- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD VPN site-to-site route FTD to remote LAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FDM VPN site-to-site route FTD to remote LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2019 05:02 AM - edited 08-15-2019 07:48 AM
I have setup a VPN site to site between 2 firewall.
On my site Y, public IP 210.666.111.7 with 1 local LAN (10.145.49.0/24) <--config is below
On my site Z, public IP 216.55.11.82 with 2 local LAN (10.83.132.0/24 and 10.83.138.0/24)
I am trying to route site Y LAN subnet to reach a server at site Z that has a server IP of 10.83.132.40.
At site Z I can reach site Y, local LAN (10.145.49.0/24).
At site Y I can not reach both of the site Z local LAN (10.83.132.0/24 and 10.83.138.0/24); to be able to establish a connection to create identity realm using AD directory service.
Tunnel is connected and working. Just missing, how to know to take the VPN connection at Site Y to connect to Site Z LAN (10.83.132.0/24 and 10.83.138.0/24)
site Y is using Firepower Device Manager and its config is : [IP Addresses do not identify the actual ones used ]
Any idea of how I must create my route.. NAT..OR Access List; whichever is required?
: Hardware: FPR-2110, 6843 MB RAM, CPU MIPS 1200 MHz, 1 CPU (6 cores) : NGFW Version 6.2.3 ! hostname firepower ! interface Ethernet1/1 nameif outside cts manual propagate sgt preserve-untag policy static sgt disabled trusted security-level 0 ip address 210.666.111.7 255.255.255.252 ! interface Ethernet1/2 nameif inside cts manual propagate sgt preserve-untag policy static sgt disabled trusted security-level 0 ip address 10.145.49.3 255.255.255.0 ! interface Ethernet1/3 shutdown no nameif no security-level no ip address ! interface Management1/1 management-only nameif diagnostic cts manual propagate sgt preserve-untag policy static sgt disabled trusted security-level 0 no ip address ! ftp mode passive ngips conn-match vlan-id object network USinternetAddresses subnet 216.55.11.0 255.255.255.0 object network US_Outside_FirePower_IP host 216.55.11.82 object network US_Vlan_600 subnet 10.83.138.0 255.255.255.0 object network any-ipv4 subnet 0.0.0.0 0.0.0.0 object network any-ipv6 subnet ::/0 object network default_inside_route host 10.145.49.1 object network 10.145_16 subnet 10.145.0.0 255.255.0.0 object network US_Vlan_14 subnet 10.83.132.0 255.255.255.0 object network INvlan200 subnet 10.145.49.0 255.255.255.0 object network OutsideIPv4Gateway host 210.666.111.1 object network OutsideIPv4DefaultRoute subnet 0.0.0.0 0.0.0.0 object-group network |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 network-object object 10.145_16 object-group network |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 network-object object US_Vlan_600 network-object object US_Vlan_14 access-list NGFW_ONBOX_ACL remark rule-id 268435458: ACCESS POLICY: NGFW_Access_Policy access-list NGFW_ONBOX_ACL remark rule-id 268435458: L5 RULE: US-to-India access-list NGFW_ONBOX_ACL advanced permit ip object USinternetAddresses ifc outside any rule-id 268435458 access-list NGFW_ONBOX_ACL remark rule-id 268435460: ACCESS POLICY: NGFW_Access_Policy access-list NGFW_ONBOX_ACL remark rule-id 268435460: L5 RULE: USvln14-0to-INvlan200 access-list NGFW_ONBOX_ACL advanced permit ip object US_Vlan_14 object INvlan200 rule-id 268435460 access-list NGFW_ONBOX_ACL advanced permit ip object US_Vlan_600 object INvlan200 rule-id 268435460 access-list NGFW_ONBOX_ACL remark rule-id 268435461: ACCESS POLICY: NGFW_Access_Policy access-list NGFW_ONBOX_ACL remark rule-id 268435461: L5 RULE: INvlan200-to-USvlan14 access-list NGFW_ONBOX_ACL advanced permit ip object INvlan200 object US_Vlan_14 rule-id 268435461 access-list NGFW_ONBOX_ACL advanced permit ip object INvlan200 object US_Vlan_600 rule-id 268435461 access-list NGFW_ONBOX_ACL remark rule-id 268435459: ACCESS POLICY: NGFW_Access_Policy access-list NGFW_ONBOX_ACL remark rule-id 268435459: L5 RULE: OutSide-to-any access-list NGFW_ONBOX_ACL advanced permit ip ifc outside any any rule-id 268435459 access-list NGFW_ONBOX_ACL remark rule-id 268435457: ACCESS POLICY: NGFW_Access_Policy access-list NGFW_ONBOX_ACL remark rule-id 268435457: L5 RULE: Inside_Outside_Rule access-list NGFW_ONBOX_ACL advanced trust ip ifc inside any ifc outside any rule-id 268435457 event-log both access-list NGFW_ONBOX_ACL remark rule-id 1: ACCESS POLICY: NGFW_Access_Policy access-list NGFW_ONBOX_ACL remark rule-id 1: L5 RULE: DefaultActionRule access-list NGFW_ONBOX_ACL advanced deny ip any any rule-id 1 access-list |s2sAcl|829f4535-aecf-11e9-b03c-d9fb9a86cd36 extended permit ip object-group |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 object-group |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 pager lines 24 logging enable logging timestamp logging console warnings mtu diagnostic 1500 mtu outside 1500 mtu inside 1500 no failover no monitor-interface service-module icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 no arp permit-nonconnected arp rate-limit 32768 nat (inside,outside) source static |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 destination static |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 no-proxy-arp route-lookup nat (inside,outside) source static 10.145_16 10.145_16 destination static Vlan_14 Vlan_14 ! nat (any,outside) after-auto source dynamic any-ipv4 interface access-group NGFW_ONBOX_ACL global route outside 0.0.0.0 0.0.0.0 210.666.111.1 1 route inside 10.145.0.0 255.255.0.0 10.145.49.1 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 timeout conn-holddown 0:00:15 timeout igp stale-route 0:01:10 user-identity default-domain LOCAL aaa authentication login-history http server enable http 0.0.0.0 0.0.0.0 inside http ::/0 inside ip-client diagnostic ipv6 ip-client diagnostic ip-client inside ipv6 ip-client inside ip-client outside ipv6 ip-client outside no snmp-server location no snmp-server contact sysopt connection tcpmss 0 crypto ipsec ikev2 ipsec-proposal VPN_IPSEC_PRO protocol esp encryption aes-gcm-256 protocol esp integrity null crypto ipsec security-association pmtu-aging infinite crypto map s2sCryptoMap 1 match address |s2sAcl|829f4535-aecf-11e9-b03c-d9fb9a86cd36 crypto map s2sCryptoMap 1 set peer 216.55.11.82 crypto map s2sCryptoMap 1 set ikev2 ipsec-proposal VPN_IPSEC_PRO crypto map s2sCryptoMap interface outside crypto ca trustpool policy crypto ikev2 policy 1 encryption aes-gcm-256 integrity null group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside crypto ikev1 policy 160 authentication pre-share encryption des hash sha group 5 lifetime 86400 telnet timeout 5 console timeout 0 dhcpd auto_config outside ! threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept group-policy |s2sGP|216.55.11.82 internal group-policy |s2sGP|216.55.11.82 attributes vpn-tunnel-protocol ikev2 dynamic-access-policy-record DfltAccessPolicy tunnel-group 216.55.11.82 type ipsec-l2l tunnel-group 216.55.11.82 general-attributes default-group-policy |s2sGP|216.55.11.82 tunnel-group 216.55.11.82 ipsec-attributes ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 no tcp-inspection policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect ip-options inspect icmp inspect icmp error ! service-policy global_policy global prompt hostname context app-agen heartbeat interval 1000 retry-count 3 snort preserve-connection Cryptochecksum:7bffc7f714679427fd4645c16fb65a91 : end
- Labels:
-
Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2019 05:12 AM - edited 08-15-2019 06:59 AM
Hi,
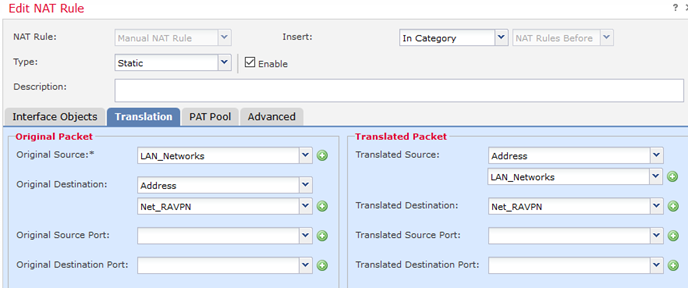
You'll need a NAT exemption rule. You need to ensure the original & translated source is INvlan200 and the original & translated destination is US_Vlan_14 (assuming those are the correct objects). Create another rule for the other objects, or reference a group containing all objects instead.
Here is a similar example:-
You will also need to ensure the Access Control Policy permits the traffic.
EDIT: Sorry, I wasn't as observant as @Rahul Govindan you seem to already have the NAT rule.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2019 05:17 AM
Your config looks correct. You have the right NAT, ACL and route,
object-group network |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 network-object object 10.145_16 object-group network |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 network-object object US_Vlan_600 network-object object US_Vlan_14
nat (inside,outside) source static |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 destination static |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 no-proxy-arp route-lookup
access-list |s2sAcl|829f4535-aecf-11e9-b03c-d9fb9a86cd36 extended permit ip object-group |s2sAclSrcNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36 object-group |s2sAclDestNwgV4|829f4535-aecf-11e9-b03c-d9fb9a86cd36
route outside 0.0.0.0 0.0.0.0 210.666.111.1 1
What about the other side? Do you have the config?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2019 07:25 AM - edited 08-15-2019 07:26 AM
Yeah, I have the config for The other side. It looks like this.
Thanks
: Saved : : Hardware: FPR-2110, 6843 MB RAM, CPU MIPS 1200 MHz, 1 CPU (6 cores) : NGFW Version 6.2.3.13 ! hostname firepower ! interface Ethernet1/1 description internet facing nameif WAN cts manual propagate sgt preserve-untag policy static sgt disabled trusted security-level 0 ip address 216.55.11.82 255.255.255.240 ! ! interface Management1/1 management-only nameif diagnostic cts manual propagate sgt preserve-untag policy static sgt disabled trusted security-level 0 no ip address ! ftp mode passive ngips conn-match vlan-id object network 10.83.138.0 subnet 10.83.138.0 255.255.255.0 object network VLAN_26 subnet 10.83.135.0 255.255.255.0 object network VLAN600 subnet 10.83.138.0 255.255.255.0 access-list CSM_FW_ACL_ remark rule-id 9998: PREFILTER POLICY: Default Tunnel and Priority Policy access-list CSM_FW_ACL_ remark rule-id 9998: RULE: DEFAULT TUNNEL ACTION RULE access-list CSM_FW_ACL_ advanced permit ipinip any any rule-id 9998 access-list CSM_FW_ACL_ advanced permit 41 any any rule-id 9998 access-list CSM_FW_ACL_ advanced permit gre any any rule-id 9998 access-list CSM_FW_ACL_ advanced permit udp any eq 3544 any range 1025 65535 rule-id 9998 access-list CSM_FW_ACL_ advanced permit udp any range 1025 65535 any eq 3544 rule-id 9998 access-list CSM_FW_ACL_ remark rule-id 268438531: ACCESS POLICY: US - Mandatory access-list CSM_FW_ACL_ remark rule-id 268438531: L7 RULE: DRvl37-to-VBvl600 access-list CSM_FW_ACL_ advanced permit ip ifc WAN object DRvlan37_52 object 10.83.138.0 rule-id 268438531 access-list CSM_FW_ACL_ remark rule-id 268438533: ACCESS POLICY: US - Mandatory access-list CSM_FW_ACL_ remark rule-id 268438533: L7 RULE: VLAN14-to-DRVL39 access-list CSM_FW_ACL_ advanced permit ip ifc WAN any ifc WAN any rule-id 268438533 access-list CSM_FW_ACL_ remark rule-id 268438530: ACCESS POLICY: US - Mandatory access-list CSM_FW_ACL_ remark rule-id 268438530: L7 RULE: VLAN26_TO_WAN access-list CSM_FW_ACL_ advanced permit ip ifc WAN any ifc VLAN_26 any rule-id 268438530 access-list CSM_FW_ACL_ advanced permit ip ifc VLAN_26 any ifc WAN any rule-id 268438530 access-list CSM_FW_ACL_ advanced permit ip ifc VLAN_26 any ifc VLAN_26 any rule-id 268438530 access-list CSM_FW_ACL_ remark rule-id 268436484: ACCESS POLICY: US - Default access-list CSM_FW_ACL_ remark rule-id 268436484: L4 RULE: DEFAULT ACTION RULE access-list CSM_FW_ACL_ advanced deny ip any any rule-id 268436484 event-log flow-start access-list VPN_IP_POOL standard permit 172.16.10.0 255.255.254.0 access-list AnyConnect_Split standard permit 10.83.138.0 255.255.255.0 access-list CSM_IPSEC_ACL_3 extended permit ip 10.83.138.0 255.255.255.0 10.145.0.0 255.255.0.0 access-list CSM_IPSEC_ACL_3 extended permit ip 10.83.132.0 255.255.255.0 10.145.0.0 255.255.0.0 ! tcp-map UM_STATIC_TCP_MAP tcp-options range 6 7 allow tcp-options range 9 18 allow tcp-options range 20 255 allow urgent-flag allow ! no pager logging list MANAGER_VPN_EVENT_LIST level errors class auth logging list MANAGER_VPN_EVENT_LIST level errors class vpn logging list MANAGER_VPN_EVENT_LIST level errors class vpnc logging list MANAGER_VPN_EVENT_LIST level errors class vpnfo logging list MANAGER_VPN_EVENT_LIST level errors class vpnlb logging list MANAGER_VPN_EVENT_LIST level errors class webfo logging list MANAGER_VPN_EVENT_LIST level errors class webvpn logging list MANAGER_VPN_EVENT_LIST level errors class ca logging list MANAGER_VPN_EVENT_LIST level errors class svc logging list MANAGER_VPN_EVENT_LIST level errors class ssl logging list MANAGER_VPN_EVENT_LIST level errors class dap logging list MANAGER_VPN_EVENT_LIST level errors class ipaa logging FMC MANAGER_VPN_EVENT_LIST no logging message 106015 no logging message 313001 no logging message 313008 no logging message 106023 no logging message 710003 no logging message 106100 no logging message 302015 no logging message 302014 no logging message 302013 no logging message 302018 no logging message 302017 no logging message 302016 no logging message 302021 no logging message 302020 mtu WAN 1500 mtu VLAN_26 1500 mtu VLAN_25 1500 mtu VLAN_800 1500 mtu VLAN_501 1500 mtu diagnostic 1500 failover failover lan unit secondary failover lan interface Sync_Link Ethernet1/11 failover replication http failover link Sync_Link Ethernet1/11 failover interface ip Sync_Link 10.10.10.1 255.255.255.0 standby 10.10.10.2 icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 no arp permit-nonconnected arp rate-limit 32768 access-group CSM_FW_ACL_ global route WAN 0.0.0.0 0.0.0.0 216.55.11.19 1 route WAN 10.145.49.0 255.255.255.0 210.666.111.1 1 route WAN 210.666.111.1 255.255.255.255 216.55.11.19 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:00:30 timeout floating-conn 0:00:00 timeout conn-holddown 0:00:15 timeout igp stale-route 0:01:10 aaa-server ad500-remote-access protocol ldap max-failed-attempts 4 realm-id 3 aaa-server ad500-remote-access host 10.83.138.30 server-port 389 ldap-base-dn DC=A,DC=net ldap-group-base-dn CN=Users,DC=A,DC=net ldap-scope subtree ldap-naming-attribute samaccountname ldap-login-password ***** ldap-login-dn vpn@a.net server-type microsoft aaa proxy-limit disable aaa authentication login-history no snmp-server location no snmp-server contact no snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart crypto ipsec ikev2 ipsec-proposal CSM_IP_1 protocol esp encryption aes-gcm-256 protocol esp integrity null crypto ipsec security-association pmtu-aging infinite crypto map CSM_WAN_map 1 match address CSM_IPSEC_ACL_2 crypto map CSM_WAN_map 1 set peer 147. crypto map CSM_WAN_map 1 set ikev2 ipsec-proposal CSM_IP_1 crypto map CSM_WAN_map 1 set reverse-route crypto map CSM_WAN_map 2 match address CSM_IPSEC_ACL_3 crypto map CSM_WAN_map 2 set peer 210.666.111.1 crypto map CSM_WAN_map 2 set ikev2 ipsec-proposal CSM_IP_1 crypto map CSM_WAN_map 2 set reverse-route crypto map CSM_WAN_map interface WAN crypto ca trustpoint r.a.net enrollment self subject-name CN=r.a.net keypair <Default-RSA-Key> ignore-ipsec-keyusage crl configure crypto ca trustpool policy crypto ca certificate chain r.a.net certificate 78631b5d quit crypto ikev2 policy 2 encryption aes-gcm-256 integrity null group 19 prf sha256 lifetime seconds 86400 crypto ikev2 policy 10 encryption aes-gcm-256 aes-gcm-192 aes-gcm integrity null group 21 20 19 14 5 prf sha512 sha384 sha256 sha lifetime seconds 86400 crypto ikev2 enable WAN crypto ikev1 am-disable telnet timeout 5 console timeout 0 ! tls-proxy maximum-session 1000 ! threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept ssl trust-point r.a.net webvpn enable WAN anyconnect image disk0:/csm/anyconnect-win-4.7.02036-webdeploy-k9.pkg 1 regex "Windows" anyconnect image disk0:/csm/anyconnect-linux64-4.7.02036-webdeploy-k9.pkg 2 regex "Linux" anyconnect image disk0:/csm/anyconnect-macos-4.7.02036-webdeploy-k9.pkg 3 regex "Mac OS" anyconnect enable tunnel-group-list enable cache no disable group-policy DfltGrpPolicy attributes vpn-tunnel-protocol ikev2 ssl-client user-authentication-idle-timeout none webvpn anyconnect keep-installer none anyconnect modules value dart anyconnect ask none default anyconnect http-comp none activex-relay disable file-entry disable file-browsing disable url-entry disable deny-message none group-policy RA_FullTunnel internal group-policy RA_FullTunnel attributes banner none wins-server none dns-server value 10.83.138.30 dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ikev2 ssl-client split-tunnel-policy tunnelall ipv6-split-tunnel-policy tunnelall split-tunnel-network-list none default-domain value A.net split-dns none split-tunnel-all-dns disable client-bypass-protocol disable vlan none address-pools value RemoteAccess-IP-Pool webvpn anyconnect ssl dtls enable anyconnect mtu 1406 anyconnect firewall-rule client-interface public none anyconnect firewall-rule client-interface private none anyconnect ssl keepalive 20 anyconnect ssl rekey time none anyconnect ssl rekey method none anyconnect dpd-interval client 30 anyconnect dpd-interval gateway 30 anyconnect ssl compression none anyconnect dtls compression none anyconnect modules value dart anyconnect ask none default anyconnect anyconnect ssl df-bit-ignore disable group-policy RA_SplitTunnel internal group-policy RA_SplitTunnel attributes banner none wins-server none dns-server value 10.83.138.30 dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ikev2 ssl-client split-tunnel-policy tunnelspecified ipv6-split-tunnel-policy tunnelall split-tunnel-network-list value AnyConnect_Split default-domain value AD500.net split-dns none split-tunnel-all-dns disable client-bypass-protocol disable vlan none address-pools value RemoteAccess-IP-Pool webvpn anyconnect ssl dtls enable anyconnect mtu 1406 anyconnect firewall-rule client-interface public none anyconnect firewall-rule client-interface private none anyconnect ssl keepalive 20 anyconnect ssl rekey time none anyconnect ssl rekey method none anyconnect dpd-interval client 30 anyconnect dpd-interval gateway 30 anyconnect ssl compression none anyconnect dtls compression none anyconnect modules value dart anyconnect ask none default anyconnect anyconnect ssl df-bit-ignore disable group-policy VPN_temp internal group-policy VPN_temp attributes banner value wt wins-server none dns-server value 10.83.138.30 dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified ipv6-split-tunnel-policy tunnelall split-tunnel-network-list value VPN_IP_POOL default-domain none split-dns none split-tunnel-all-dns disable client-bypass-protocol disable vlan none address-pools value RemoteAccess-IP-Pool webvpn anyconnect ssl dtls enable anyconnect mtu 1406 anyconnect firewall-rule client-interface public none anyconnect firewall-rule client-interface private none anyconnect ssl keepalive 20 anyconnect ssl rekey time none anyconnect ssl rekey method none anyconnect dpd-interval client 30 anyconnect dpd-interval gateway 30 anyconnect ssl compression none anyconnect dtls compression none anyconnect modules value dart anyconnect ask none default anyconnect anyconnect ssl df-bit-ignore disable group-policy .DefaultS2SGroupPolicy internal group-policy .DefaultS2SGroupPolicy attributes vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ikev1 ikev2 dynamic-access-policy-record DfltAccessPolicy tunnel-group 147. type ipsec-l2l tunnel-group 147. general-attributes default-group-policy .DefaultS2SGroupPolicy tunnel-group 147. ipsec-attributes ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** tunnel-group remote-Access type remote-access tunnel-group remote-Access general-attributes address-pool RemoteAccess-IP-Pool authentication-server-group a-remote-access default-group-policy RA_SplitTunnel tunnel-group remote-Access webvpn-attributes group-alias remote-Access enable tunnel-group 210.666.111.1 type ipsec-l2l tunnel-group 210.666.111.1 general-attributes default-group-policy .DefaultS2SGroupPolicy tunnel-group 210.666.111.1 ipsec-attributes ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 no tcp-inspection policy-map type inspect ip-options UM_STATIC_IP_OPTIONS_MAP parameters eool action allow nop action allow router-alert action allow policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect icmp inspect icmp error inspect ip-options UM_STATIC_IP_OPTIONS_MAP class class-default set connection advanced-options UM_STATIC_TCP_MAP ! service-policy global_policy global prompt hostname context call-home profile CiscoTAC-1 no active destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address email callhome@cisco.com destination transport-method http subscribe-to-alert-group diagnostic subscribe-to-alert-group environment subscribe-to-alert-group inventory periodic monthly subscribe-to-alert-group configuration periodic monthly subscribe-to-alert-group telemetry periodic daily app-agent heartbeat interval 1000 retry-count 3 snort preserve-connection Cryptochecksum:eeca95f4583f64f8693d6fd8a516e8e5 : end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2019 07:52 AM
Yeah, I have the config for The other side. It looks like this.
Thanks
: Saved : : Hardware: FPR-2110, 6843 MB RAM, CPU MIPS 1200 MHz, 1 CPU (6 cores) : NGFW Version 6.2.3.13 ! hostname firepower ! interface Ethernet1/1 description internet facing nameif WAN cts manual propagate sgt preserve-untag policy static sgt disabled trusted security-level 0 ip address 216.55.11.82 255.255.255.240 ! ! interface Management1/1 management-only nameif diagnostic cts manual propagate sgt preserve-untag policy static sgt disabled trusted security-level 0 no ip address ! ftp mode passive ngips conn-match vlan-id object network 10.83.138.0 subnet 10.83.138.0 255.255.255.0 object network VLAN_26 subnet 10.83.135.0 255.255.255.0 object network VLAN600 subnet 10.83.138.0 255.255.255.0 access-list CSM_FW_ACL_ remark rule-id 9998: PREFILTER POLICY: Default Tunnel and Priority Policy access-list CSM_FW_ACL_ remark rule-id 9998: RULE: DEFAULT TUNNEL ACTION RULE access-list CSM_FW_ACL_ advanced permit ipinip any any rule-id 9998 access-list CSM_FW_ACL_ advanced permit 41 any any rule-id 9998 access-list CSM_FW_ACL_ advanced permit gre any any rule-id 9998 access-list CSM_FW_ACL_ advanced permit udp any eq 3544 any range 1025 65535 rule-id 9998 access-list CSM_FW_ACL_ advanced permit udp any range 1025 65535 any eq 3544 rule-id 9998 access-list CSM_FW_ACL_ remark rule-id 268438531: ACCESS POLICY: US - Mandatory access-list CSM_FW_ACL_ remark rule-id 268438531: L7 RULE: DRvl37-to-VBvl600 access-list CSM_FW_ACL_ advanced permit ip ifc WAN object DRvlan37_52 object 10.83.138.0 rule-id 268438531 access-list CSM_FW_ACL_ remark rule-id 268438533: ACCESS POLICY: US - Mandatory access-list CSM_FW_ACL_ remark rule-id 268438533: L7 RULE: VLAN14-to-DRVL39 access-list CSM_FW_ACL_ advanced permit ip ifc WAN any ifc WAN any rule-id 268438533 access-list CSM_FW_ACL_ remark rule-id 268438530: ACCESS POLICY: US - Mandatory access-list CSM_FW_ACL_ remark rule-id 268438530: L7 RULE: VLAN26_TO_WAN access-list CSM_FW_ACL_ advanced permit ip ifc WAN any ifc VLAN_26 any rule-id 268438530 access-list CSM_FW_ACL_ advanced permit ip ifc VLAN_26 any ifc WAN any rule-id 268438530 access-list CSM_FW_ACL_ advanced permit ip ifc VLAN_26 any ifc VLAN_26 any rule-id 268438530 access-list CSM_FW_ACL_ remark rule-id 268436484: ACCESS POLICY: US - Default access-list CSM_FW_ACL_ remark rule-id 268436484: L4 RULE: DEFAULT ACTION RULE access-list CSM_FW_ACL_ advanced deny ip any any rule-id 268436484 event-log flow-start access-list VPN_IP_POOL standard permit 172.16.10.0 255.255.254.0 access-list AnyConnect_Split standard permit 10.83.138.0 255.255.255.0 access-list CSM_IPSEC_ACL_3 extended permit ip 10.83.138.0 255.255.255.0 10.145.0.0 255.255.0.0 access-list CSM_IPSEC_ACL_3 extended permit ip 10.83.132.0 255.255.255.0 10.145.0.0 255.255.0.0 ! tcp-map UM_STATIC_TCP_MAP tcp-options range 6 7 allow tcp-options range 9 18 allow tcp-options range 20 255 allow urgent-flag allow ! no pager logging list MANAGER_VPN_EVENT_LIST level errors class auth logging list MANAGER_VPN_EVENT_LIST level errors class vpn logging list MANAGER_VPN_EVENT_LIST level errors class vpnc logging list MANAGER_VPN_EVENT_LIST level errors class vpnfo logging list MANAGER_VPN_EVENT_LIST level errors class vpnlb logging list MANAGER_VPN_EVENT_LIST level errors class webfo logging list MANAGER_VPN_EVENT_LIST level errors class webvpn logging list MANAGER_VPN_EVENT_LIST level errors class ca logging list MANAGER_VPN_EVENT_LIST level errors class svc logging list MANAGER_VPN_EVENT_LIST level errors class ssl logging list MANAGER_VPN_EVENT_LIST level errors class dap logging list MANAGER_VPN_EVENT_LIST level errors class ipaa logging FMC MANAGER_VPN_EVENT_LIST no logging message 106015 no logging message 313001 no logging message 313008 no logging message 106023 no logging message 710003 no logging message 106100 no logging message 302015 no logging message 302014 no logging message 302013 no logging message 302018 no logging message 302017 no logging message 302016 no logging message 302021 no logging message 302020 mtu WAN 1500 mtu VLAN_26 1500 mtu VLAN_25 1500 mtu VLAN_800 1500 mtu VLAN_501 1500 mtu diagnostic 1500 failover failover lan unit secondary failover lan interface Sync_Link Ethernet1/11 failover replication http failover link Sync_Link Ethernet1/11 failover interface ip Sync_Link 10.10.10.1 255.255.255.0 standby 10.10.10.2 icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 no arp permit-nonconnected arp rate-limit 32768 access-group CSM_FW_ACL_ global route WAN 0.0.0.0 0.0.0.0 216.55.11.19 1 route WAN 10.145.49.0 255.255.255.0 210.666.111.1 1 route WAN 210.666.111.1 255.255.255.255 216.55.11.19 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:00:30 timeout floating-conn 0:00:00 timeout conn-holddown 0:00:15 timeout igp stale-route 0:01:10 aaa-server a-remote-access protocol ldap max-failed-attempts 4 realm-id 3 aaa-server a-remote-access host 10.83.138.30 server-port 389 ldap-base-dn DC=A,DC=net ldap-group-base-dn CN=Users,DC=A,DC=net ldap-scope subtree ldap-naming-attribute samaccountname ldap-login-password ***** ldap-login-dn vpn@a.net server-type microsoft aaa proxy-limit disable aaa authentication login-history no snmp-server location no snmp-server contact no snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart crypto ipsec ikev2 ipsec-proposal CSM_IP_1 protocol esp encryption aes-gcm-256 protocol esp integrity null crypto ipsec security-association pmtu-aging infinite crypto map CSM_WAN_map 1 match address CSM_IPSEC_ACL_2 crypto map CSM_WAN_map 1 set peer 147. crypto map CSM_WAN_map 1 set ikev2 ipsec-proposal CSM_IP_1 crypto map CSM_WAN_map 1 set reverse-route crypto map CSM_WAN_map 2 match address CSM_IPSEC_ACL_3 crypto map CSM_WAN_map 2 set peer 210.666.111.1 crypto map CSM_WAN_map 2 set ikev2 ipsec-proposal CSM_IP_1 crypto map CSM_WAN_map 2 set reverse-route crypto map CSM_WAN_map interface WAN crypto ca trustpoint r.a.net enrollment self subject-name CN=r.a.net keypair <Default-RSA-Key> ignore-ipsec-keyusage crl configure crypto ca trustpool policy crypto ca certificate chain r.a.net certificate 78631b5d quit crypto ikev2 policy 2 encryption aes-gcm-256 integrity null group 19 prf sha256 lifetime seconds 86400 crypto ikev2 policy 10 encryption aes-gcm-256 aes-gcm-192 aes-gcm integrity null group 21 20 19 14 5 prf sha512 sha384 sha256 sha lifetime seconds 86400 crypto ikev2 enable WAN crypto ikev1 am-disable telnet timeout 5 console timeout 0 ! tls-proxy maximum-session 1000 ! threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept ssl trust-point r.a.net webvpn enable WAN anyconnect image disk0:/csm/anyconnect-win-4.7.02036-webdeploy-k9.pkg 1 regex "Windows" anyconnect image disk0:/csm/anyconnect-linux64-4.7.02036-webdeploy-k9.pkg 2 regex "Linux" anyconnect image disk0:/csm/anyconnect-macos-4.7.02036-webdeploy-k9.pkg 3 regex "Mac OS" anyconnect enable tunnel-group-list enable cache no disable group-policy DfltGrpPolicy attributes vpn-tunnel-protocol ikev2 ssl-client user-authentication-idle-timeout none webvpn anyconnect keep-installer none anyconnect modules value dart anyconnect ask none default anyconnect http-comp none activex-relay disable file-entry disable file-browsing disable url-entry disable deny-message none group-policy RA_FullTunnel internal group-policy RA_FullTunnel attributes banner none wins-server none dns-server value 10.83.138.30 dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ikev2 ssl-client split-tunnel-policy tunnelall ipv6-split-tunnel-policy tunnelall split-tunnel-network-list none default-domain value A.net split-dns none split-tunnel-all-dns disable client-bypass-protocol disable vlan none address-pools value RemoteAccess-IP-Pool webvpn anyconnect ssl dtls enable anyconnect mtu 1406 anyconnect firewall-rule client-interface public none anyconnect firewall-rule client-interface private none anyconnect ssl keepalive 20 anyconnect ssl rekey time none anyconnect ssl rekey method none anyconnect dpd-interval client 30 anyconnect dpd-interval gateway 30 anyconnect ssl compression none anyconnect dtls compression none anyconnect modules value dart anyconnect ask none default anyconnect anyconnect ssl df-bit-ignore disable group-policy RA_SplitTunnel internal group-policy RA_SplitTunnel attributes banner none wins-server none dns-server value 10.83.138.30 dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ikev2 ssl-client split-tunnel-policy tunnelspecified ipv6-split-tunnel-policy tunnelall split-tunnel-network-list value AnyConnect_Split default-domain value A.net split-dns none split-tunnel-all-dns disable client-bypass-protocol disable vlan none address-pools value RemoteAccess-IP-Pool webvpn anyconnect ssl dtls enable anyconnect mtu 1406 anyconnect firewall-rule client-interface public none anyconnect firewall-rule client-interface private none anyconnect ssl keepalive 20 anyconnect ssl rekey time none anyconnect ssl rekey method none anyconnect dpd-interval client 30 anyconnect dpd-interval gateway 30 anyconnect ssl compression none anyconnect dtls compression none anyconnect modules value dart anyconnect ask none default anyconnect anyconnect ssl df-bit-ignore disable group-policy VPN_temp internal group-policy VPN_temp attributes banner value wt wins-server none dns-server value 10.83.138.30 dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified ipv6-split-tunnel-policy tunnelall split-tunnel-network-list value VPN_IP_POOL default-domain none split-dns none split-tunnel-all-dns disable client-bypass-protocol disable vlan none address-pools value RemoteAccess-IP-Pool webvpn anyconnect ssl dtls enable anyconnect mtu 1406 anyconnect firewall-rule client-interface public none anyconnect firewall-rule client-interface private none anyconnect ssl keepalive 20 anyconnect ssl rekey time none anyconnect ssl rekey method none anyconnect dpd-interval client 30 anyconnect dpd-interval gateway 30 anyconnect ssl compression none anyconnect dtls compression none anyconnect modules value dart anyconnect ask none default anyconnect anyconnect ssl df-bit-ignore disable group-policy .DefaultS2SGroupPolicy internal group-policy .DefaultS2SGroupPolicy attributes vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ikev1 ikev2 dynamic-access-policy-record DfltAccessPolicy tunnel-group 147. type ipsec-l2l tunnel-group 147. general-attributes default-group-policy .DefaultS2SGroupPolicy tunnel-group 147. ipsec-attributes ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** tunnel-group remote-Access type remote-access tunnel-group remote-Access general-attributes address-pool RemoteAccess-IP-Pool authentication-server-group a-remote-access default-group-policy RA_SplitTunnel tunnel-group remote-Access webvpn-attributes group-alias remote-Access enable tunnel-group 210.666.111.1 type ipsec-l2l tunnel-group 210.666.111.1 general-attributes default-group-policy .DefaultS2SGroupPolicy tunnel-group 210.666.111.1 ipsec-attributes ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 no tcp-inspection policy-map type inspect ip-options UM_STATIC_IP_OPTIONS_MAP parameters eool action allow nop action allow router-alert action allow policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect icmp inspect icmp error inspect ip-options UM_STATIC_IP_OPTIONS_MAP class class-default set connection advanced-options UM_STATIC_TCP_MAP ! service-policy global_policy global prompt hostname context call-home profile CiscoTAC-1 no active destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address email callhome@cisco.com destination transport-method http subscribe-to-alert-group diagnostic subscribe-to-alert-group environment subscribe-to-alert-group inventory periodic monthly subscribe-to-alert-group configuration periodic monthly subscribe-to-alert-group telemetry periodic daily app-agent heartbeat interval 1000 retry-count 3 snort preserve-connection Cryptochecksum:eeca95f4583f64f8693d6fd8a516e8e5 : end
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: