- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD Management Access Restriction does not work for Management interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FTD Management Access Restriction does not work for Management interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 07:52 PM - edited 02-21-2020 08:40 AM
I have been investigating how to restrict administrative access to FTD firewalls. Our corporate policy requires that we:
1) Enable SSH with Radius Authentication
2) Restrict IP address which can connect to the firewall.
When you install FTD on a ASA firewall the Management interface of the ASA is used by firepower module. This is the interface which is used for the FMC to connect to the firewall. Once the device is managed by an FMC the management interface is not available in the list of interfaces available on the device.
Below given is the document which explains how to enable radius authentication for ssh access to the FTD firewall.
However, the problem here is you can only enable and lock down access to interfaces which are available in the FMC. The management interface is not available in the configuration for modification. This means, I can use an in-line interface for SSH but I have no way of securing the access to the Management Interface itself. I opened a TAC case for this and they said there is no way to lock down the Management interface with radius authentication and you will have to use a local account to log in.
I am still not convinced. I think there should be SOME way to lock access to the management interface on the device itself. It would be pretty lame for a next generation security product not to have that feature.
Has anyone had much experience around this issue ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 07:01 PM
NGFW is not so next generation as it appears and this is not configurable AFAIK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 12:03 AM - edited 01-18-2019 12:10 AM
To restrict access to the FMC go to System > Configuration > Access List and enter the desired IPs or subnets that are to access the FMC.
To configure ssh access on the FTD CLI log in to the CLI and issue the command configure ssh-access-list 192.168.1.0/24 if you want to allow access from the 192.168.1.0/24 network. Keep in mind that you should also include the FMC IP or subnet in this list as this interface is used to register the FTD to FMC.
To configure access restriction on FXOS, log in to FXOS GUI and go to Platform Settings > Access List.
By default there are no access restrictions to any of these.
When doing this I suggest that you have physical access to the devices incase you lose connectivity, then you can console into the devices.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2019 01:43 AM
it only allow me to enter one ACL at the cli when i use the command and if I try to enter antoher acl it overwrite the existing?
Please can someone help how to enter multiple acl using cli command configure ssh-acl ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2019 01:52 AM
I suggest that you open a new post as this is a very old post and we do not have a detailed description of your problem. So please open a new post and be as detailed as possible when you describe the issue you are facing.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2019 01:54 AM
well asked very simple question related to above post anyway will open the new ticket.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2019 01:16 AM
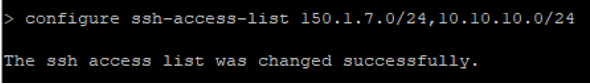
Please use comma without space between the objects. Please refer attached screenshot.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: