- Cisco Community
- Technology and Support
- Security
- Network Security
- FMC and FTD, a block rule ALLOWS data to flow?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 08:34 PM - edited 02-21-2020 07:37 AM
I am running FMC to administer an FTD 5508. Both have version 6.2.21 of thier respective software.
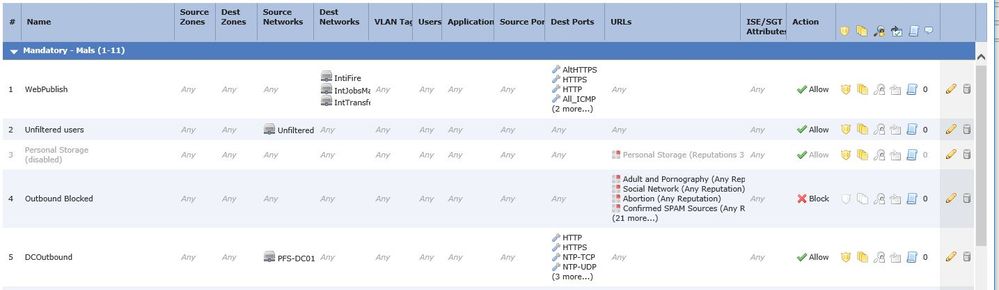
I have a rule set up as pictured below, rule4 Outbound Blocked. Idea is for it to block some "non business" sites. I expected the rule evaluation logic to do the following:
1. Evaluate each rule in order.
2. When evaluating rule4:
If a match occurs, deny the packet, and stop processing further rules.
If a match does not occur, move onto the next rule.
Oddly to me, it seems that rule4 is ALLOWING through at least some traffic that does not match the rule. Specifically, rule4 is allowing SMTP traffic, on TCP port 25 through. The behaviour I expected was for this rule to only ever block traffic, not to let anything ever pass though it, regardless of if it matched or not.
Am I misunderstanding how the logic here should operate? Does a block rule allow anything that does not match or something?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 12:54 PM
The problem here is time it takes for the evaluation. The firewall does not want to block all traffic until the evaluation is made. Your case should be easily fixed by re-ordering the rules. Cisco TAC generally recommends the Application and URL rules to be placed after the L3/L4 rules. So If you are really blocking that specific traffic below, that rule should be above this rule to block URL's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 09:42 PM
This might because URL filtering takes a few packets to start filtering urls. Till then, if all other conditions match (in your case is any any), it allows to go through so that the identification can complete. Documented below:
If early traffic matches all other rule conditions but identification is incomplete, the system allows the packet to pass and the connection to be established (or the SSL handshake to complete). After the system completes its identification, the system applies the appropriate rule action to the remaining session traffic.
Try adding ports to your url filtering rules to match http/https traffic only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 10:14 PM
The firewall is not just allowing the first few packets, it allows at least dozens. Any traffic on port 25 at least is passed.
I have now added HTTP and HTTPS as destination ports, and this seems to stop this behaviour. It also means that questionable websites on port 8080 or 88 or 8000 or 8008 or 591 or 4433 or whatever are not blocked. Proxies often use these ports, and the most dodgy sites could use ANY port. I would rather traffic to those destinations on ANY port was blocked, and the rest left for evaluation by other rules.
Is the behaviour I am seemng how the firewall is supposed to work? To my way of thinking, a BLOCK rule should; either cause no more rules to be evaluated, OR allow the next rule to be examined; I cannot understand the logic behind a block rule allowing traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 12:54 PM
The problem here is time it takes for the evaluation. The firewall does not want to block all traffic until the evaluation is made. Your case should be easily fixed by re-ordering the rules. Cisco TAC generally recommends the Application and URL rules to be placed after the L3/L4 rules. So If you are really blocking that specific traffic below, that rule should be above this rule to block URL's.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: