- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Edge Firewalls...Routing protocol or No?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2017 09:37 AM - edited 02-21-2020 07:02 AM
I think there are difference of opinions out there, so I'd like to ask the question...Firewalls, specifically the edge firewalls, routing protocol or not?
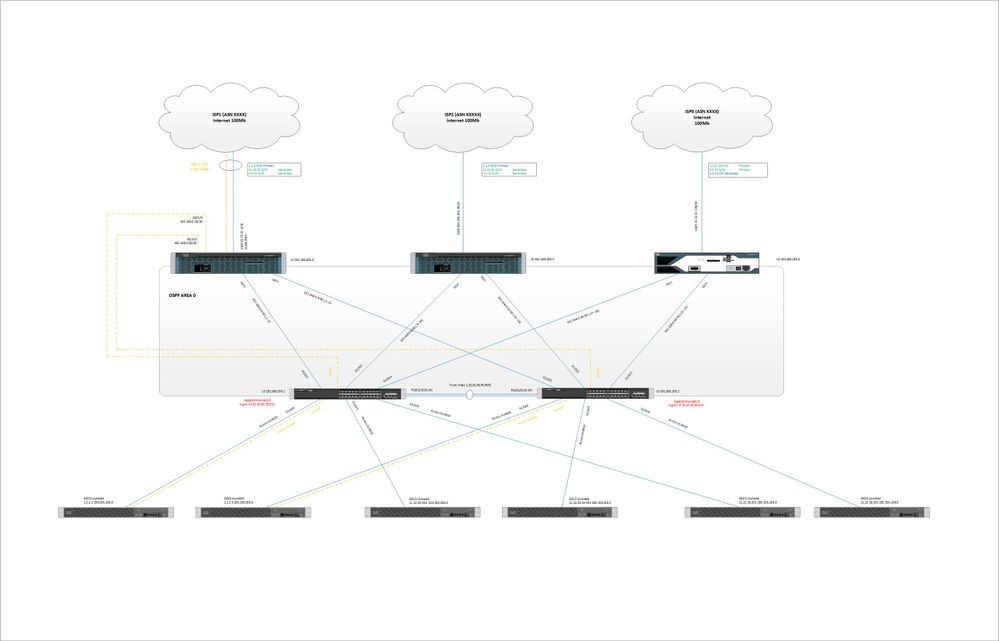
In a scenario of:
L2 SW -> DMZ Server Farm
|
|
ISP -> Router -> L2 SW -> Edge FW -> Core -> Core FW -> Server Agg Layer -> Server Farm.
So things I don't understand or have concerns on:
1. The ISP will run BGP between each other. So between the router and the Edge FW's I would think to run something like OSPF, if dynamic routing protocol would be chosen to run on the FW. In that space would you run public IP space or private IP space?
2. My core switches are Cat9ks not in a VSS (because it is not supported yet on my models), but also never will be. Rather using routing to decide failover and also leverage ECMP. What I struggle with is would you physically connect each Core switch to each FW in an HA pair Active/Standby? Or connect the core switches to the FW's on a 1 to 1 basis? Core 1 -> FW1 Core 2 -> FW2? My concern with this if a down stream core switch to the active FW fails the HA pair will failover when really there was nothing wrong with the active firewall. Maybe this is ok.
Thoughts?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 08:36 AM
For the Firewall edge routing, to control any routing attacks, I will use different protocols (1 for outside and 1 for inside). You can use BGP for outside and ospf for inside.
However, if your ISP is just sending a default route, there is no much to control and in that case you can decide if you want to go with static route.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2017 07:35 PM
Hi
You can run dynamic routing on edge firewall. I would suggest to run different routing protocol on outside and inside. This will allow router filtering between outside and inside. Also, to ensure a security, always configure device hardening.
I would continue with bg pl routing between your edge fw and your wan routers. Regarding your question for public or private IP, how all devices are currently connected? Public or private?
If you're out of public IP, then you can use private IPs. However, if you have a lot of public IPs, use public addresses. I personally use private IPs as most of customers haven't lot of public IPs.
Regarding your second question, as your 2 chassis aren't in VSS, if you connect both of them on your active firewall, you'll need to have 2 inside zone if you want to use both cat9k. Now, your Cat9k are in hsrp mode i guess, then you can just connect the 1st chassis with active fw and 2nd chassis with passive fw. Your ASA will failover to passive ASA when 1st Cat9k will crash because then ASA inside interface will crash as well.
And i assume that your both cat9k have routing adjacency then a traffic hitting 2nd cat9k chassis will be forwarded to 1st chassis took go out through active ASA.
Does that make sense?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 12:18 PM
If you're out of public IP, then you can use private IPs. However, if you have a lot of public IPs, use public addresses. I personally use private IPs as most of customers haven't lot of public IPs.
I am still lost on how you run a private space between the firewalls and the edge internet routers when the firewalls outside interface has to have a public IP address for NAT, how does that work? I don't want the edge routers doing the NAT. I also don't have Load Balancers to do the NAT rather than the firewalls.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 01:07 PM
Hi
Routing and NAT are different stuff. You can nat your traffic to a public IP on your firewall and transport it to other devices through private interconnection subnet. This is a common question and instead of giving you lot of explanation, I did a quick lab on Cisco Virl, just to extract some config and you can reproduce it yourself for testing purpose.
The idea is to nat a traffic on using a POOL or even a loopback.
You can do the same with PA but right now I don't have any PA in LAB then just did it with Cisco devices.
Config are very minimalist without any password or advanced features, purpose is just to show you, you can nat traffic on a public IP and having those devices interconnected using private subnets.
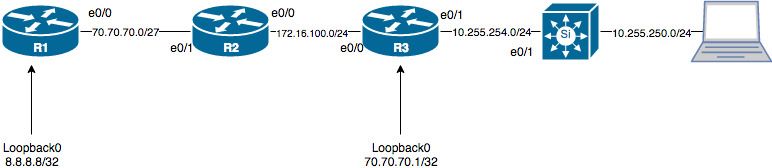
Here a lab design:
R1 would be your ISP, R2 your Edge router and R3 a firewall.
BGP between R1 and R2 and OSPF between R2 and R3.
Below some config examples for each routers:
R1:
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 70.70.70.3 YES manual up up
Loopback0 8.8.8.8 YES manual up up
router bgp 1
bgp log-neighbor-changes
redistribute connected
neighbor 70.70.70.2 remote-as 2
R2:
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 172.16.100.2 YES manual up up
Ethernet0/1 70.70.70.2 YES manual up up
router bgp 2
bgp log-neighbor-changes
neighbor 70.70.70.3 remote-as 1
router ospf 1
redistribute bgp 2 subnets
passive-interface default
no passive-interface Ethernet0/0
network 70.70.70.2 0.0.0.0 area 0
network 172.16.100.2 0.0.0.0 area 0
R3:
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 172.16.100.1 YES manual up up
Ethernet0/1 10.255.254.2 YES manual up up
Loopback0 70.70.70.1 YES manual up up
NVI0 172.16.100.1 YES unset up up
router ospf 1
passive-interface default
no passive-interface Ethernet0/0
network 70.70.70.1 0.0.0.0 area 0
network 172.16.100.1 0.0.0.0 area 0
ip nat inside source list NAT interface Loopback0 overload
Extended IP access list NAT
10 permit ip 10.0.0.0 0.255.255.255 any (15 matches)
Now, when I ping from host with IP 10.255.250.2 to 8.8.8.8, my IP is natted correctly to 70.70.70.1 and icmp works fine:
R1:
*Dec 28 20:57:35.724: ICMP: echo reply sent, src 8.8.8.8, dst 70.70.70.1, topology BASE, dscp 0 topoid 0
*Dec 28 20:57:37.727: ICMP: echo reply sent, src 8.8.8.8, dst 70.70.70.1, topology BASE, dscp 0 topoid 0
*Dec 28 20:57:38.730: ICMP: echo reply sent, src 8.8.8.8, dst 70.70.70.1, topology BASE, dscp 0 topoid 0
*Dec 28 20:57:39.733: ICMP: echo reply sent, src 8.8.8.8, dst 70.70.70.1, topology BASE, dscp 0 topoid 0
*Dec 28 20:57:40.737: ICMP: echo reply sent, src 8.8.8.8, dst 70.70.70.1, topology BASE, dscp 0 topoid 0
R3:
Pro Inside global Inside local Outside local Outside global
icmp 70.70.70.1:56155 10.255.250.2:56155 8.8.8.8:56155 8.8.8.8:56155
icmp 70.70.70.1:56411 10.255.250.2:56411 8.8.8.8:56411 8.8.8.8:56411
icmp 70.70.70.1:56667 10.255.250.2:56667 8.8.8.8:56667 8.8.8.8:56667
Hope that answers your question. Let me know if you need more info/help.
If I had a PA in demo, I would be able to setup a lab with same configs.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2017 07:59 AM - edited 12-29-2017 08:21 AM
I think for me it was more of understanding "how it works" I have never seen a scenario in that everything northbound of the firewall was private, but to your point smaller customers will not get a big address space so they have limits. I was always under the impression you didn't want to NAT on a router if you didn't have to. Maybe it was just people who choose not to do so, I have seen things like F5 taking in the public ranges and doing the NAT there, then forwarding to the firewall or even having the firewall forward the requests to the F5. I have worked with guy who live by the words, "remove nat from your firewall completely" they say it takes up resources and also creates a security vulnerability? I am not much of a security guy so I do not know how true that it.
Thanks for the "white board" per say. I am a much better visual learner.
Now if R3 is the firewall....there really isn't a "loopback"so how does that work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2017 11:53 AM
On PA, if I recall correctly, you can have loopbacks and nat using loopback interfaces. I couldn't say that 100% sure as I don't have any PA right now to connect to validate it.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2017 12:02 PM
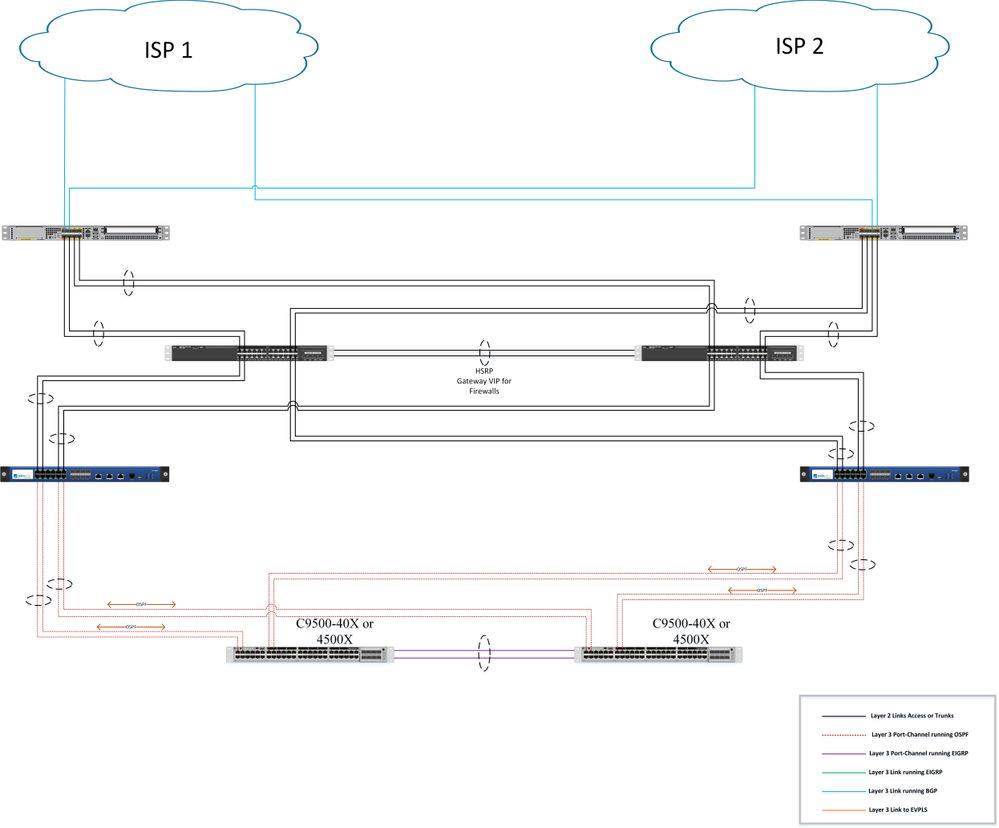
I was looking at some previous documents I had made and diagrams, and came across something similar.
I had three pairs of ASAs all connected to 3650s (3650s running HSRP)
The firewalls had the public block on the outside interface and was connected to access ports on the switches. The switches were running SVIs with a public IP that was essentially the gateways for the outside interfaces. Then we were running layer 3 links using private /30's to upstream edge routers. From ASA to switches to inside interfaces of edge routers we were running OSPF, then BGP from outside edge routers to ISP. Then there was BGP and OSPF redistribution.
Im going to have to drop these into UNL to see how it was working but I have the configs to look. So the NAT was being done on the firewall and OSPF and BGP were doing the routing and advertising of the public block. I think one thing we didn't do, which we should have was get our own Public block from ARIN. We were using the ISP's block and advertising each ISPs into each others BGP AS. I think we had to sign some papers for that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2017 12:09 PM
Just a recommendation, if you setup a public IP on your switch (don't know the reason behind it, why not just using at L2), don't forget to setup Hardening IOS config to protect it from outside.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2017 12:40 PM
@Francesco Molino wrote:
Then you were doing BGP for outside and OSPF inside :-) What I suggested you at the beginning and what it's done usually.
Just a recommendation, if you setup a public IP on your switch (don't know the reason behind it, why not just using at L2), don't forget to setup Hardening IOS config to protect it from outside.
Why would you not know the reason? The outside of the ASA needs to have the Public, so where would the gateways go?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2017 12:45 PM
Sorry I'm through my iphone and can't see really well the design.
You have a public IP on ASA outside and on your router right? If so, why adding a L3 on the switch, just acting as L2 would be fine.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 12:03 AM
1. If you are intent on using a dynamic routing protocol between the router and edge FW then OSPF is the way I would go for this. Just make sure that the router doesn't send the whole internet routing table to the edge FW, just the default route.
2. For this setup I would look into using redundant interfaces. Connect one link from each switch to each edge FW (active/standby). create redundant interface and associate each interface connected to the switches with the redundant interface (keep in mind that the first interface you associate with the redundant interface becomes the primary interface). then, if possible, have a physical link directly between the ASAs for failover link and state link. Now if one of the switches fail the redundant interfaces will use the link toward the second switch.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 05:52 AM
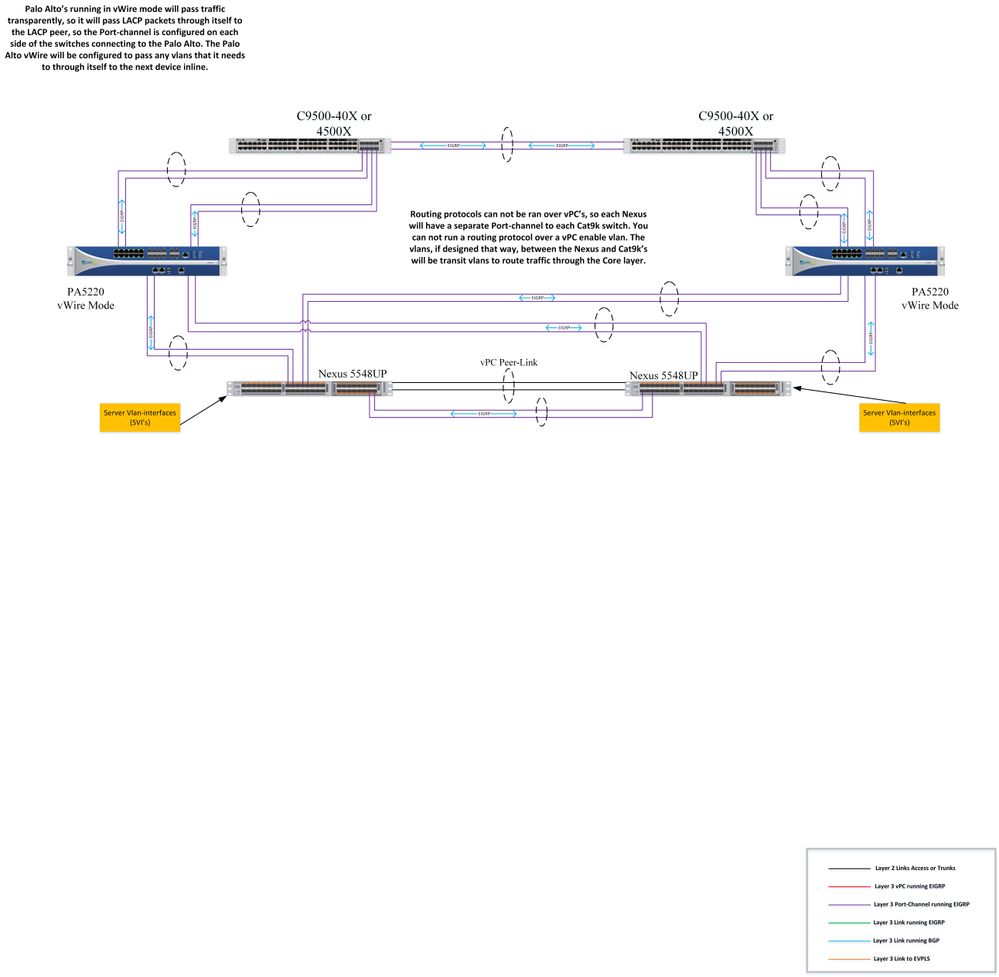
The Cat9ks are not running HSRP they are both actively forwarding traffic. They are running EIGRP southbound to a pair a Nexus 5ks (those are running active/active HSRP). Then the Cat9ks are running OSPF northbound to the firewall, the firewalls are running OSPF northbound to the edge routers. There is a paid of 3650s in between the Firewalls and the Edge routers, those are running HSRP and will be all layer 2 links.
No for the surprise....The edge firewalls are not ASA's. So this is why I am running OSPF.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 08:36 AM
For the Firewall edge routing, to control any routing attacks, I will use different protocols (1 for outside and 1 for inside). You can use BGP for outside and ospf for inside.
However, if your ISP is just sending a default route, there is no much to control and in that case you can decide if you want to go with static route.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 10:11 AM
Couldn't each link from each Cat9k terminating at the active PA be in the same zone?
I would run BGP from Edge Router to ISP, OSPF from edge router to firewalls.
The ISP will send me anything I want as long as I meet their hardware requirements, so shouldn't be an issue.
There is going to be a lot of redistribution for sure running all three primary routing protocols.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2017 10:26 AM
Yes on PA you can have all interfaces you want in the same zone. I was thinking about ASA when wrote the answer.
Ok for your routing protocol and you will have OSPF between edge and inside Core? within the same area?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide