- Cisco Community
- Technology and Support
- Security
- Network Security
- Data Center Firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Data Center Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 06:51 AM - edited 02-21-2020 06:52 AM
Gents,
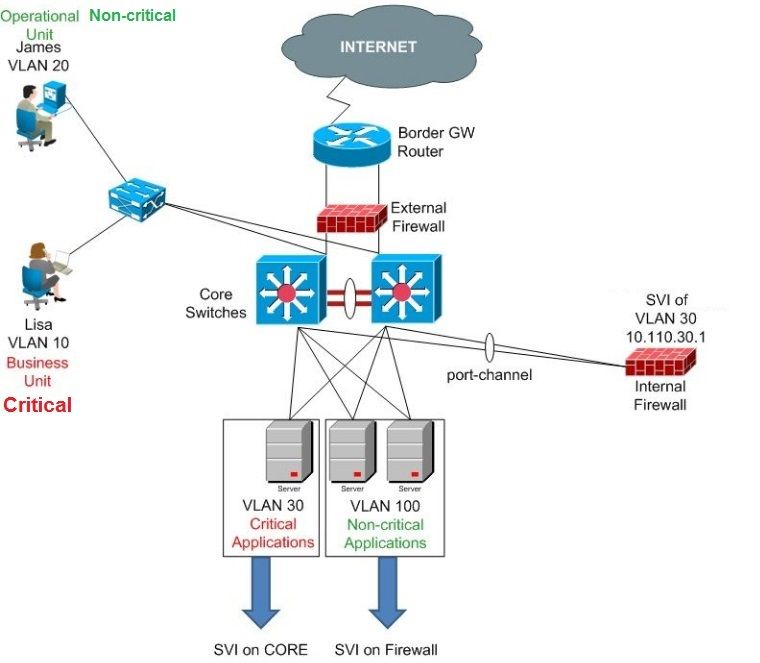
I would like to know your opinion on the below design to protect the servers of critical business applications from the operational staff.
I made my ASA the Gateway for the critical business applications' servers. Means any user accessing the critical business applications, network traffic needs to be allowed and inspected by the firewall rules.
The remaining all the SVIs for non-critical vlans stay on the Core.
Kindly, let me know if there's any issue you guys see with this design.
Thanking you all in advance!
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 11:05 AM
On your design, you're saying that internal firewall will have the SVI for vlan 30 but you have an arrow under critical servers saying the SVI will be on the core.
The design looks like ok even if you can handle that scenario in multiple ways.
You'll have to do routing between your Core and internal FW to make sure that everyone can access vlan 30, this said that means you won't only have SVI 30 but another interface to make the interconnection between core and internal FW.
Another simple way, is to keep SVI 30 on your core switch and add a firewall in transparent mode between your servers and the core switch.
Does that answer your question?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 11:35 AM
Thanks Franc, yup my bad thanks for noticing the mistakenly drawn arrow.
Let me know if the physical connection between firewall and Core remains the same if run the ASA in transparent mode.
It'd be great if you can share some sample configs I'm new to this scenario.
BTW does the transparent mode put extra load on the firewalls? OR it's less CPU sensitive than my idea of configuring SVIs on ASA?
Kind Regards,
Umer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 12:12 PM
Transparent mode won't add any extra load and can consume less as it won't do any routing stuff. However, in your case, the CPU consumption will be quite the same. It depends on the traffic the ASA needs to handle.
In terms of config (a quick example for interface configs, rest of configs like rules are same as routed mode):
interface gigabitethernet 0/0
nameif inside
security-level 100
bridge-group 1
!
interface gigabitethernet 0/1
nameif outside
security-level 0
bridge-group 1
!
interface bvi 1
ip address x.x.x.x 255.255.255.0 --> Ip in the same vlan 30. You can access asa through that IP. Bridge groups are used to allow multiple vlan used without adding security context (this is a quick and dirty explanation, here a doc where you can found more detailed information: https://www.cisco.com/c/en/us/td/docs/security/asa/asa92/configuration/general/asa-general-cli/interface-transparent.html)
In terms of physical and logical connection.
Your ASA has 2 interfaces, 1 called inside and 1 called outside. You will use 2 vlans (inside and outside) but keep the same L3 (SVI 30)
outside will be the interface facing the SVI (vlan 30), the inside will be connected to your switch using vlan YY. All your servers will be tagged (if ESX) or untagged (if Physical for example) to this new vlan YY.
A good drawing has been made on Cisco Learning, I'll drop you the link then you can have a better understanding: https://learningnetwork.cisco.com/thread/108406
Is that clear?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 12:29 PM
Thanks Bro, it really helps.
I'm gonna make the configs will share with you, shortly.
In your first comment you mentioned in my setup I do not need only an SVI but another type of connection between Core and ASA for routing. Please let me know what other connection I can make between them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 12:35 PM
You need an interconnection subnet between ASA and your core switch to tell all others svi on the core switch how to reach svi 30 which is behind the firewall
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 12:49 PM
In that case can I use static routes from Core to ASA and from ASA to Core.
Let's say I keep the SVI of vlan 30 on Core itself (instead of FW) and create subinterface on the Firewall, then connect them both via a 802.1Q trunk. Will that be okay I never tried just guessing as an idea.
But if my idea is okay then what would be the security configuration to protect the critical vlans from unsecure access of internal users. I just need the basic sample config which at least gives me right direction.
Your comments really helped me understanding the firewalling between my different user segments.
Thanks a lot!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 01:22 PM
If you keep ASA in routed mode with SVI in vlan 30 then you should add an interco subnet and play with static routes to tell other vlans how to reach vlan 30 and the invert as well.
You can’t have ASA in routed mode, keeping SVI on core, as all traffic won’t passthrough the firewall
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 01:31 PM
Got you!
But using the routed mode what will be the security configs simple ACLs? or something else to ensure the secure access between critical and non-critical vlans.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2017 01:50 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide