- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: CISCO 5515x First Setup - Newbie
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CISCO 5515x First Setup - Newbie
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 06:16 AM - edited 02-21-2020 08:34 AM
Hi, hope I am posting in the right area...
I have inherited the responsibility for this wiped CISCO 5515x after the company split up, etc ...
I have managed to learn how to login, using Mac OSX, Terminal, etc and wipe and do a basic setup config.
I have then added some simple IPs for inside and outside and got the network running over DHCP and have access over the management port.
But I am stumped getting onto the internet between inside and outside.
I attach the config and some screen shots to give you an indication of where I am up to.
I'm not needing a complex setup, just get it working so people can DHCP onto the network and access the internet, LAN to LAN.
I have read a lot of posts here, online and videos to get this far ... any help at this basic hick-up very welcome.
Help in basic terms please, preferably using the ADSM Interface for this sacrificial Newbie :-)
Thank you.
ciscoasa# sh run
: Saved
:
ASA Version 9.1(2)
!
hostname ciscoasa
domain-name oc.lan
enable p-s-w--d *********************** encrypted
names
!
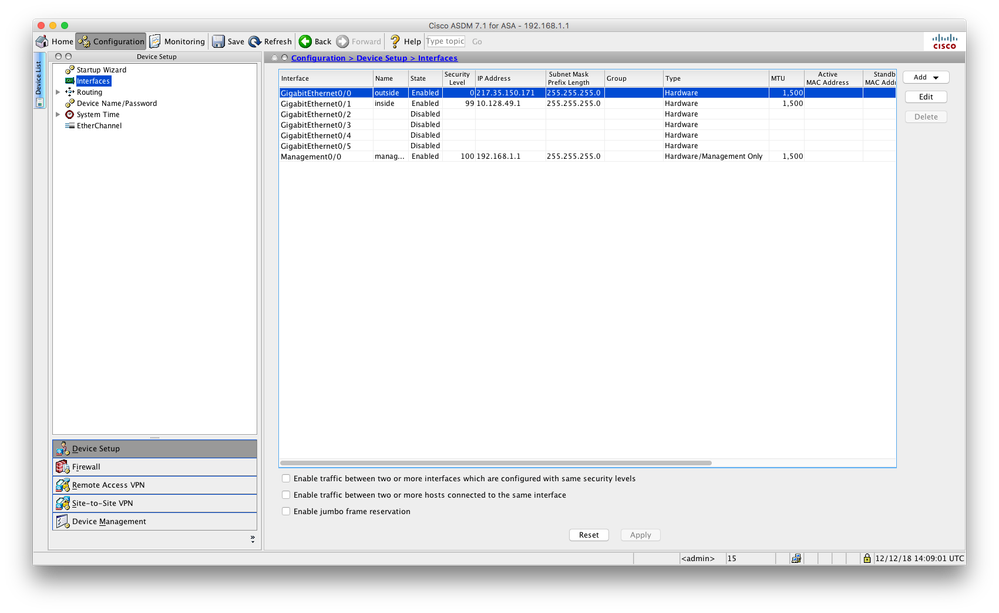
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 217.35.150.171 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 99
ip address 10.128.49.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
ftp mode -whateveristhebasicsettinghereisset-
dns server-group DefaultDNS
domain-name oc.lan
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd address 10.128.49.2-10.128.49.200 inside
dhcpd dns 8.8.8.8 8.8.4.4 interface inside
dhcpd enable inside
!
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:ff3011399f6276bfc9048b82e5c433b9
: end
ciscoasa#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 06:17 AM
edit:
I'm not needing a complex setup, just get it working so people can DHCP onto the network and access the internet, LAN to WAN to LAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 06:56 AM
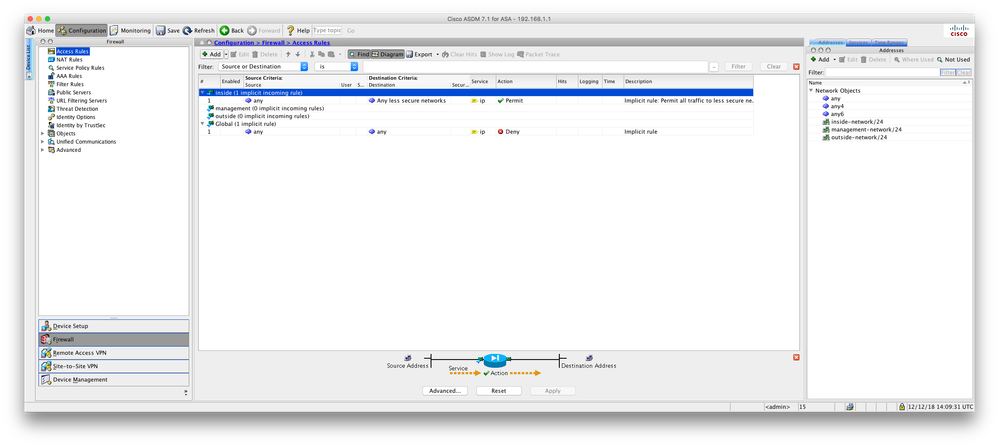
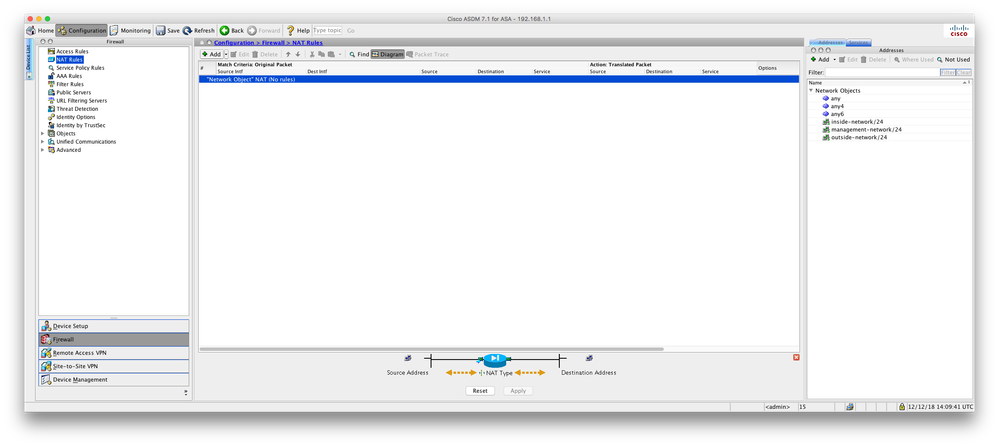
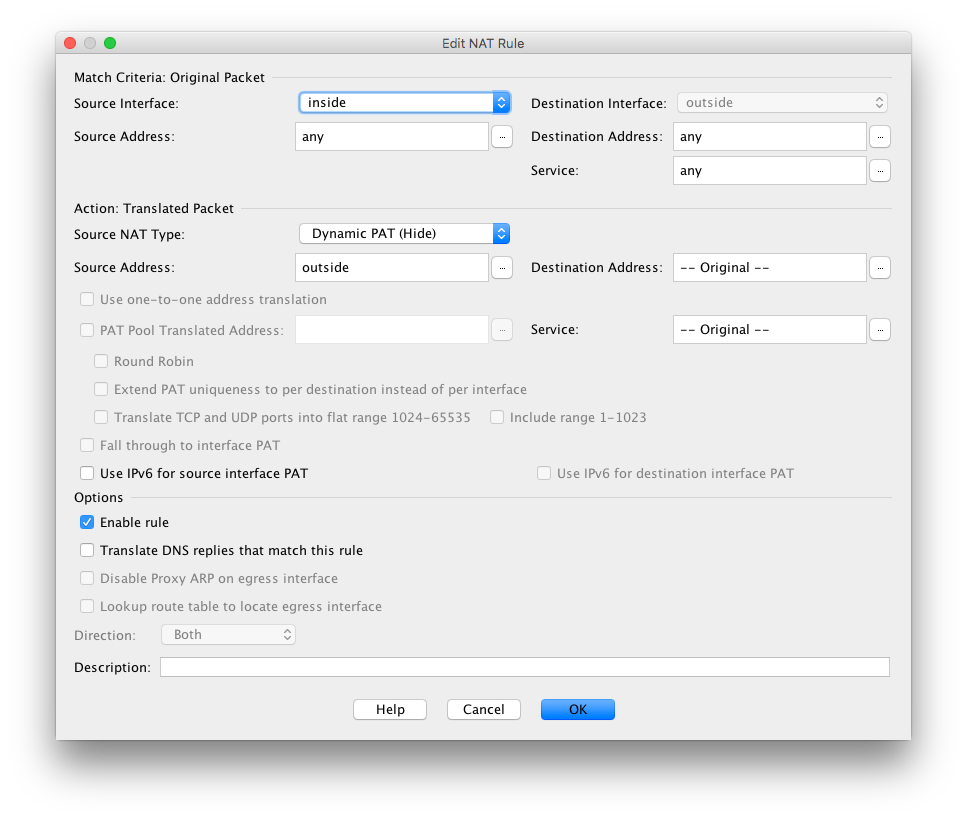
To get internet access you'll need nat, e.g:-
nat (inside,outside) after-auto source dynamic any interface
Is the DHCP configuration you've defined working?
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:07 AM
Thanks RJI
yes DHCP on 10.128.49.x is working AOK
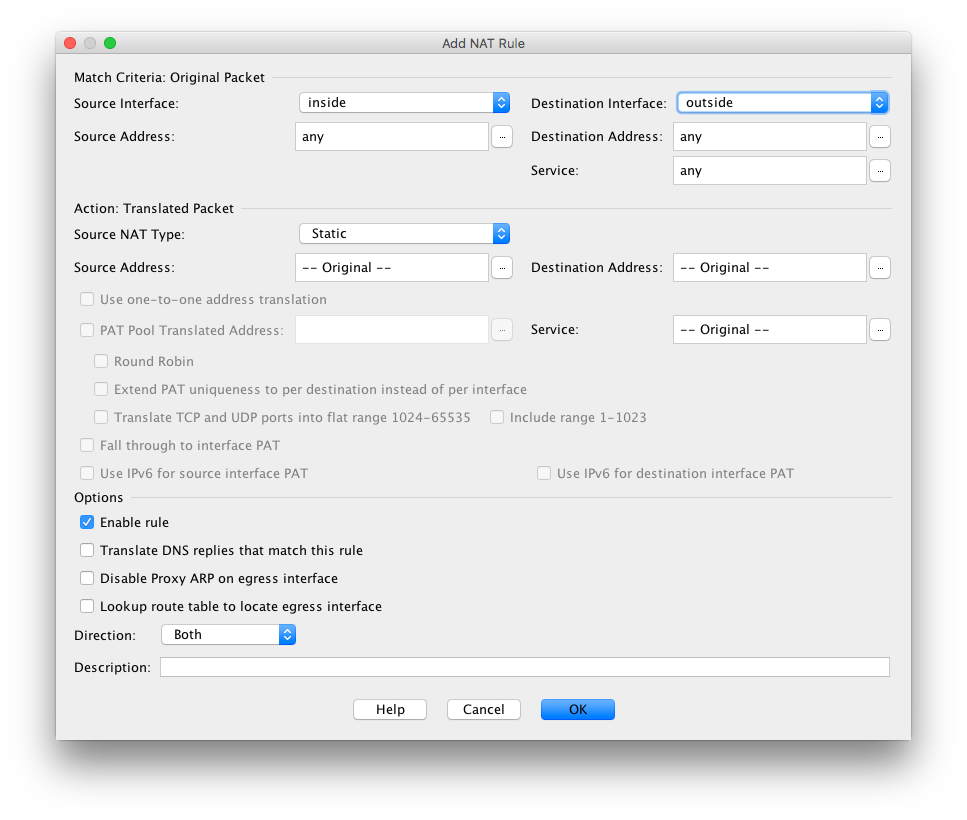
I tried to interpret your advice of 'nat (inside,outside) after-auto source dynamic any interface' and here is what I saw ...
The actual IPs for inside and outside will change one day, for now I hope to learn a simple working process. for this unfamiliar-to-me device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:19 AM
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:26 AM
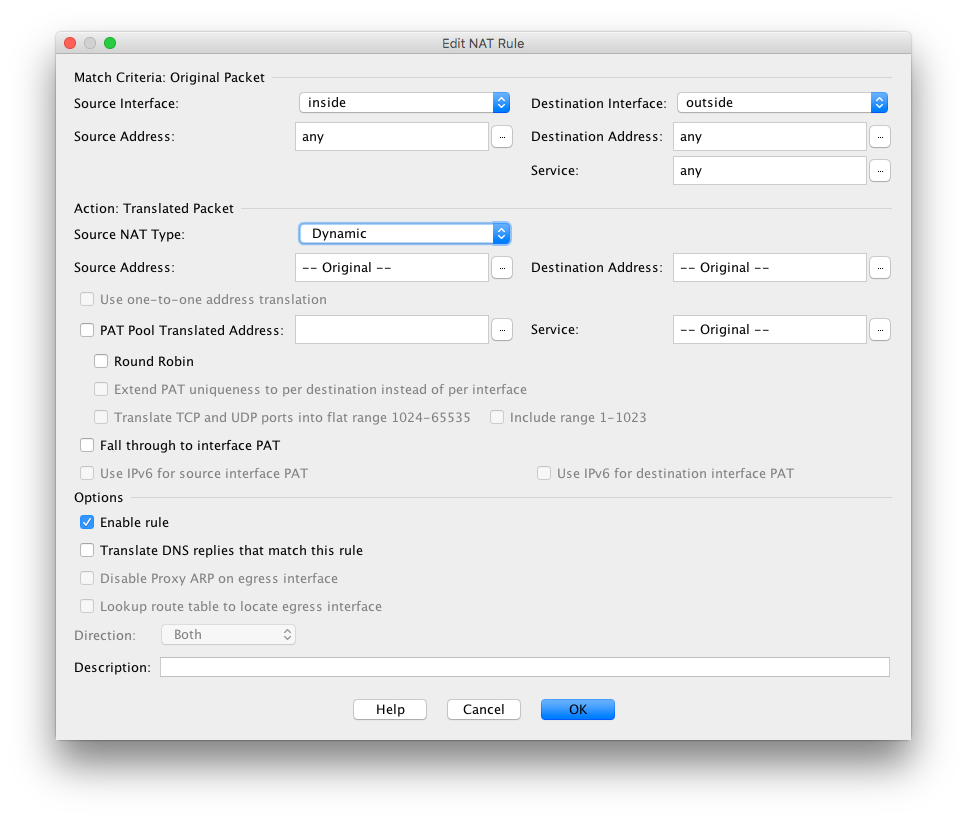
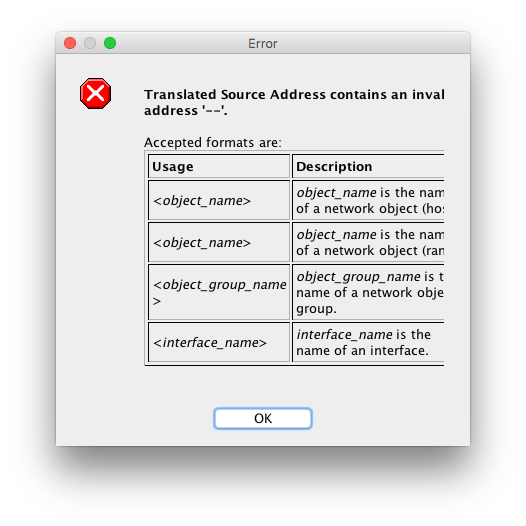
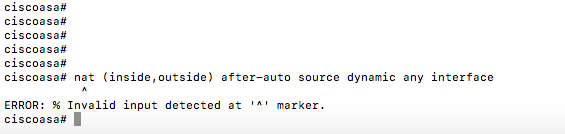
I tried changing to dynamic and got this:
... when you say 'Else just copy and paste the commands I supplied' do you mean in terminal like this?
... or somewhere in the ADSM ASA Interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:30 AM
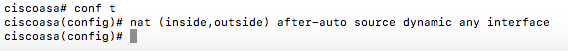
Then you can enter the nat command
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:41 AM
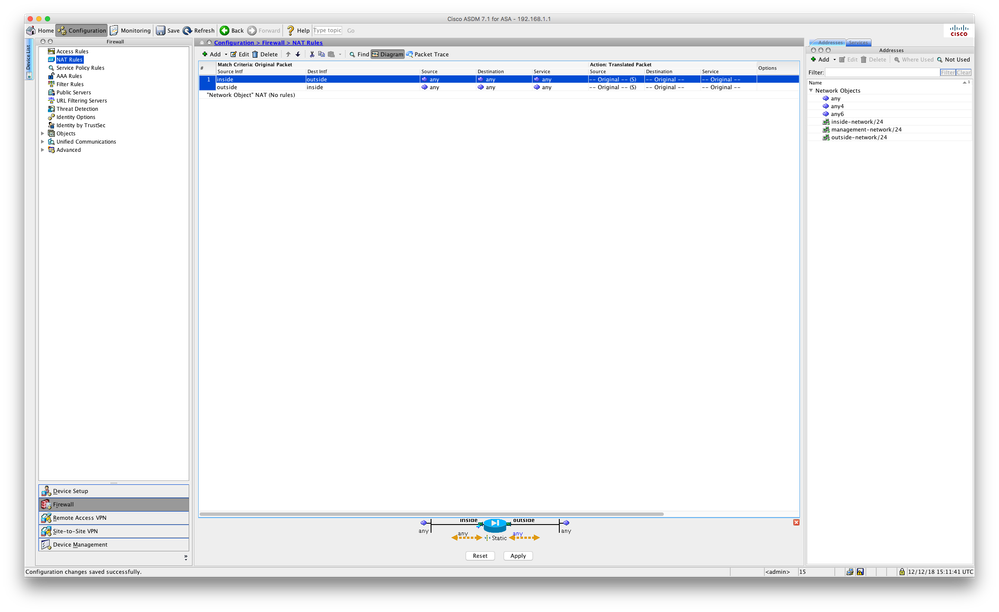
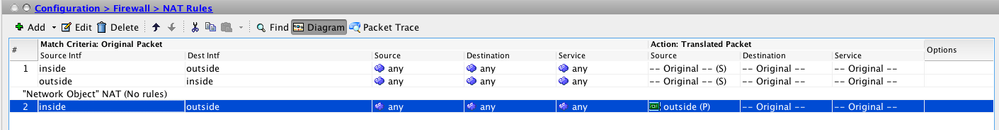
Cheers ... that worked as a command √
it resulted in this:
and this new 'Network Object':
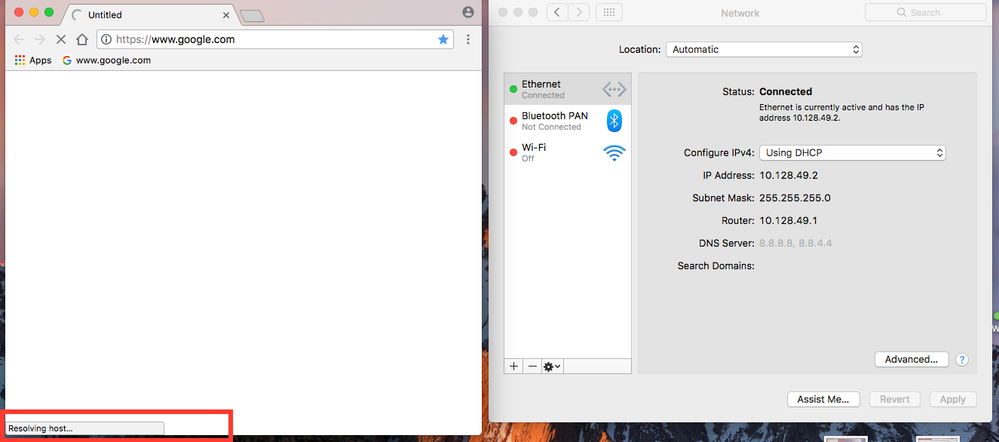
But clients cannot resolve to the www still unfortunately ...
Hoping my evidence above is OK as a Newbie ... I am sure other will follow one day with the same issue and hope all this helps :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:46 AM
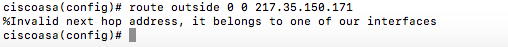
route outside 0 0 217.35.150.x
Replace the x with the ISP router's IP address and paste that command in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:59 AM
on interface 0 I have the ISP CAT5 cable
WAN IP: 217.35.150.x
WAN SUBNET: 255.255.255.0
WAN ROUTER: 217.35.150.x ... not sure where to set this up in the ASA
on interface 1 I have a CAT5 to a hub ... and fro the hub to all the computers
LAN IP [range] 10.128.49.x
LAN SUBNET: 255.255.255.0
LAN ROUTER: 10.128.49.1
LAN DNS: 8.8.8.8, 8.8.4.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 08:16 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 08:39 AM
Thanks RJI,
That's all very familiar setup values to my Netgear experiences ... :-)
Just this CISCO interface is New to me :-(
Mac terminal accepted that with no error.
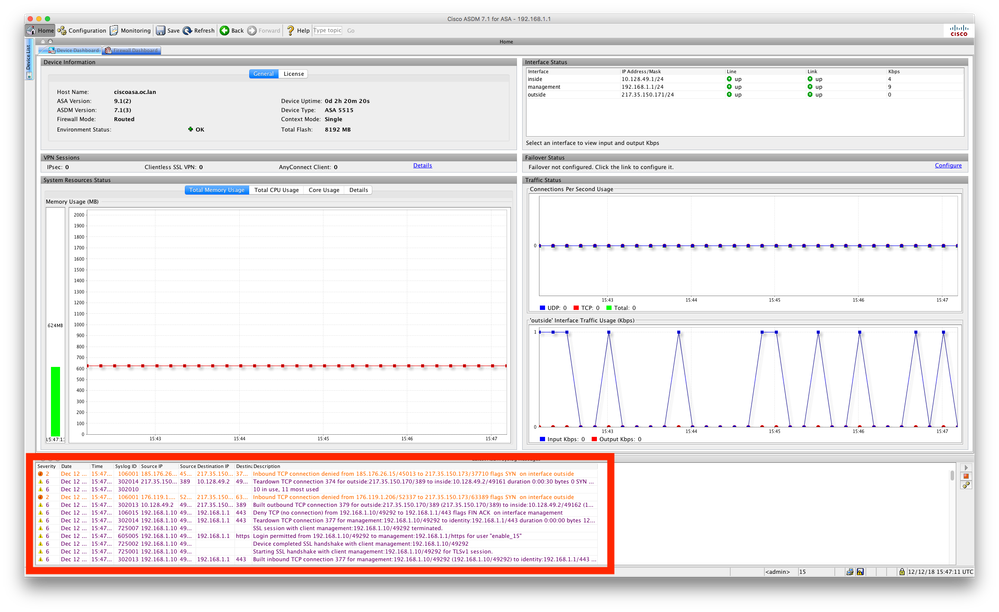
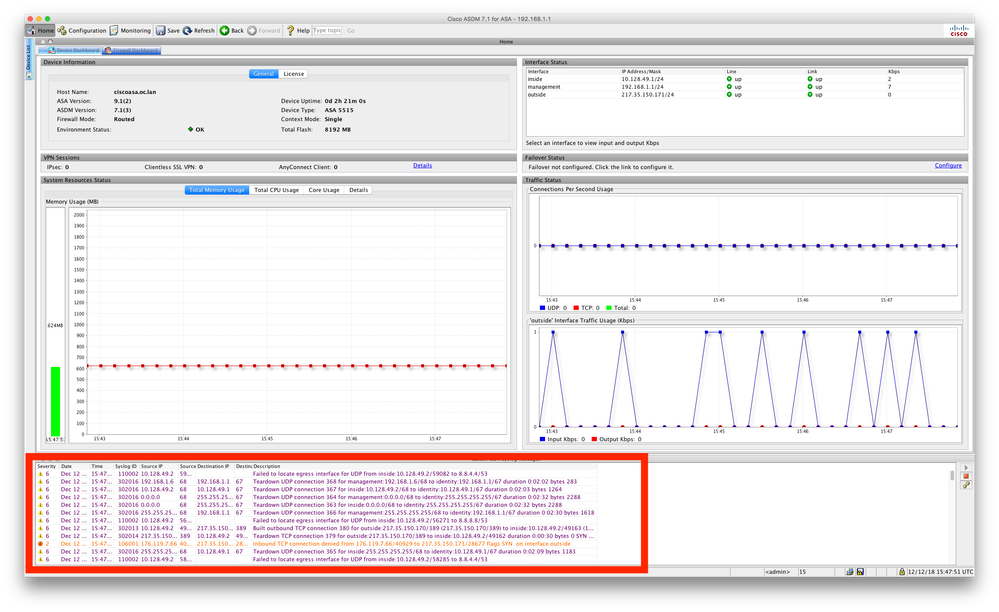
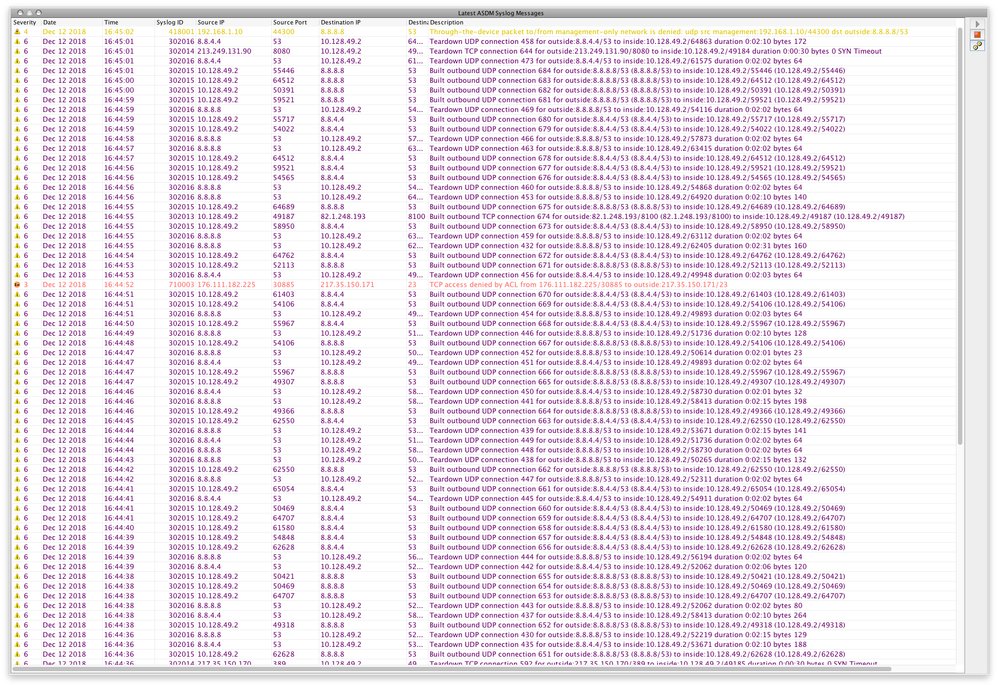
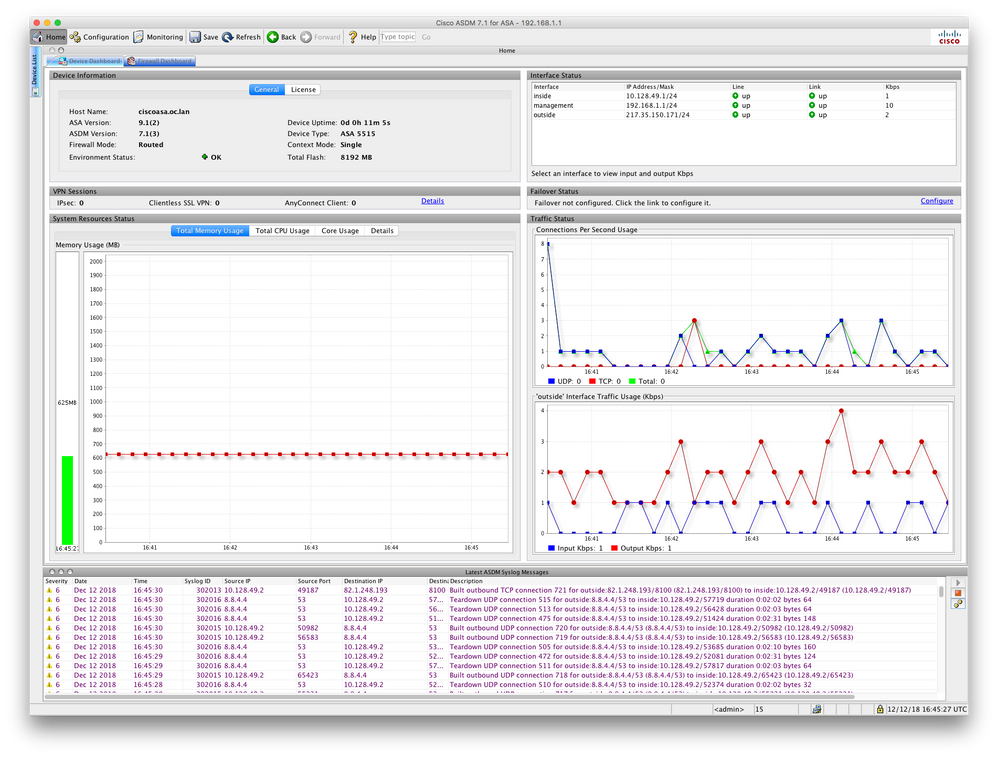
And indeed the traffic looks to be flowing in the Log view in the ADSM.
But Web Browsers on devices still display no web pages...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 08:41 AM
... also, does the managed interface port of 192.168.1.1 really need to have DHCP set too?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: