- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Blocked or blacklisted by the firewall preprocessor
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Blocked or blacklisted by the firewall preprocessor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2017 07:00 AM - edited 03-12-2019 02:09 AM
Hello,
when I issued a packet-tracer from my antispam to Internet on SMTP dest port, I see this results :
Phase: 12
Type: SNORT
Subtype:
Result: DROP
Config:
Additional Information:
Snort Trace:
Packet: TCP, SYN, seq 811220630
AppID: service unknown (0), application unknown (0)
Firewall: starting rule matching, zone 1 -> 1, geo 0 -> 0, vlan 0, sgt 65535, user 9999997, icmpType 0, icmpCode 0
Firewall: block rule, id 268434432, drop
Snort: processed decoder alerts or actions queue, drop
NAP id 2, IPS id 0, Verdict BLACKLIST, Blocked by Firewall
Snort Verdict: (black-list) black list this flow
Result:
input-interface: INSIDE
input-status: up
input-line-status: up
output-interface: OUT
output-status: up
output-line-status: up
Action: drop
Drop-reason: (firewall) Blocked or blacklisted by the firewall preprocessor
I can't find anyware to allow or white list this stream
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2017 12:21 AM
Hi,
I am running into the same problem. Did you find the solution for this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2018 08:01 AM
Hi,
I'm also encounter same issue , do you resolve this problem ?
And another question is how to tune Snort Verdict blacklisted time?
Regards,
Ben
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2018 09:18 AM
In such a case the destination address is in the Firepower blacklist - either the one downloaded automatically as part of the Cisco Security Intelligence (SI) feed or a local custom blacklist.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2018 04:39 PM
i have the same issue when failover to primary node. i am using FTD running version 6.2.3 -83. secondary node work normally.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2018 05:06 AM
Are the appliances managed locally (ASDM) or remotely(FMC). In either case you must make sure that the policies are applied identically to both nodes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 07:57 PM
"Drop-reason: (firewall) Blocked or blacklisted by the firewall preprocessor."
Any suggestions....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 02:04 AM
Are FTD 1 and FTD 2 in an HA pair?
We need some more details to ascertain possible causes of your problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 03:13 PM
(FW101) non-working
> show access-list | include DMVPN_Traffic_Hub_to_Hub
access-list CSM_FW_ACL_ line 140 remark rule-id 268439606: L7 RULE: DMVPN_Traffic_Hub_to_Hub
show access-list | include 268439606
access-list CSM_FW_ACL_ line 139 remark rule-id 268439606: ACCESS POLICY: FW101 - Mandatory
access-list CSM_FW_ACL_ line 140 remark rule-id 268439606: L7 RULE: DMVPN_Traffic_Hub_to_Hub
access-list CSM_FW_ACL_ line 141 advanced permit tcp ifc Interlink object-group FMC_INLINE_src_rule_268439606 ifc Interlink object-group FMC_INLINE_dst_rule_268439606 object-group ESP_50 rule-id 268439606 (hitcnt=0) 0x65342c53
access-list CSM_FW_ACL_ line 141 advanced permit tcp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 50 rule-id 268439606 (hitcnt=0) 0x7a797f98
access-list CSM_FW_ACL_ line 141 advanced permit tcp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 50 rule-id 268439606 (hitcnt=0) 0x0a8c2851
access-list CSM_FW_ACL_ line 141 advanced permit tcp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 50 rule-id 268439606 (hitcnt=0) 0x5effc1c3
access-list CSM_FW_ACL_ line 141 advanced permit tcp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 50 rule-id 268439606 (hitcnt=0) 0x146865f8
access-list CSM_FW_ACL_ line 142 advanced permit udp ifc Interlink object-group FMC_INLINE_src_rule_268439606 ifc Interlink object-group FMC_INLINE_dst_rule_268439606 object-group UDP_4500 rule-id 268439606 (hitcnt=0) 0x8d388f80
access-list CSM_FW_ACL_ line 142 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 4500 rule-id 268439606 (hitcnt=0) 0x79dc3f1d
access-list CSM_FW_ACL_ line 142 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 4500 rule-id 268439606 (hitcnt=0) 0x6ca0619f
access-list CSM_FW_ACL_ line 142 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 4500 rule-id 268439606 (hitcnt=0) 0xaef4147c
access-list CSM_FW_ACL_ line 142 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 4500 rule-id 268439606 (hitcnt=0) 0x0dfa067c
access-list CSM_FW_ACL_ line 143 advanced permit udp ifc Interlink object-group FMC_INLINE_src_rule_268439606 ifc Interlink object-group FMC_INLINE_dst_rule_268439606 object-group UDP_500 rule-id 268439606 (hitcnt=6) 0xdd1f3fe4
access-list CSM_FW_ACL_ line 143 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq isakmp rule-id 268439606 (hitcnt=0) 0xfd58fc5b
access-list CSM_FW_ACL_ line 143 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq isakmp rule-id 268439606 (hitcnt=0) 0x810563db
access-list CSM_FW_ACL_ line 143 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq isakmp rule-id 268439606 (hitcnt=6) 0xf3c91e26
access-list CSM_FW_ACL_ line 143 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq isakmp rule-id 268439606 (hitcnt=0) 0xe1fc9781
access-list CSM_FW_ACL_ line 144 advanced permit udp ifc Interlink object-group FMC_INLINE_src_rule_268439606 ifc Interlink object-group FMC_INLINE_dst_rule_268439606 object-group IPSec_over_UDP rule-id 268439606 (hitcnt=0) 0xe1b61e51
access-list CSM_FW_ACL_ line 144 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 10000 rule-id 268439606 (hitcnt=0) 0xfa9d9d5c
access-list CSM_FW_ACL_ line 144 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 10000 rule-id 268439606 (hitcnt=0) 0x4d1f57ad
access-list CSM_FW_ACL_ line 144 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 10000 rule-id 268439606 (hitcnt=0) 0x2247f007
access-list CSM_FW_ACL_ line 144 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 10000 rule-id 268439606 (hitcnt=0) 0xc20f6752
Below commands are from Expert mode in FTD, showing no out put in regards to rule-id 268439606 as it shows on working FTD at the bootm of the page
admin@FW101: cat /var/sf/detection_engines/17b6430e-5f23-11e9-b014-8e6fe6d5323f/ngfw.rules
(should appear some rule-id 268439606)
(FW201) Working
> show access-list | include DMVPN_Traffic_Hub_to_Hub
access-list CSM_FW_ACL_ line 273 remark rule-id 268439607: L7 RULE: DMVPN_Traffic_Hub_to_Hub
> show access-list | include 268439607
access-list CSM_FW_ACL_ line 272 remark rule-id 268439607: ACCESS POLICY: FW201 - Mandatory
access-list CSM_FW_ACL_ line 273 remark rule-id 268439607: L7 RULE: DMVPN_Traffic_Hub_to_Hub
access-list CSM_FW_ACL_ line 274 advanced permit tcp ifc Interlink object-group FMC_INLINE_src_rule_268439607 ifc Interlink object-group FMC_INLINE_dst_rule_268439607 object-group ESP_50 rule-id 268439607 (hitcnt=0) 0x945e36cb
access-list CSM_FW_ACL_ line 274 advanced permit tcp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 50 rule-id 268439607 (hitcnt=0) 0x7a797f98
access-list CSM_FW_ACL_ line 274 advanced permit tcp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 50 rule-id 268439607 (hitcnt=0) 0x0a8c2851
access-list CSM_FW_ACL_ line 274 advanced permit tcp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 50 rule-id 268439607 (hitcnt=0) 0x5effc1c3
access-list CSM_FW_ACL_ line 274 advanced permit tcp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 50 rule-id 268439607 (hitcnt=0) 0x146865f8
access-list CSM_FW_ACL_ line 275 advanced permit udp ifc Interlink object-group FMC_INLINE_src_rule_268439607 ifc Interlink object-group FMC_INLINE_dst_rule_268439607 object-group UDP_4500 rule-id 268439607 (hitcnt=0) 0xccac03cf
access-list CSM_FW_ACL_ line 275 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 4500 rule-id 268439607 (hitcnt=0) 0x79dc3f1d
access-list CSM_FW_ACL_ line 275 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 4500 rule-id 268439607 (hitcnt=0) 0x6ca0619f
access-list CSM_FW_ACL_ line 275 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 4500 rule-id 268439607 (hitcnt=0) 0xaef4147c
access-list CSM_FW_ACL_ line 275 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 4500 rule-id 268439607 (hitcnt=0) 0x0dfa067c
access-list CSM_FW_ACL_ line 276 advanced permit udp ifc Interlink object-group FMC_INLINE_src_rule_268439607 ifc Interlink object-group FMC_INLINE_dst_rule_268439607 object-group UDP_500 rule-id 268439607 (hitcnt=1) 0x202df959
access-list CSM_FW_ACL_ line 276 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq isakmp rule-id 268439607 (hitcnt=0) 0xfd58fc5b
access-list CSM_FW_ACL_ line 276 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq isakmp rule-id 268439607 (hitcnt=1) 0x810563db
access-list CSM_FW_ACL_ line 276 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq isakmp rule-id 268439607 (hitcnt=0) 0xf3c91e26
access-list CSM_FW_ACL_ line 276 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq isakmp rule-id 268439607 (hitcnt=0) 0xe1fc9781
access-list CSM_FW_ACL_ line 277 advanced permit udp ifc Interlink object-group FMC_INLINE_src_rule_268439607 ifc Interlink object-group FMC_INLINE_dst_rule_268439607 object-group IPSec_over_UDP rule-id 268439607 (hitcnt=0) 0x37d6d61a
access-list CSM_FW_ACL_ line 277 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 10000 rule-id 268439607 (hitcnt=0) 0xfa9d9d5c
access-list CSM_FW_ACL_ line 277 advanced permit udp ifc Interlink x.x.x.0 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 10000 rule-id 268439607 (hitcnt=0) 0x4d1f57ad
access-list CSM_FW_ACL_ line 277 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.0 255.255.255.252 eq 10000 rule-id 268439607 (hitcnt=0) 0x2247f007
access-list CSM_FW_ACL_ line 277 advanced permit udp ifc Interlink x.x.x.4 255.255.255.252 ifc Interlink x.x.x.4 255.255.255.252 eq 10000 rule-id 268439607 (hitcnt=0) 0xc20f6752
FROM EXPERT MODE of FTD (CLI)
admin@FW201:~$ cat /var/sf/detection_engines/0b43cfec-a673-11e8-a02e-385aad3b79f3/ngfw.rules
268439607 allow 8 x.x.x.0 29 any 8 x.x.x.0 29 10000 any 17
268439607 allow 8 x.x.x.0 29 any 8 x.x.x.0 29 4500 any 17
268439607 allow 8 x.x.x.0 29 any 8 x.x.x.0 29 500 any 17
268439607 allow 8 x.x.x.0 29 any 8 x.x.x.0 29 50 any 6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 08:38 PM
If there aren't in an HA pair or cluster, how can they have the same configurations? Can you backup a step and tell us how you have them setup? Is this a lab?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 08:59 PM
Marvin,
I have 2x (2130) FTDs managed by FMC and all in production. Initially, we only needed 1 FTD and over the time things grew and added new FTD. Previously deployed FTD running version 6.2.3.12 and recently added FTD running version 6.2.1. Im unable to upgrade 6.2.1 to 6.2.3.12 therefore can not cluster/HA (TAC case logged).
Actually, I wasn't able to set up DMVPN/IPSec tunnels between our 2 HUBs which are behind each FTD. Tried running packet-tracer and seen this SNORT drop, now Im here and seeking advice on "Blocked or blacklisted by the firewall preprocessor". Mind you to establish tunnels between both HUBs traffic traverses thru both FTD
Question arises, should I wait to upgrade FTD 6.2.1 to 6.2.3.12 and then cluster/HA or should look for reason for DROP?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 10:06 PM - edited 07-08-2019 10:10 PM
To pass DMVPN/IPsec tunnels through the Firepower devices, you should allow the traffic in a prefilter rule - not an access control policy rule. You will need to allow:
UDP/500,
UDP/4500 and
ESP/AH (IP proto 50/51) depending on configuration.
...to your hub address. The action should be "Fastpath".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 06:33 PM
As your last post, jsut making sure that when using DMVPN/IPSec tunnels then should ONLY use Prefilter not ACP rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:48 PM
You're welcome.
Yes, that's correct - only prefilter it with Fastpath action. Since the traffic is IPsec encapsulated and coming from known endpoints, none of the NGIPS processes (Snort, SI, Malware detection etc.) can add any value so prefilter will just Fastpath the DMVPN traffic to the post-processing stages (ALG, egress interface selection etc.).
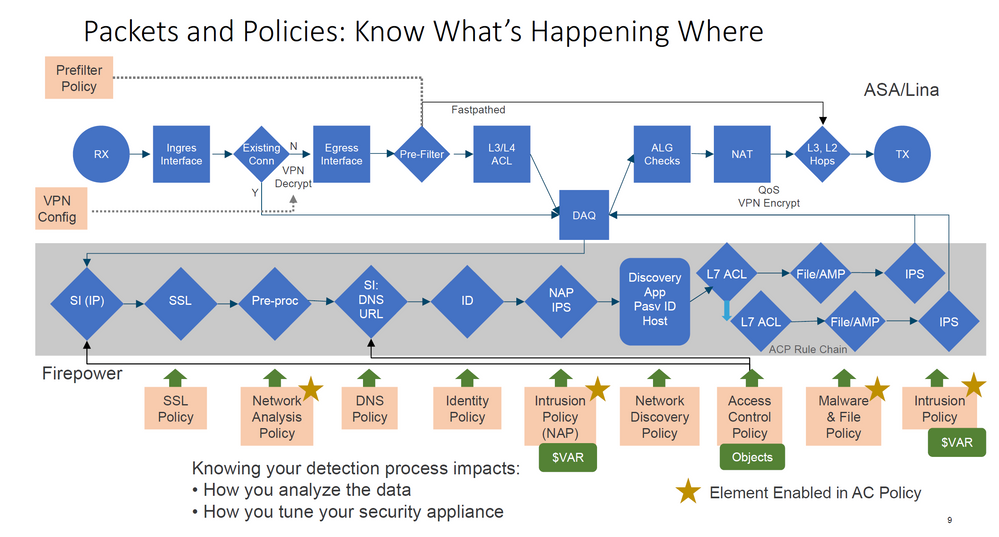
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2018 10:26 PM
hello,
i was the same issue but cisco tag help me find the reason
your output contain the blocking line id
Firewall: block rule, id 268434432, drop
in your situation it is 268434432
you must go to firepower applianca cli and connect to FTD
if promt is "ASB-HO-FTD-A# " connect to FTD
ASB-HO-FTD-A# connect ftd
then go to expert mode by typeng next commang
> expert
do the next linux command ( 1ac0cb9a-0cd2-11e8-8c50-8f0e1cebbe73 part is different for each appliance )
cat /var/sf/detection_engines/1ac0cb9a-0cd2-11e8-8c50-8f0e1cebbe73/ngfw.rules
if you have problem with doing privious step then
- type "cat /var/sf/detection_engines/"
- press tab button
- append "ngfw.rules"
after this you will see all ACL and ID of each ACE
find the one from packet tracer output " 268434432 "
probably you must have permit statement for traffic before this point.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


