- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD access policy unexpected beheviour after applying a rule to block Teamviewer Application.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FTD access policy unexpected beheviour after applying a rule to block Teamviewer Application.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2019 06:34 PM
Hi, experts.
After applying in the FTD a rule to block the Teamviewer application for the internal hosts to internet (INSIDE to OUTSIDE),
I found in LINA this:
FTD-5516X-XXX# show access-list CSM_FW_ACL_ | i 268434489
access-list CSM_FW_ACL_ line 219 remark rule-id 268434489: ACCESS POLICY: ACP-XXX - Mandatory
access-list CSM_FW_ACL_ line 220 remark rule-id 268434489: L7 RULE: BLOCK TEAM VIEWER
access-list CSM_FW_ACL_ line 221 advanced permit ip ifc INSIDE any ifc OUTSIDE any rule-id 268434489 (hitcnt=514521) 0x38d32427
The application has been blocked but is allowing everything from INSIDE to OUTSIDE (when application is not matching).
Is normal this behaviour or what can I do to avoid that rule not allow the traffic in line 221 ?
Regards.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2019 04:45 AM
What is the default action of the policy? (shown here in my firepower management center)
It should be set to "Block", I think yours might be "allow"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2019 06:33 AM
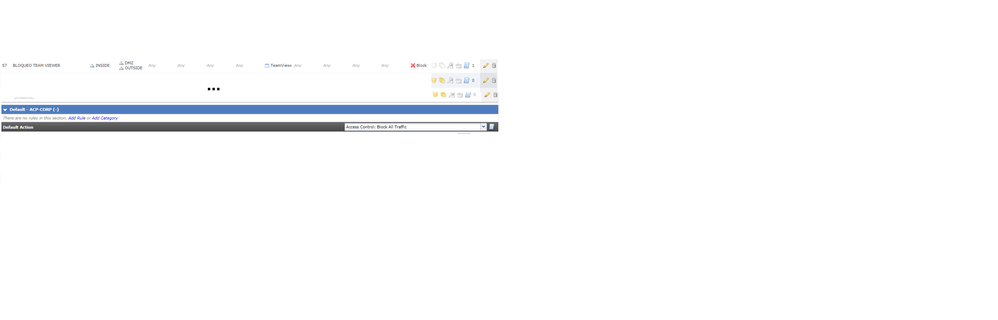
The default action is se to block all. See image. A default action set to other must add: permit ip any any (without zones).
Note the rule blocking the Application (Teamviewer in this case) is adding the permit action.
As a workaround I am looking to define a specific protocol in the same rule (for example icmp echo) and it is working (it adds only icmp echo). But this is a rare the behaviour, don´t think so ? There must be a better way to tune this.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide