- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA Firepower FTD - Advanced Multiple IPSec Tunnel Config Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2019 10:19 AM - edited 02-21-2020 09:12 AM
Good Evening,
I have an ASA 5516-X running the traditional ASA image which is working fine at the moment however I would like to replace it with FTD.
I've got another ASA 5516-X which is running the latest FTD image, we are managing this locally through FTD, we do not have an FMC.
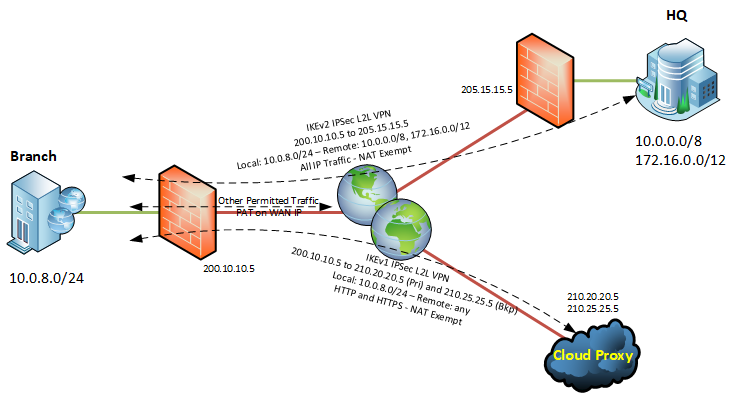
Our ASA is the branch office end of an IKEv2 IPSec L2L to our HQ.
For augment's sake lets say:
- The branch office end is 10.0.8.0/24 behind 200.10.10.5
- The HQ end is 10.0.0.0/8 and 172.16.0.0/12 behind 205.15.15.5
- Main mode with PSK
- All IP traffic to these two RFC 1918 private ranges from the branch office passes down the tunnel.
- All other traffic is split out and routed locally to the internet behind PAT (where the ACL permits).
Recently we have started using a cloud based transparent web proxy service using a second IPSec tunnel to direct HTTP and HTTPS traffic, with a NAT exemption, to the remote service.
- Branch end network 10.0.8.0/24
- Remote end network 0.0.0.0/0 (any) behind a primary and backup WAN IP (lets say 210.20.20.5 and 210.25.25.5)
- Ports TCP 80 and TCP 443
- Had to use an IKEv1 IPSec L2L because of the backup peer address requirement.
- Main mode with PSK
On the ASA software this works fine with the selection of the correct local and remote protected networks, priority in the crypto maps. The HQ crypto map has the lowest priority (20) and the proxy has priority (60).
When initially setting up the second tunnel a warning is received about potential overlap but the advanced settings of the crypto map were changed to reflect the destination ports in the protected network and everything has been fine.
Now I'm running into problems trying to replicate this in FTD.
I have the HQ L2L set up fine as a IKEv2 IPSec with the same protected networks as above, however I cannot set up the cloud proxy L2L. When I try to replicate the configuration in the FTD GUI I just get a warning that the range overlaps with our HQ VPN and I cannot proceed any further. There is no option I can see to configure priorities for the tunnels or set specific destination ports for the remote protected networks to get this to work.
I also cannot see any way in FTD to specify a backup peer IP address, I tried comma separated but this is not accepted.
Does anyone have any advise or suggestions, can this even be achieved in FTD?
The only thing I could think of was specific destination protected network entries for the public internet facing ranges allocated by IANA but this would be a nightmare and also doesn't resolve the problem of only wanting to tunnel HTTP and HTTPS traffic down the second tunnel.
Thank you in advance
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2019 01:19 AM
overlapping subnets in crypto maps and NAT rules. ASA takes that with
warning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2019 01:19 AM
overlapping subnets in crypto maps and NAT rules. ASA takes that with
warning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2019 02:50 AM
Thank you for the information Mohammed, that's a shame but we will have to look at another approach to this
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide