- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: How to generate a CSR and install a certificate on an FTD device.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2017 07:07 PM - edited 02-21-2020 06:18 AM
I have an ASA-5508-X, running FTD, controlled by a vFMC device. Both are running 6.2.2 software. It is partly implemented.
I want to set this up to serve Anyconnect clients, and I want SSL inspection. My understanding is that both of these things will require a certificate on the 5508. Since some client machines will be BYOD devices, I want a certificate that is trusted without any configuration on the client machines.
I want to generate a Certificate Signing Request, send it off to a public CA, (Godaddy or Comodo or whatever) then install the certificate on the 5508. I cannot, however, figure out how to generate the CSR. Am I missing something really obvious here?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2017 11:12 PM
You're welcome.
1. Almost all of the engineers whom I know and the bulk of examples on the Internet use the open source tool "openssl"to create CSRs. It is available for all Linux distributions as well as Windows and OS X. the syntax can be a bit challenging but nothing a quick search can't turn up multiple examples to work from. I have found the following site to be useful when crafting CSRs on the fly:
https://www.digicert.com/easy-csr/openssl.htm
2. You can exercise all of the licenses you mentioned on unencrypted traffic as-is. If you want to open up and inspect encrytped traffic (such as transported within SSL/TLS) then you need to act as a "man in the middle" of the otherwise end-to-end secured traffic stream. That requires you have a certificate that the client trusts to act on behalf of the site they are going to. Not all client appliactions will allow that (see "certificate pinning") and even if they do it may not always be advisable for you to do so (performance impact, legal and privacy concerns, etc.).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2017 07:49 PM - edited 09-14-2017 07:50 PM
To use a certificate to identify the FTD device, you need to add a Cert Enrollment object (Objects > PKI > Cert enrollment) in Firepower Management Center.
When using an external CA, you currently (as of FMC 6.2.2.) need to add it using the PKCS12 or SCEP methods. PKCS12 is applicable for most public CA use cases. In the case of PKCS12 you have to create the CSR externally (e.g. using OpenSSL). That will allow you to have the private key, CSR and eventually the signed certificate as separate files. You then combine the key and certificate into a PKCS12 and add it to the FMC. Once you have that object you can use it in your remote access VPN wizard and bind it to the interface that the remote users use. I've done that for my FTD device and it works fine.
That covers the VPN use case. If by SSL inspection you mean decryption, that cannot be done for general use cases (i.e. inspecting outbound SSL traffic) using a public CA-issued certificate. The certificate needs to be able to decrypt and re-sign and that can only be done using an internal PKI. If you want to do it only for selected servers that you own and have the private key and certificate for then you can do it for incoming SSL traffic. You do that with an SSL policy applied only to those specific servers under your control.
Also be advised that SSL decryption is currently done in software and doing so has a significant performance impact (70-80% throughput degradation for the decrypted traffic). You would not typically want to do that on a lower end appliance like the ASA 5508-X.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2017 09:25 PM
Thanks,that clarifies a few things, while opening up more questions.
1. Can you give me a link somewhere to instructions on how to "create the CSR externally"? I have installed certificates and many devices and systesm, but have always generated the CSR on the target device, copied it, then downloaded and installed the supplied certificate bundle.
2. I am still a little confused about the need for a certificate and how it relates to SSL decryption. We have licenses on this device for Threat, Malware and URL filtering, we want to inspect and flter traffic where internal users are browsing websites. Does this work only if we have a PKI set up? Does it require a certificate at all?
The connnection at our head office is a 50/50 fibre, so I am counting on the 5508 to be able to handle that load without a significant problem, even in a worst case scenario.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2017 11:12 PM
You're welcome.
1. Almost all of the engineers whom I know and the bulk of examples on the Internet use the open source tool "openssl"to create CSRs. It is available for all Linux distributions as well as Windows and OS X. the syntax can be a bit challenging but nothing a quick search can't turn up multiple examples to work from. I have found the following site to be useful when crafting CSRs on the fly:
https://www.digicert.com/easy-csr/openssl.htm
2. You can exercise all of the licenses you mentioned on unencrypted traffic as-is. If you want to open up and inspect encrytped traffic (such as transported within SSL/TLS) then you need to act as a "man in the middle" of the otherwise end-to-end secured traffic stream. That requires you have a certificate that the client trusts to act on behalf of the site they are going to. Not all client appliactions will allow that (see "certificate pinning") and even if they do it may not always be advisable for you to do so (performance impact, legal and privacy concerns, etc.).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2017 05:47 PM
Is it possible to use a wildcard cert on FTDs?
Thank you,
Deb
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2017 07:32 PM
@ciscotac16 wrote:
Is it possible to use a wildcard cert on FTDs?
It depends what context you are asking about.
For the Web UI of FMC you can certainly use a wildcard certificate. I have done several and that is no problem.
For the purposes of SSL decrypt and resign of outbound traffic , generally you want a special certificate (not a wildcard) that has been generated from your internal PKI and is itself a certificate-signing certificate. There's usually no good reason to use a wildcard in that case (an d arguably reasons not to do so).
For purposes of decrypting and inspecting traffic to an internally hosted server, you use whatever certificate that server uses (along with its private key).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2017 12:50 PM
Hi, Marvin. Thanks for the reply.
We need the certs for identity only (no SSL/TLS decryption). We are going to run two x 2110s in HA, managed by an FPMC.
Each FTD has to have its own unique name, such as ftd1.<domain name>.com, and ftd2.<domain name>.com. Also we would like for users to be able to connect to something else like vpn.<domain name>.com (so that it works for users connecting remotely whether or not there's been a failover).
I confirmed this morning with Cisco TAC that wildcard certs will work for this scenario. However, I'm wondering if certs with SANs would also work (less expensive).
If certs with SANs would work, we are thinking that we could get just one new cert that had the names of both FTDs in it, as well as the general remote access name.
Thanks for your time and sharing of expertise!
Deb
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2017 07:35 PM
OK, I understand better what you're asking now. For your 2110 hardware chassis itself (i.e. the physical management interface), its certificate is managed via the FX-OS cli.
I don't have an FCM handy to check but I'm not sure all the certificate operations for the chassis are exposed in the Firepower Chassis Manager (FCM) GUI.
Note that the FCM certificate is only used when admins access the chassis GUI - something that should be relatively infrequent and might not require use of a public CA-signed certificate. In my lab, for instance, I use a Windows Server 2016-based CA which I trust to issue certificates to all of my appliances.
For the remote access SSL VPN on the FTD pair, that certificate is managed by the Firepower Management Center. For that service, which is exposed to end users, using a public-CA signed certificate is definitely recommended.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2018 05:50 PM
Marvin did you have to create a different template for the FMC to accept your certificates?
I'm trying to figure out the ISE integratin, but it requires a FMC certificate. I'm guessing I'll have to go the openssl route so I have a private key, but I also get a invalid cert error when trying to use the CSR method for the FMC SSL cert for admin access. Not helpful at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 03:18 AM
The server template I have on my Windows Server 2016 CA worked fine for my FMC. I did build that template using some guidance from my friend Steve McNutt in his "PKI for Network Engineers" series:
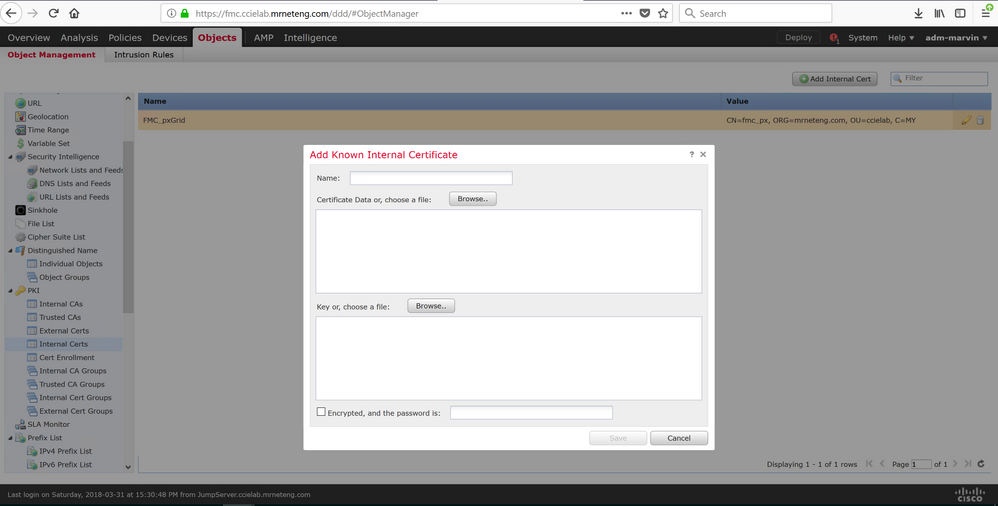
Once you have a good CA to use, you can use tools like OpenSSL for products such as FMC that don't have a good built-in mechanism to generate a CSR. Create a CSR in OpenSSL and then use the generated private key and CA-signed certificate to upload into FMC as shown below:
I did that and pxGrid to ISE works just fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 12:32 PM
I've found this step-by-step video.
This CSR approach do not require openssl.
https://youtu.be/DYhxjg47NqM?t=555
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 07:14 PM
That's a great link. Thanks for sharing.
FTI you can also use the open source Windows-based tool XCA for certificate management (CSR creation, key management etc.). I find it a lot more user-friendly than using OpenSSL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2019 01:42 PM
can we use wild card certificate for pxgride and firepower integrating
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2019 09:07 PM
The pxGrid certificate must be both a client and server certificate. Most wildcard certificates don't generally have both of those attributes. If yours does, then you should be able to use it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2022 01:57 PM - edited 10-06-2022 02:04 PM
Does this still apply? How is generating CSR this way different from what's documented here? https://www.cisco.com/c/en/us/support/docs/network-management/remote-access/212424-anyconnect-remote-access-vpn-configurati.html#anc3
If we know the CA root CA, can we follow this approach to download the CSR?
https://www.youtube.com/watch?v=ZZRVAFcSZCA&t=481s&ab_channel=CiscoCommunity
Does any new documentation show the cli/openssl approach? I can't seem to find it.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: