- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: CONNECTION BETWEEN TWO ASA 5506 -X FIREWALLS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CONNECTION BETWEEN TWO ASA 5506 -X FIREWALLS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2019 01:16 AM - edited 04-22-2019 01:17 AM
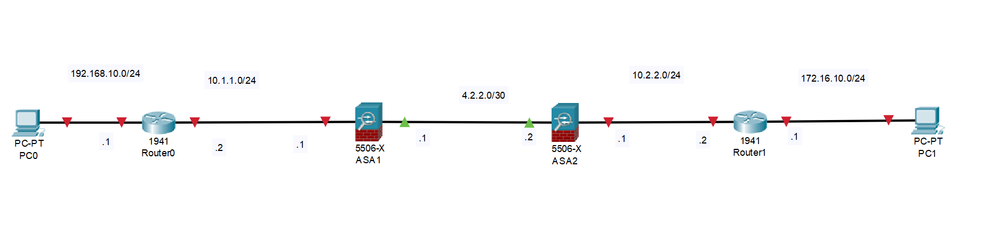
Hello.i have some problem.I need to connect two ASA 5506 firewall with each other .i have created the schema at packet tracer and then recreated it in real world but the same result
i can not make connection (icmp) behind the other firewall (for example from PC0 to PC1) .I have configured all interfaces. i have configured default routes on routers toward the ASAs. I alsa have written default routes on ASA firewalls toward each other and static routes toward their internal routes.I had checked also NAT config I also added icmp to the default global service policy for inspection and other protocols which i needed.But i can ping only from PC0 To ASA2 4.2.2.2 interface.What i have been missing i can not find
- Labels:
-
Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2019 04:32 AM
You have mentioned NAT config. Can you provide more information on what is being NAT'd and where.
Configs would help also.
I assume you can Ping to each PC from the local FW and Router?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2019 11:29 AM
I can ping from PC0 to ASA-2 4.2.2.2 interface but can not go behind ASA-2
I also can ping from PC1 to ASA-1 4.2.2.1 interface but can not go behind it
my nat config are both on ASA1 and ASA2
ASA-1(config-network-object)# nat (inside,outside) dynamic interface
ASA-2 (config-network-object)# nat (inside,outside) dynamic interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2019 02:22 PM
You may find that if you run Wireshark on say PC0 and try to ping it from PC1 you will see your icmp traffic reach PC0 with it then replying but not getting back to the source.
My understanding without labbing this up is that the return icmp traffic would be PAT'd again in opposite direction causing it to have a different source address. The asa won't have this 'existing' connection from the icmp inspect config and drop. I think during this icmp flow, at one point the source and destination of the traffic willl be either end of the Outside ASA interfaces, e.g source of 4.4.4.2 and destination 4.4.4.1 / vice versa.
If you want to have connectivity between them i would suggest configuring NAT exemption for the hosts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2019 02:31 PM
It doesn't work as expected because it is designed that way on ASA to deny ping through destined the ASA interface IP address. See link, https://community.cisco.com/t5/routing/asa-5585-x-unreachable-gateway-between-interfaces/m-p/3839525#M313418
There no way to override that security rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2019 03:02 PM
Hi,
@joseph.h.nguyen I think the original request was to ping through the ASAs from PC0 to PC1 - not pinging an ASA interface.
@shaig I assume you pinging the 172.16.10.x IP address of PC1? In which case @GRANT3779 is correct, the traffic would match your dynamic nat rule and be natted, so therefore not respond from the IP address you originally pinged.
Create a no-nat/nat exemption rule on both ASA's or alternatively create a static NAT for each PC.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 09:56 AM - edited 04-24-2019 10:05 AM
ASA-2#SH RUNning-config
: Saved
:
ASA Version 9.6(1)
!
hostname ASA-2
names
!
interface GigabitEthernet1/1
nameif OUTSIDE
security-level 100
ip address 4.2.2.2 255.255.255.252
!
interface GigabitEthernet1/2
nameif INSIDE
security-level 0
ip address 10.2.2.1 255.255.255.0
!
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
no security-level
no ip address
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
object network NAT
subnet 172.16.10.0 255.255.255.0
!
route INSIDE 172.16.10.0 255.255.255.0 10.2.2.2 1
route OUTSIDE 0.0.0.0 0.0.0.0 4.2.2.1 1
object network NAT
nat (INSIDE,OUTSIDE) dynamic interface
!
!
!
!
!
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
ASA-2#
ASA-1#SH RUNning-config
: Saved
:
ASA Version 9.6(1)
!
hostname ASA-1
names
!
interface GigabitEthernet1/1
nameif outside
security-level 100
ip address 4.2.2.1 255.255.255.252
!
interface GigabitEthernet1/2
nameif inside
security-level 0
ip address 10.1.1.1 255.255.255.0
!
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
no security-level
no ip address
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
object network NAT
subnet 192.168.10.0 255.255.255.0
!
route inside 192.168.10.0 255.255.255.0 10.1.1.2 1
route outside 0.0.0.0 0.0.0.0 4.2.2.2 1
!
!
!
object network NAT
nat (inside,outside) dynamic interface
!
!
!
!
!
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
ASA-1#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 12:09 PM
ASA-1#sh running-config
: Saved
:
ASA Version 9.6(1)
!
hostname ASA-1
names
!
interface GigabitEthernet1/1
nameif outside
security-level 100
ip address 4.2.2.1 255.255.255.252
!
interface GigabitEthernet1/2
nameif inside
security-level 0
ip address 10.1.1.1 255.255.255.0
!
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
no security-level
no ip address
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
object network NAT
subnet 192.168.10.0 255.255.255.0
!
route inside 192.168.10.0 255.255.255.0 10.1.1.2 1
route outside 0.0.0.0 0.0.0.0 4.2.2.2 1
!
!
!
object network NAT
nat (inside,outside) dynamic interface
!
!
!
!
!
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
ASA-1#
ASA-2#sh running-config
: Saved
:
ASA Version 9.6(1)
!
hostname ASA-2
names
!
interface GigabitEthernet1/1
nameif outside
security-level 100
ip address 4.2.2.2 255.255.255.252
!
interface GigabitEthernet1/2
nameif inside
security-level 0
ip address 10.2.2.1 255.255.255.0
!
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
no security-level
no ip address
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
object network NAT
subnet 172.16.10.0 255.255.255.0
!
route inside 172.16.10.0 255.255.255.0 10.2.2.2 1
route outside 0.0.0.0 0.0.0.0 4.2.2.1 1
!
!
!
object network NAT
nat (inside,outside) dynamic interface
!
!
!
!
!
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
ASA-2#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 12:12 PM
i have pasted the running-config of both ASAs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 01:12 PM
On ASA1 can you configure the following two objects, obviously stick in the IP addresses for each host.
Object network obj_pc0
Host "pc0 ip address"
Object network obj_pc1
Host "pc1ip address"
Then add the following NAT/NO NAT rule.
nat (inside,outside) source static obj_pc0 obj_pc0 destination static obj_pc1 obj_pc1
Add the same objects on ASA2 but then add the following reverse NONAT.
nat (inside,outside) source static obj_pc1 obj_pc1 destination static obj_pc0 obj_pc0
Test your ping
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: