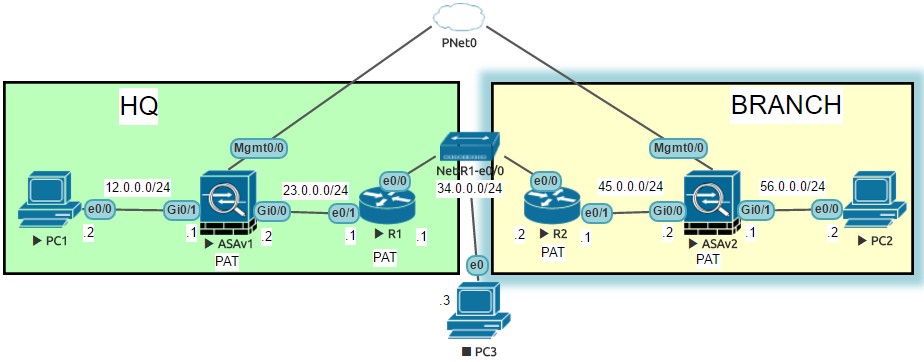
Usually I am using public ip to ASA directly but client situation is that they don't have public ip but they can use Static NAT or PAT in R1 or R2
REQUIREMENTS
- PC1 need to ping PC2 and vice versa
- PC3 need to connect to HQ using AnyConnect
QUESTIONS:
- anyone can gimme link on how to do Site-to-Site vpn behind double NAT.
I think I need to enable NAT-T in ASAv
- Am I correct to say I need to connect to R1 outside interface ip address from PC3 anyconnect
thanks
INFO
PC1:
#sh run
hostname PC1
interface Ethernet0/0
ip address 12.0.0.2 255.255.255.0
ip route 0.0.0.0 0.0.0.0 12.0.0.1
ASAv1:
ASA Version 9.5(2)204
hostname ASA1
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 23.0.0.2 255.255.255.0
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 12.0.0.1 255.255.255.0
interface Management0/0
nameif management
security-level 0
ip address 10.0.10.81 255.255.255.0
access-list inside_access_in extended permit icmp any any
access-list outside_access_in extended permit icmp any any
nat (inside,outside) after-auto source dynamic any interface
access-group outside_access_in in interface outside
access-group inside_access_in in interface inside
router eigrp 10
network 12.0.0.0 255.255.255.0
network 23.0.0.0 255.255.255.0
route outside 0.0.0.0 0.0.0.0 23.0.0.1 1
http server enable
http 10.0.10.0 255.255.255.0 management
policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect icmp
R1:
version 15.4
hostname R1
interface Ethernet0/0
ip address 34.0.0.1 255.255.255.0
ip nat outside
ip virtual-reassembly in
interface Ethernet0/1
ip address 23.0.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
router eigrp 10
network 23.0.0.0
network 34.0.0.0
ip nat inside source list LAN interface Ethernet0/0 overload
ip route 0.0.0.0 0.0.0.0 34.0.0.2
ip access-list standard LAN
permit 23.0.0.0 0.0.0.255
permit 12.0.0.0 0.0.0.255
R2:
version 15.4
hostname R2
interface Ethernet0/0
ip address 34.0.0.2 255.255.255.0
ip nat outside
ip virtual-reassembly in
interface Ethernet0/1
ip address 45.0.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
router eigrp 10
network 34.0.0.0
network 45.0.0.0
no ip http server
no ip http secure-server
ip nat inside source list LAN interface Ethernet0/0 overload
ip access-list standard LAN
permit 45.0.0.0 0.0.0.255
permit 56.0.0.0 0.0.0.255
ASAv2:
ASA Version 9.5(2)204
hostname ASA2
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 45.0.0.2 255.255.255.0
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 56.0.0.1 255.255.255.0
interface Management0/0
nameif management
security-level 0
ip address 10.0.10.82 255.255.255.0
access-list inside_access_in extended permit icmp any any
access-list outside_access_in extended permit icmp any any
nat (inside,outside) after-auto source dynamic any interface
access-group outside_access_in in interface outside
access-group inside_access_in in interface inside
router eigrp 10
network 45.0.0.0 255.255.255.0
network 56.0.0.0 255.255.255.0
route outside 0.0.0.0 0.0.0.0 45.0.0.1 1
http server enable
http 10.0.10.0 255.255.255.0 management
policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect icmp
PC2:
version 15.4
hostname PC2
interface Ethernet0/0
ip address 56.0.0.2 255.255.255.0
ip route 0.0.0.0 0.0.0.0 56.0.0.1