- Cisco Community
- Technology and Support
- Security
- Network Security
- FTD External Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2017 03:17 PM - edited 03-12-2019 02:09 AM
I cannot find a way to get external authentication methods to work for the management interface of a Firepower Threat Defense system. In an FMC Platform Settings policy for device type "Firepower" there is an option to enable external authentication generally and for the shell specifically. However, there is no corresponding option in the policy settings for a device type "Threat Defense". In the manual (Firepower Management Center Configuration Guide, Version 6.2), I found this stated:
• SSH local users can only be configured at the CLI using the configure user add command. By default,
there is an admin user for which you configured the password during initial setup.
Does this mean that externally authenticated users cannot use an FTD CLI, or am I missing something?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2017 12:47 AM
As far as I know, that feature is not currently available on the FTD devices.
I've heard talk of adding it but no committed time frame or release at this point.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2017 12:47 AM
As far as I know, that feature is not currently available on the FTD devices.
I've heard talk of adding it but no committed time frame or release at this point.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2018 12:14 PM
supposedly 6.2.3 code fixed this and it even says "only available for 6.2.3 devices" in the platform external configuration tab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2018 04:08 AM
Is this now available? I'm running 6.2.3.3 on a 2110 and trying to get external (ldap) authentication work for cli access to the ftd which is managed via fmc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2018 04:11 AM
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2018 05:07 AM
I can't seem to get this working. I setup and tested the External Auth Server under Platform Settings > Platform Policy > External Authentication > Manage External Authentication Server, which is using LDAP as Auth Method and Encryption is SSL set under Advanced Options. Testing with my account is successful.
After the external auth server is setup, back under Platform Settings > Platform Policy > External Authentication > you are suppose to hit refesh button and I guess you are suppose to see the external auth server object you just created listed but I don't, still show not records to display.
The document states "For LDAP when you specify SSL or TLS encryption, you must upload a certificate for the connection; otherwise, the server will not be listed on this tab."
The document states
"For LDAP when you specify SSL or TLS encryption, you must upload a certificate for the connection; otherwise, the server will not be listed on this tab."
Not sure where this certificate needs to uploaded for the FTD device. I have a cert uploaded for the FMC for HTTPS access.
What do I need to do to get this working?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2018 03:27 PM - edited 11-08-2018 03:34 PM
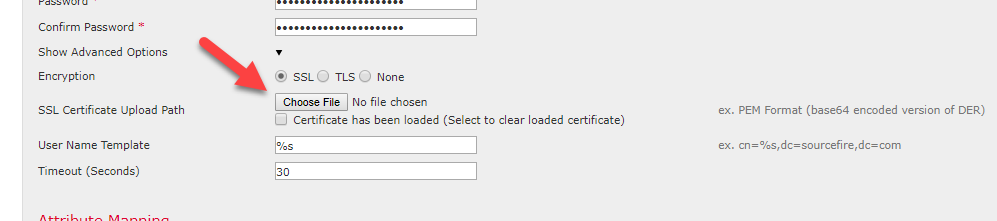
On the External Authentication Object page, go to Show Advanced Options and you will find the above button to upload the LDAPS CA certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2023 08:33 PM - edited 06-19-2023 09:21 PM
I actually dont think i've ever got it to work in multiple deployments, ive set it up exactly as you have above, i however get the server listed, its enabled but when i try SSH into the device i get "permission denied".
FTD logs:
2023-06-20T03:45:59.154931+00:00 <hostname>.dcp.local : Jun 20 03:45:59 UTC: %FTD-sys-5-199017: sshd[38665]: Invalid user <user-name> from <mgmt_host_ip> port 37758#012
2023-06-20T03:46:02.835086+00:00 <hostname>.dcp.local : Jun 20 03:46:02 UTC: %FTD-sys-5-199017: sshd[38665]: pam_tally(sshd:auth): pam_get_uid; no such user#012
2023-06-20T03:46:02.835367+00:00 <hostname>.dcp.local : Jun 20 03:46:02 UTC: %FTD-sys-5-199017: sshd[38665]: pam_unix(sshd:auth): check pass; user unknown#012
2023-06-20T03:46:02.835470+00:00 <hostname>.dcp.local : Jun 20 03:46:02 UTC: %FTD-sys-5-199017: sshd[38665]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=<mgmt_host_ip> #012
2023-06-20T03:46:02.843674+00:00 <hostname>.dcp.local : Jun 20 03:46:02 UTC: %FTD-sys-5-199017: sshd[38665]: pam_ldap: error trying to bind as user "uid=<user-name>,cn=users,cn=accounts,dc=dcp,dc=local" (Invalid credentials)#012
2023-06-20T03:46:05.089077+00:00 <hostname>.dcp.local : Jun 20 03:46:05 UTC: %FTD-sys-5-199017: sshd[38665]: Failed password for invalid user <user-name> from <mgmt_host_ip> port 37758 ssh2#012
i can log in to the FMC, membership group is the same for FTD and FMC. not sure what im missing here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2023 07:00 AM
Please use this post of mine as a reference guide and see if it helps:
https://bluenetsec.com/fmc-external-authentication-with-radius/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2023 11:10 PM
Hi Aref,
Whilst I appreciate you trying to assist me, the reference guide you've linked doesn't in any way replicate the environment we have and also doesn't touch on the main issue of not being able to authenticate to the FTDs
Will
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2023 02:53 AM
Hi Will, apologies if I am missing anything. If you are getting the permission denies when you are trying to SSH into the FTDs, then that potentially would be due to incorrect settings in the external authentication object. In the link I shared it is showing how the FTD CLI would need to be configured to allow some of the admins to log into the FTDs CLI. Could you please share the configs you applied and elaborate a little bit more about the issues you are experiencing with these accesses?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: