1 reachability
access-list interesting_traffic exteneded permit tcp 192.168.0.0 255.255.255.0 any eq http
access-list interesting_traffic exteneded permit tcp 192.168.0.0 255.255.255.0 any eq https
route-map ISP1 permit 10
match ip address interesting_traffic
set ip next-hop verify-availability x.x.x.72 1 track 1
set ip next-hop x.x.x.65
interface Gi0/1
policy-route route-map ISP1
Note: you only need to apply the route-map on the ingress interface. (E.g. inside interface)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 01:03 AM
Thanks so much for your reply as I'm almost ready.
Can you just proof read this before I apply. I want to just test this against my laptop IP first before applying to a subnet:
This public IPs are slightly different and now I'm in the office I have been able to check what they end in.
ASA interfaces are:
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address x.x.x.66 255.255.255.224 standby x.x.x.67
ospf cost 10
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 172.x.10.1 255.255.255.0 standby 172.x.10.2
ospf cost 10
ISP routers
Standby Router x.x.x.75
Primary Router x.x.x.74
HSRP x.x.x.65
172.x.140.37 is me
IP SLA
This is to track the standby router is reachable.
sla monitor 1
type echo protocol ipIcmpEcho x.x.x.75 interface outside
num-packets
timeout
frequency
sla monitor schedule 1 life forever start-time now
track 1 rtr 1 reachability
ACL
This it the ACL the policy will only look at and is for my workstation and on tcp/80 and tcp/443 traffic only
access-list interesting_traffic extended permit tcp host 172.x.140.37 any eq http
access-list interesting_traffic extended permit tcp host 172.x.140.37 any eq https
Route Map
This route map will work only if the traffic is matching the ACLs called 'interesting_traffic' and if so set the next hop to the standby router of x.x.x.75, but only if it's reachable (track 1) and if it is not then it will fall back to x.x.x.65 which is the HSRP virtual IP of the 2 ISP routers.
route-map ISP1 permit 10
match ip address interesting_traffic
set ip next-hop verify-availability x.x.x.75 1 track 1
set ip next-hop x.x.x.65
Apply to interface
The above will only work once applied and to do this it has to be applied to the 'inside' interface and not the 'outside'
interface Gig1/2
policy-route route-map ISP1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 03:22 AM
It look good to me.
But it's highly recommended to build a lab on GNS3 or real lab environment before deploy it into production.
Especially you can't just shutdown the x.x.x.75 to verify the failover in production environment, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 03:55 AM - edited 02-04-2019 04:09 AM
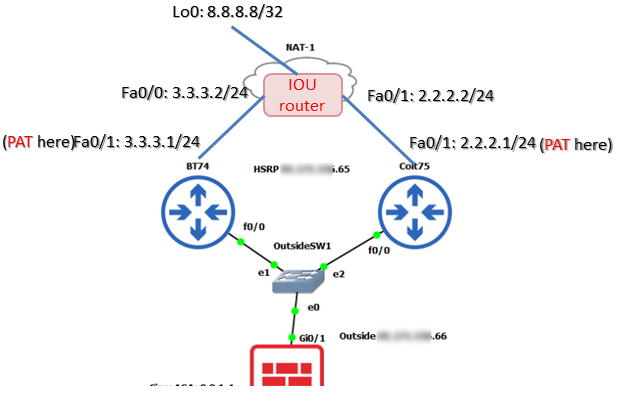
Funny you say that I am using GNS3 for this. Will let you know how it goes.
I use GNS3 all the time, best tool ever, especially for my exams etc.
This is what I will do, however I'm not sure if I should add a NAT and connect to my real work subnet, or somehow put a simple device beyond the ISP routers to test the policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 06:57 AM
Hello,
You could just place a router with loopback interface to simulate the Internet Address (E.g. 8.8.8.8). For example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 04:00 AM
Oh and what useful show commands can I use to check the policy is working?
I guess I can also capture traffic on one of the links to the routers and watch in wireshark.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 07:00 AM
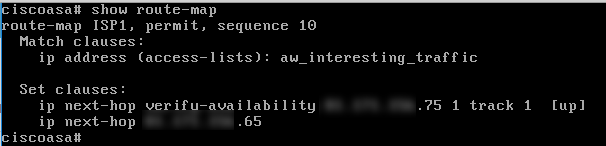
You could use "show route-map" to check the availability of next-hop, as well as the number packets hit this PBR.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 07:38 AM - edited 02-06-2019 11:09 AM
GNS3 is all running and the pings are hitting the remote device, but still taking the active HSRP path.
The route map is up too.
Had to reboot GNS3 and ping around to get things working.
If I ping from the PC on the inside I see it route via the active HSRP .74 IP and not .75. What I do is run Wireshark on the link.
Because the remote device in GNS3 is a vPCS I have used this ACL, maybe it's not recognised?
access-list aw_interesting_traffic extended permit icmp host 172.x.x.37 any echo
access-list aw_interesting_traffic extended permit icmp host 172.x.x.37 any echo-reply
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2019 05:12 AM
Do you see any hit count on your access list? Can you enable "debug policy-route" to have more detailed information?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2019 05:28 AM
What is the default gateway you have configured on inside PC?
If the route-map is hit, it would either via .65 (HSRP's MAC address) or .75 (Standby Router's MAC Address)..
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: