- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA5512 9.2 port forwarding to inside
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 04:04 AM
how to I configuring the firewall
public client ---> ASA5512 ---> c3750x ---> c2960s ---> host (192.168.2.12 tcp 8888)
detail
ASA5512
outside : 10.10.10.254
inside : 192.168.0.1
c3750x
g0/0 : 192.168.0.2
g0/1 : 192.168.2.1
c2960s
g0/0 : 192.168.2.254
app host 192.168.2.12 tcp 8888
I would like to connect to the inside host 192.168.2.12 on tcp port 8888 from public client.
I tried to configuring ASA5512 port forwarding to the internal host but can not succeed.
please help me with the correct configuration, how can I did it.
kind regards,
Mano
Solved! Go to Solution.
- Labels:
-
Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 08:12 AM
If the port is random, you'll need to modify your ACL. E.g:-
"access-list OUTSIDE_IN extended permit tcp any4 object CEMs-DATA object-group CEMs-Port"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 08:51 AM
The packet-tracer output was "allow" because you specified the source port.
If you want the telnet to work, change the ACL as I provided in a previous response, this will allow traffic from any source port.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 04:11 AM
Hi,
How did you configure the ASA?
Below is an example, this would nat the traffic from the outside interface (you may need to change the the interface names inside/outside to match your names):-
object network SERVER
host 192.168.2.12
nat (inside,outside) static interface service tcp 8888 8888
Amend your existing access-list, e.g:-
access-list OUTSIDE_IN extended permit tcp any host 192.168.2.12 eq 8888
access-group OUTSIDE_IN in interface outside
If this does not work please provide your ASA configuration AND provide the output of the command "show nat".
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 06:14 AM
ASA Version 9.12(2)
!
hostname ASA5512X
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.10.10.254 255.255.255.252
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
boot system disk0:/asa9-12-2-smp-k8.bin
ftp mode passive
!
object network obj-192.168.2.12
host 192.168.2.12
description CEMs-DATA Logging host
nat (inside,outside) static interface service tcp 8888 8888
!
access-list Filter-Route standard permit 10.220.1.0 255.255.255.0
access-list outside_access_in extended permit tcp any object obj-192.168.2.12 eq 8888
access-group outside_access_in in interface outside
!
pager lines 24
logging enable
logging asdm informational
asdm image disk0:/asdm-7122.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
nat (inside,outside) source dynamic any interface
!
route-map Filter-Route permit 10
match ip address Filter-Route
!
router ospf 1
network 10.253.20.0 255.255.255.240 area 0
area 0
log-adj-changes
redistribute static subnets route-map Filter-Route
!
route outside 0.0.0.0 0.0.0.0 10.10.10.253 1
route inside 192.168.0.0 255.255.240.0 192.168.0.2 1
!
user-identity default-domain LOCAL
aaa authentication http console LOCAL
aaa authentication telnet console LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 management
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
sysopt connection tcpmss 1344
crypto ipsec ikev1 transform-set L2TP-IKE1-Transform-Set esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set L2TP-IKE1-Transform-Set mode transport
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map L2TP-MAP 10 set ikev1 transform-set L2TP-IKE1-Transform-Set
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev1 enable outside
crypto ikev1 policy 5
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
ssh 192.168.0.0 255.255.255.0 inside
ssh timeout 30
ssh version 1 2
ssh key-exchange group dh-group1-sha1
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
enable outside
hsts
enable
max-age 31536000
include-sub-domains
no preload
cache
disable
no error-recovery disable
!
class-map inspection_default
match default-inspection-traffic
!
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect pptp
inspect ipsec-pass-thru
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
: end
++++++++++++++++++++++++++
this is my configuration.
thank you, sir.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 06:25 AM
You didn't provide the output of "show nat" but I assume the traffic is actually hitting your existing nat rule "nat (inside,outside) source dynamic any interface"
Remove that rule using "no nat (inside,outside) source dynamic any interface" and then re-add using the command "nat (inside,outside) after-auto source dynamic any interface".
The difference between the different syntax being after-auto. This will move the dynamic rule to the bottom of the nat rules and will allow your static nat rule to be processed first.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 08:14 AM
Thank you for you're responded.
after I edited a configuration look like below:
ASA Version 9.12(2)
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 118.174.147.254 255.255.255.252
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
...
object network obj-192.168.2.12
host 192.168.2.12
description CEMs-DATA Logging host
nat (inside,outside) static interface service tcp 8888 8888
!
access-list outside_access_in extended permit tcp any object obj-192.168.2.12 eq 8888
access-list Filter-Route standard permit 10.220.1.0 255.255.255.0
...
access-group outside_access_in in interface outside
..
nat (inside,outside) after-auto source dynamic any interface
..
!
route-map Filter-Route permit 10
match ip address Filter-Route
+++++++++++++++++++++++++++++++++++
ASA5512X# sh nat
Manual NAT Policies (Section 1)
1 (inside) to (VPN-2) source static inside-obj iEngineer destination static Depo Depo
translate_hits = 0, untranslate_hits = 0
2 (inside) to (VPN-5) source static inside-obj iEngineer destination static Depo Depo
translate_hits = 0, untranslate_hits = 0
3 (outside) to (VPN-2) source static L2TP-Subnet iEngineer destination static Depo Depo no-proxy-arp
translate_hits = 0, untranslate_hits = 0
4 (outside) to (VPN-5) source static L2TP-Subnet iEngineer destination static Depo Depo no-proxy-arp
translate_hits = 0, untranslate_hits = 0
5 (inside) to (outside) source static Enginer-Server Enginer-Server
translate_hits = 5, untranslate_hits = 0
6 (outside) to (inside) source static L2TP-Subnet L2TP-Subnet destination static inside-obj-1 inside-obj-1 no-proxy-arp
translate_hits = 0, untranslate_hits = 0
7 (inside) to (outside) source static Energy-Minitry Energy-Minitry
translate_hits = 0, untranslate_hits = 0
8 (inside) to (outside) source dynamic inside-obj interface
translate_hits = 351, untranslate_hits = 27
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static obj-192.168.2.12 interface service tcp 8888 8888
translate_hits = 0, untranslate_hits = 0
Manual NAT Policies (Section 3)
1 (inside) to (outside) source dynamic any interface
translate_hits = 0, untranslate_hits = 0
best regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2019 02:22 AM
8 (inside) to (outside) source dynamic inside-obj interface
translate_hits = 351, untranslate_hits = 27
and re-add with after-auto to move to NAT Section 3 as you did previously.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2019 08:03 PM
I tried to reconfig again but no luck
configuration:
!
ASA Version 9.1(2)
!
hostname ASA5512X
names
ip local pool L2TP-Pool 192.168.12.1-192.168.12.10
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.10.10.254 255.255.255.252
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface GigabitEthernet0/4
nameif VPN5
security-level 50
ip address 10.253.20.14 255.255.255.252
ospf cost 20
ospf authentication null
!
interface GigabitEthernet0/5
nameif VPN3
security-level 50
ip address 10.253.20.10 255.255.255.252
ospf cost 10
ospf authentication null
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
boot system disk0:/asa912-smp-k8.bin
ftp mode passive
!
object network CEMs-DATA
host 192.168.2.12
description CEMs-DATA Logging host
!
object network inside-obj
subnet 192.168.0.0 255.255.240.0
!
object network ENG-MAX
subnet 10.232.217.128 255.255.255.224
!
object network inside-Maximo
subnet 10.220.1.0 255.255.255.0
!
object network PPTP-Server
host 192.168.2.5
!
object network L2TP-Subnet
subnet 192.168.12.0 255.255.255.240
!
object network inside-obj-1
subnet 192.168.0.0 255.255.128.0
!
object network Energy
host 192.168.11.2
!
object-group service CEMs-Port tcp
port-object eq 888
port-object eq 8888
!
access-list Filter-Route standard permit 10.220.1.0 255.255.255.0
access-list outside_access_in extended permit tcp any4 object PPTP-Server eq ssh
access-list outside_access_in extended permit udp any4 object PPTP-Server eq isakmp
access-list outside_access_in extended permit udp any4 object PPTP-Server eq 4500
access-list outside_access_in extended permit esp any4 object PPTP-Server
access-list outside_access_in extended permit ah any4 object PPTP-Server
access-list outside_access_in extended permit tcp any4 object Energy eq 8000
access-list outside_access_in extended permit tcp any4 object-group CEMs-Port object CEMs-DATA object-group CEMs-Port
access-list Split-Tunnel-ACL standard permit 192.168.100.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 192.168.20.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 10.232.217.128 255.255.255.224
access-list Split-Tunnel-ACL standard permit 192.168.0.0 255.255.240.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu VPN5 1500
mtu VPN3 1500
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
icmp permit any VPN5
icmp permit any VPN3
asdm image disk0:/asdm-713.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
!
nat (inside,VPN3) source static inside-obj IN-MAXdestination static ENG-MAX ENG-MAX
nat (inside,VPN5) source static inside-obj IN-MAXdestination static ENG-MAX ENG-MAX
nat (outside,VPN3) source static L2TP-Subnet IN-MAXdestination static ENG-MAX ENG-MAX no-proxy-arp
nat (outside,VPN5) source static L2TP-Subnet IN-MAXdestination static ENG-MAX ENG-MAX no-proxy-arp
nat (inside,outside) source static PPTP-Server PPTP-Server
nat (outside,inside) source static L2TP-Subnet L2TP-Subnet destination static inside-obj-1 inside-obj-1 no-proxy-arp
nat (inside,outside) source static Energy Energy
!
object network CEMs-DATA
nat (inside,outside) static interface service tcp 8888 8888
!
nat (inside,outside) after-auto source dynamic any interface
access-group outside_access_in in interface outside
!
route-map Filter-Route permit 10
match ip address Filter-Route
!
!
router ospf 1
network 10.253.20.0 255.255.255.240 area 0
area 0
log-adj-changes
redistribute static subnets route-map Filter-Route
!
route outside 0.0.0.0 0.0.0.0 10.10.10.253 1
route inside 10.220.1.0 255.255.255.0 192.168.0.2 1
route inside 192.168.0.0 255.255.240.0 192.168.0.2 1
route inside 192.168.20.0 255.255.255.0 192.168.0.2 1
route inside 192.168.100.0 255.255.255.0 192.168.0.2 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication http console LOCAL
aaa authentication telnet console LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
sysopt connection tcpmss 1344
crypto ipsec ikev1 transform-set L2TP-IKE1-Transform-Set esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set L2TP-IKE1-Transform-Set mode transport
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map L2TP-MAP 10 set ikev1 transform-set L2TP-IKE1-Transform-Set
crypto map L2TP-VPN-MAP 20 ipsec-isakmp dynamic L2TP-MAP
crypto map L2TP-VPN-MAP interface outside
crypto ca trustpool policy
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev1 enable outside
crypto ikev1 policy 5
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 192.168.0.0 255.255.240.0 inside
telnet 192.168.12.0 255.255.255.0 inside
telnet 10.232.217.151 255.255.255.255 VPN3
telnet timeout 5
ssh 223.25.216.40 255.255.255.248 outside
ssh 14.207.128.231 255.255.255.255 outside
ssh 112.142.0.0 255.255.0.0 outside
ssh 223.25.203.113 255.255.255.255 outside
ssh 192.168.0.0 255.255.240.0 inside
ssh 192.168.12.0 255.255.255.0 inside
ssh 192.168.0.0 255.255.255.0 inside
ssh timeout 30
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
enable outside
cache
disable
group-policy temp01 internal
group-policy temp01 attributes
vpn-tunnel-protocol ssl-clientless
webvpn
url-list none
group-policy L2TP-Policy internal
group-policy L2TP-Policy attributes
dns-server value 8.8.8.8 8.8.4.4
vpn-tunnel-protocol l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split-Tunnel-ACL
intercept-dhcp enable
!
tunnel-group DefaultRAGroup general-attributes
address-pool L2TP-Pool
default-group-policy L2TP-Policy
tunnel-group DefaultRAGroup ipsec-attributes
ikev1 pre-shared-key ****
tunnel-group DefaultRAGroup ppp-attributes
authentication ms-chap-v2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect pptp
inspect ipsec-pass-thru
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:***
: end
++++++++++++++++++++++++++++++++
C:\Users\engineer>telnet 10.10.10.254 8888
Connecting To 10.10.10.254...Could not open connection to the host, on port 8888: Connect failed
+++++++++++++++++++++++
ASA5512X# sh nat
Manual NAT Policies (Section 1)
1 (inside) to (InterLink-VPN3112) source static inside-obj IN-MAX destination static ENG-MAX ENG-MAX
translate_hits = 162, untranslate_hits = 181
2 (inside) to (True-i52599B) source static inside-obj IN-MAX destination static ENG-MAX ENG-MAX
translate_hits = 0, untranslate_hits = 0
3 (outside) to (InterLink-VPN3112) source static L2TP-Subnet IN-MAX destination static ENG-MAX ENG-MAX no-proxy-arp
translate_hits = 8, untranslate_hits = 8
4 (outside) to (True-i52599B) source static L2TP-Subnet IN-MAX destination static ENG-MAX ENG-MAX no-proxy-arp
translate_hits = 0, untranslate_hits = 0
5 (inside) to (outside) source static PPTP-Server PPTP-Server
translate_hits = 282, untranslate_hits = 125
6 (outside) to (inside) source static L2TP-Subnet L2TP-Subnet destination static inside-obj-1 inside-obj-1 no-proxy-arp
translate_hits = 450, untranslate_hits = 603
7 (inside) to (outside) source static Energy Energy
translate_hits = 0, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static CEMs-DATA interface service tcp 8888 8888
translate_hits = 0, untranslate_hits = 10
Manual NAT Policies (Section 3)
1 (inside) to (outside) source dynamic any interface
translate_hits = 190311, untranslate_hits = 25408
+++++++++++++
no translate hit
thank you sir.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 07:11 AM
packet-tracer input outside tcp 9.9.9.9 1024 <your outside interface ip> 8888
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 08:00 AM
Thank you for your advice.
ASA5512X# packet-tracer input outside tcp 9.9.9.9 1024 10.10.10.254 8888
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
object network CEMs-DATA
nat (inside,outside) static interface service tcp 8888 8888
Additional Information:
NAT divert to egress interface inside
Untranslate 118.174.147.254/8888 to 192.168.2.12/8888
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
+++++++++++++++++
ASA5512X# packet-tracer input outside tcp 9.9.9.9 1024 10.10.10.254 8888 detial
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
object network CEMs-DATA
nat (inside,outside) static interface service tcp 8888 8888
Additional Information:
NAT divert to egress interface inside
Untranslate 10.10.10.254/8888 to 192.168.2.12/8888
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fff9f7455a0, priority=11, domain=permit, deny=true
hits=448, user_data=0x5, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0, dscp=0x0
input_ifc=outside, output_ifc=any
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
best regards,
Lucifur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 08:12 AM
If the port is random, you'll need to modify your ACL. E.g:-
"access-list OUTSIDE_IN extended permit tcp any4 object CEMs-DATA object-group CEMs-Port"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 08:17 AM
ASA5512X# packet-tracer input outside tcp 9.9.9.9 8888 10.10.10.254 8888 detail
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
object network CEMs-DATA
nat (inside,outside) static interface service tcp 8888 8888
Additional Information:
NAT divert to egress interface inside
Untranslate 10.10.10.254/8888 to 192.168.2.12/8888
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in in interface outside
access-list outside_access_in extended permit tcp any object-group CEMs-Port object CEMs-DATA object-group CEMs-Port
object-group service CEMs-Port tcp
port-object eq 888
port-object eq 8888
object-group service CEMs-Port tcp
port-object eq 888
port-object eq 8888
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fff9f744390, priority=13, domain=permit, deny=false
hits=0, user_data=0x7fff9b7f1f00, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=8888, tag=0
dst ip/id=192.168.2.12, mask=255.255.255.255, port=8888, tag=0, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) after-auto source dynamic any interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fff9f756d80, priority=6, domain=nat, deny=false
hits=0, user_data=0x7fff9f641010, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=10.10.10.254, mask=255.255.255.255, port=0, tag=0, dscp=0x0
input_ifc=outside, output_ifc=inside
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fff9ec00e40, priority=0, domain=nat-per-session, deny=false
hits=9087, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fff9f5cffe0, priority=0, domain=inspect-ip-options, deny=true
hits=5598, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 6
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fffa0161440, priority=13, domain=ipsec-tunnel-flow, deny=true
hits=22, user_data=0x0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 7
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
object network CEMs-DATA
nat (inside,outside) static interface service tcp 8888 8888
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7fff9f779610, priority=6, domain=nat-reverse, deny=false
hits=1, user_data=0x7fff9f772850, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=192.168.2.12, mask=255.255.255.255, port=8888, tag=0, dscp=0x0
input_ifc=outside, output_ifc=inside
Phase: 8
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7fff9ec00e40, priority=0, domain=nat-per-session, deny=false
hits=9089, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 9
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7fff9f627870, priority=0, domain=inspect-ip-options, deny=true
hits=5927, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0, dscp=0x0
input_ifc=inside, output_ifc=any
Phase: 10
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 5945, packet dispatched to next module
Module information for forward flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Module information for reverse flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_tcp_normalizer
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 08:23 AM
C:\Users\engineer>telnet 10.10.10.254 8888
Connecting To 10.10.10.254...Could not open connection to the host, on port 8888: Connect failed
++++++++++++++++
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static CEMs-DATA interface service tcp 8888 8888
translate_hits = 0, untranslate_hits = 19
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2019 08:51 AM
The packet-tracer output was "allow" because you specified the source port.
If you want the telnet to work, change the ACL as I provided in a previous response, this will allow traffic from any source port.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
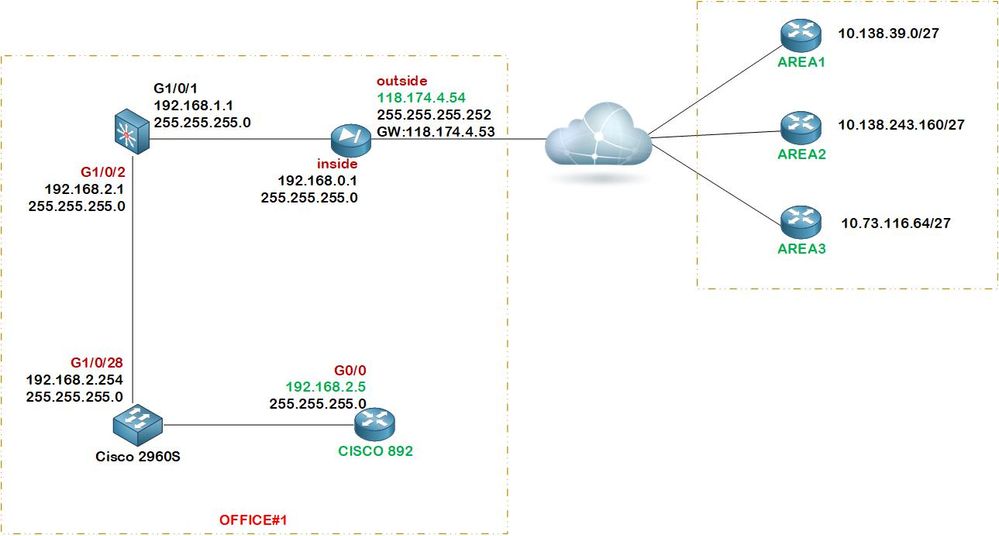
07-31-2019 08:36 AM
one more question sir.
how do I wrote a configuration file: connect from area A, B, C to
192.168.2.5 eq ssh
192.168.2.5 eq isakmp
192.168.2.5 eq 4500
esp -> 192.168.2.5
ah -> 192.168.2.5
best regards,
Lucifur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2019 09:09 AM
You would need another public IP address on the ASA and then you could create the NAT entries. Alternatively you could create a VPN tunnel terminating on the ASA itself.
HTH
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: